So far two Telegram bots called SMSRanger and BloodOTPbot have been found taking part in this malicious campaign.
Intel 471 researchers report that Telegram-powered bots are the hot favorites of threat actors as this helps them steal Telegram’s one-time passwords (OTPs) required on the 2FA (two-factor authentication) security process.
SEE: Hackers selling sensitive data from OTP generating firm
Researchers noted that there had been a sudden ‘uptick’ in the number of such services over the past few months as the variety of 2FA circumvention solutions is increasing.
Though 2FA security has emerged as a potent solution to protect our accounts, threat actors are eager to develop methods to exploit the OTPs and gain access to user accounts, either via social engineering or malware.
“While SMS- and phone-call-based OTP services are better than nothing, criminals have found ways to socially engineer their way around the safeguards,” researchers noted.
How does 2FA Works?
For your information, the purpose of 2FA security is to authenticate a user’s identity before allowing them access to some service. This verification can take place in the form of one-time password or OTP tokens, links, codes, biometric markers, or simply require a tap on a physical dongle.
Usually, 2FA tokens are sent to an email address or a mobile device as a text message.
How Telegram is exploited by bots
Intel 471 revealed that since June, they had observed a sudden increase in the exploitation of Telegram messaging service by 2FA circumventing solutions. The Telegram platform is either used to create/manage bots or serve as a customer support channel for cybercriminals.
According to researchers, Telegram bots automatically call potential victims of phishing attempts and send them messages that appear to be sent by the bank. These bots try to trick the victims into handing over OTP codes. Some bots are targeting social media users through phishing and SIM-Swap attacks.
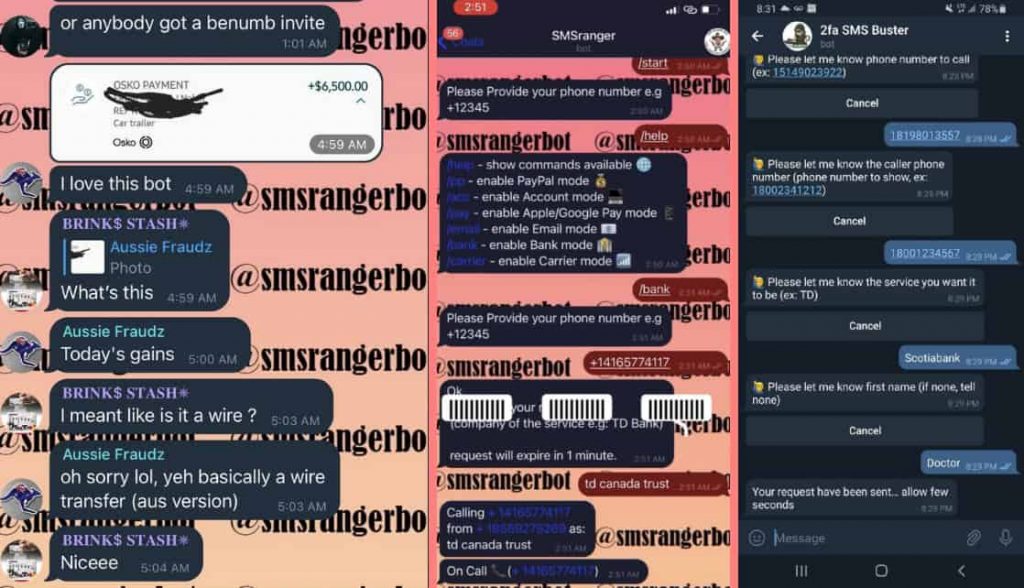
Actors show their earnings from the SMSRanger bot in a Telegram channel (left) – Command module for SMSRanger bot (center) – SMSBuster disguises a call to make it appear as a legitimate contact from a specific bank (right) – Screenshots via Intel 471.
Two Key Bots Identified
Researchers have identified two bots taking part in this malicious campaign. One is called SMSRanger while the other is BloodOTPbot. SMSRanger command setup and interface are pretty similar to the Slack collaboration platform and can potentially target services like Apple Pay, PayPal, and Google Play.
SEE: ToxicEye RAT hits Telegram app to spy, steal user data
Conversely, BloodOTPbot is an SMS-based bot that can generate automatic calls impersonating a bank’s customer support. On the other hand, KrebsOnSecurity’s Brian Krebs warned about a new cybercrime service letting attackers intercept one-time passwords, which most websites require as an additional security measure to verify users.
“These services are springing up because they work and they’re profitable. And they’re profitable because far too many websites and services funnel users toward multi-factor authentication methods that can be intercepted, spoofed, or misdirected — like SMS-based one-time codes, or even app-generated OTP tokens,” Brian Krebs wrote on the blog.