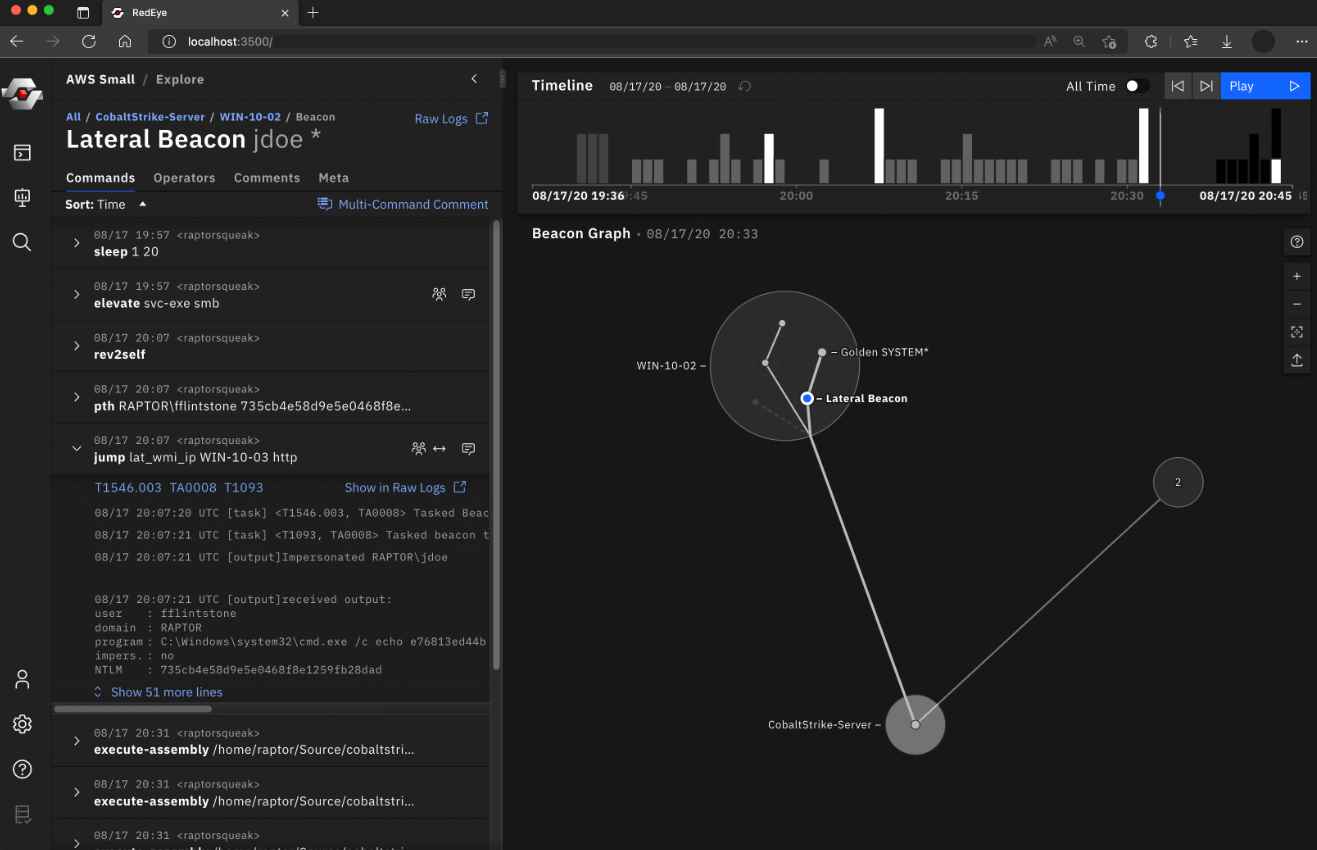
GoDaddy, a company that provides web hosting services, has now announced a security breach in which the company’s computers were breached and source code was taken. Throughout this multi-year attack, the perpetrators managed to get illegal access to the victim’s cPanel shared hosting environment, which led to the issue at hand. Early in the month of December 2022, GoDaddy uncovered a security vulnerability after getting many complaints from consumers stating that the websites they owned were being redirected to domains that were unfamiliar to them. After conducting an investigation, the company discovered that the sporadic redirects were occurring on what appeared to be random websites that were hosted on their cPanel shared hosting servers. Furthermore, the company discovered that they were unable to easily reproduce the issue, even on the same website.
