Another day, another Android malware targeting those who download apps from Play Store – This time, however, malware aims at hijacking Facebook and Google Play accounts.
Trend Micro researchers have identified new Android malware dubbed as GhostTeam. It is capable of stealing Facebook credentials after infecting devices. The malware tricks unsuspecting users into installing it and it is spread through malicious, infected apps. Research suggests that it is present in 53 different applications. One of these infected apps has over 100,000 downloads.
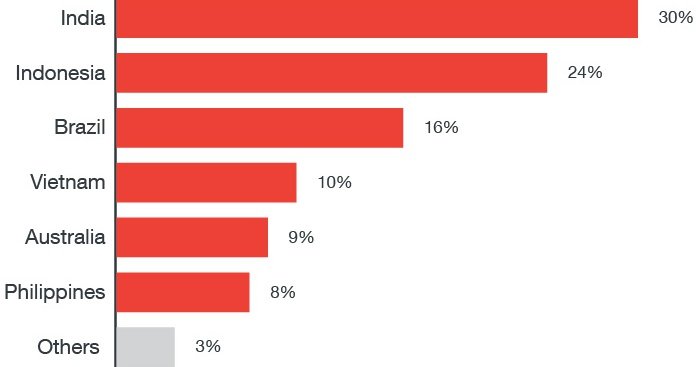
The prominent targets of GhostTeam include users in Brazil, India, and Indonesia but researchers are of the opinion that this campaign will spread to other regions most probably to the US considering that Google Play Store has been unknowingly harboring malicious apps since April 2017.
More: Hacking Facebook Account by Simply Knowing Account Phone Number
Just like other Android malware, GhostTeam also is capable of performing a variety of tasks. It basically steals Facebook credentials, which Trend Micro researchers believe could be an attempt to build what they refer to as a “zombie social media army.” Their objective, speculate researchers, is to spread unauthentic news articles and cryptocurrency mining malware along with launching full-screen ads on targeted devices to generate click revenue.
The apps in which this malware is hidden are harmless looking regular apps such as social media video downloaders, flashlights, and QR scanners, etc. It must be noted that the malware is not downloaded by the installation of these apps, just like other malware does, but instead, it involves a multi-stage attack process so as to keep its payload hidden.
One of the malware infected apps
After the infected app is downloaded from Play Store it checks if it is running on an Android VM or an emulator to hide its code from security professionals. Once it realizes that it is running on a physical device, it downloads the GhostTeam payload in the form of Google Play Services app. When the user opens Facebook or Google Play, a popup appears requesting to install the fake Google Play Services app and also asks for administrator-level permissions.
Afterwards, whenever the user opens Facebook for the first time, a fake WebView page is loaded, which asks the user to verify his/her Facebook account. The malware captures the email ID and password and immediately sends it to its C&C server. If 2FA is not enabled, the attackers would easily access the account.
To stay protected, you need to install a reliable anti-virus app and before downloading an app do check out its reviews, comments, and ratings. If you suspect anything fishy, do not download it at all. Furthermore, you need to keep Android device updated with latest security patches.
If you somehow fall prey to GhostTeam infection, you can disable device administrator permissions from accessing Settings menu to mitigate the threat. Finally, it is really important to enable 2FA (two-factor-authentication) for Facebook and all other social media accounts wherever it is available.
Trend Micro has already informed Google about the presence of infected apps and these have been removed as well. The company has updated Google Play Protect to detect GhostTeam.
More: Researcher reports how to hack Facebook account with Oculus Integration










