The company behind Aztarna is Alias Robotics, a cyber-security startup.
Manufacturers and users of IoT robots should breathe a sigh of relief that the cyber-security startup Alias Robotics has developed a robot scanning tool that can track any robot connected to the internet and powered by any robotic technology such as ROS or SROS.
Dubbed Aztarna by researchers (meaning footprint in the Basque language), it is an open-source tool that will be readily available for researchers to perform robot footprinting, auditing of internet-connected robots, and identifying/locating robots or their components, etc.
The best part is that the scanning cannot only be performed on internet connected robots but also for those industries where robots are part of day-to-day operations. The research findings have been published in a paper [PDF] titled “Aztarna, a footprinting tool for robots.”
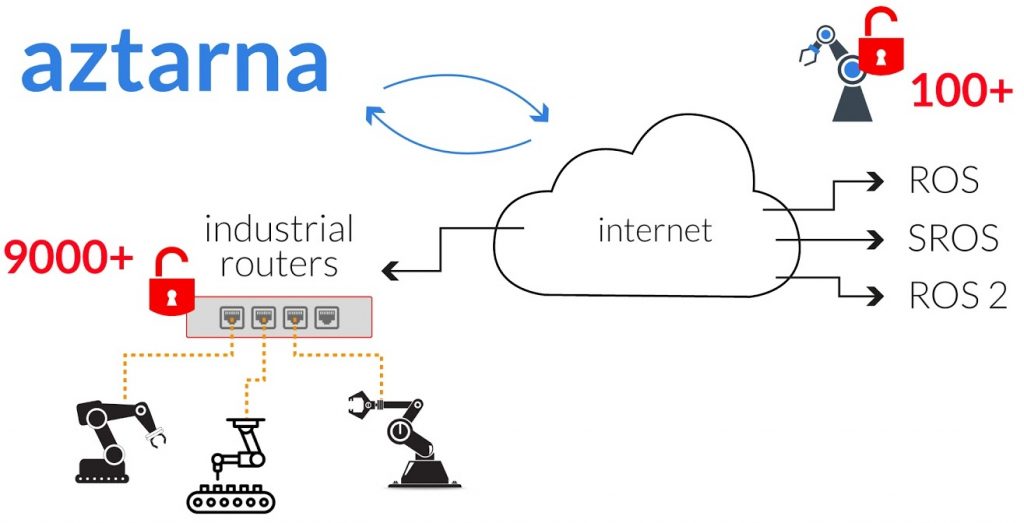
Alias Robotics’ research team carried out scanning of industrial routers for different countries and only in their first attempt they were able to identify 9000 insecure industrial routers hosting vulnerable robots. Researchers revealed in their paper that 1586 of the 9000 insecure routers were located in Europe and France and Spain topped the list with 63% and 54% of misconfigured devices respectively. However, the number of insecure industrial routers was equally higher in the US (36%), Canada (41%) and other North American countries.
Among the various manufacturers, Alias Robotics scanned industrial routers made by Sierra Wireless, Ewon, Moxa, and Westermo since these are the widely used routers in the industries. A total of 26801 routers were identified and almost 33% (8958 of the total routers) were declared insecure. In this regard, Columbia had the highest number of misconfigured and insecure devices with 26 connected devices and 100% of them using default credentials.
Furthermore, researchers performed two different scans across the internet to search for open ROS Master in port 11311. Using Aztarna, the team could verify whether the hosts were corresponding to ROS running machines or not and discovered 106 ROS systems most of which were located in the US (52) and Korea (16).
Although some ROS systems were found to be corresponding to empty simulations/systems majority were real robots including research-oriented machines and industrial robots.
The researchers claim that robots could be a potential threat to cybersecurity, which is why it is really important to secure them but the manufacturers are not paying attention to their warning. Alias Robotics’ CEO David Mayoral stated that:
“Our aim was to improve, systematize and extend the results of previous studies. We target not only robots powered by the Robot Operating System (ROS), but also other setups (SROS, ROS 2.0) and technologies. Beyond robotics frameworks, our work also targets other robots that do not necessarily employ these popular middlewares.”
After not receiving a favorable response from manufacturers, the researchers have opened up the code and regard it as a ‘general consequence’ of the lack of concern showed by those responsible for making robots.
“We value the importance to empower security researchers and aim to raise security-awareness among roboticists, by releasing this robot security auditing tool. It’s not only that they are very slow patching their flaws when we warn them. Many just don’t care and say: We know our robots have a set of reported vulnerabilities, but we leave security up to the end user,” Mayoral explained.