Godaddy discovered, after doing more research into the matter, that an unauthorised third party had put malware on the servers that are part of our cPanel shared hosting environment. This malware was the cause of the sporadic redirection of client websites.
The Company thinks that the security breach was part of a multi-year effort carried out by a sophisticated threat actor organisation. The campaign was carried out by an unknown entity. The gang infiltrated the company’s networks using malicious software and stole parts of code that were connected to certain of the company’s services.
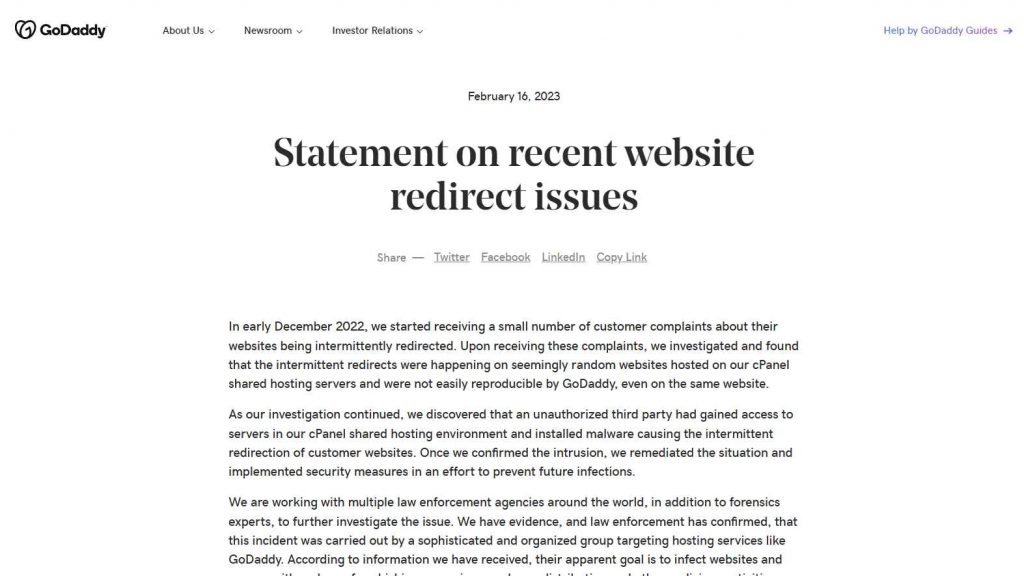
The hosting company believes that the prior breaches that were discovered in March 2020 and November 2021 are also connected to this multi-year effort, as stated in a statement that was included in an SEC filing that the company submitted.
Godaddy announced in March 2020 that a threat actor had compromised the hosting login credentials of roughly 28,000 hosting customers to their hosting accounts, in addition to the hosting login credentials of a limited number of Godaddy’s workers. On the other hand, these hosting login credentials did not provide access to the primary GoDaddy account associated with the hosting clients.
An unauthorised third party gained access to the provisioning system in the company’s legacy code base for Managed WordPress (MWP) in November 2021 by making use of a password that had been compromised. This breach had the potential to affect up to 1.2 million active and inactive MWP customers across multiple GoDaddy brands.
In their statement, Godaddy said that, in addition to forensics professionals, they are collaborating with different law enforcement authorities located all over the globe to further examine the matter.
In addition, GoDaddy asserts that it has found more evidence tying the threat actors to a larger operation that has been attacking other hosting providers all around the globe over the course of many years. This suggests that the attackers are a part of a more sophisticated and coordinated organisation that has been aiming its attacks at hosting providers.
According to a statement released by the hosting firm, the apparent objective of the attackers is to infect websites and servers with malware so that they may participate in phishing operations, distribute malware, and engage in other criminal actions. This puts not just GoDaddy at danger, but also its clients and the websites they host with GoDaddy.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.