The bug would allow attackers to steal Windows credentials literally without any difficulty.
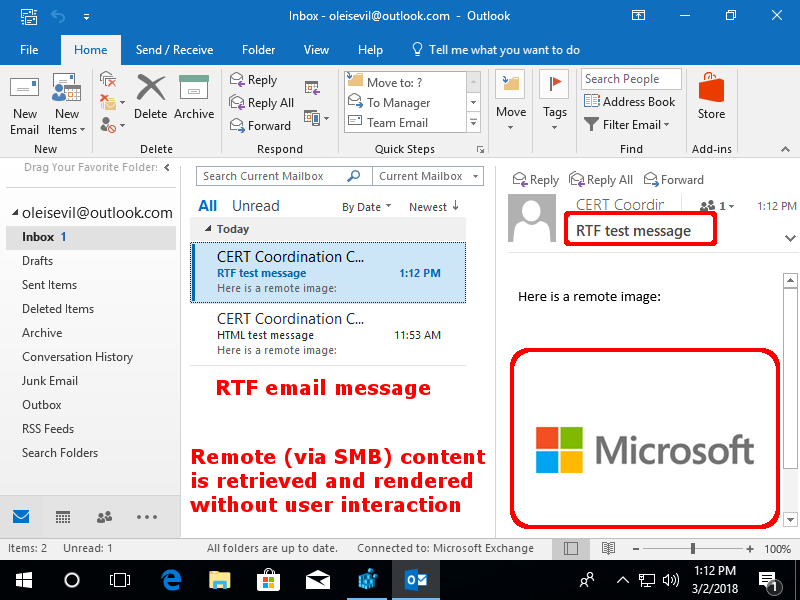
A critical Outlook bug that was identified over a year back has been fixed by Microsoft now. It was found to be capable of leaking password hashes when a user previews an RTF (rich text format) email containing remotely hosted OLE objects.
CERT Coordination Center or CERT/CC’s vulnerability analyst Will Dormann reported about the bug in November 2016 and it took the company more than a year to finally fix it. The patch has been released publicly by Microsoft in its Patch Tuesday release. However, the patch for the vulnerability, which has been categorized as CVE-2018-0950, is believed to be incomplete.
The Outlook vulnerability lets an attacker steal sensitive data such as a user’s Windows login credentials simply by convincing the victim to preview an email by opening MS Outlook. It doesn’t require additional interaction with the user at all.
More: Hackers are digging into Microsoft Word flaw that existed for last 17 year
Dormann claims that the vulnerability exists in the way MS Outlook extracts remotely hosted OLE content when an RTF email is previewed. It then automatically initiates SMB connections. He further noted that Microsoft has not applied similar restrictions on content uploaded from a remote SMB server the way it did for web-hosted content.
The threat emerges from the way Outlook handles RTF emails in connection with Object Linking and OLE objects embedding, which are hosted on a remote Server Message Block or SMB server.
For instance, Outlook doesn’t automatically load web-hosted images in the email to prevent leaking of a client’s IP address and metadata details like the time an email was viewed. But, the problem occurs when Outlook shows a preview of RTF email message with an OLE object from a remote SMB server because the same level of precautions isn’t applied in this case.
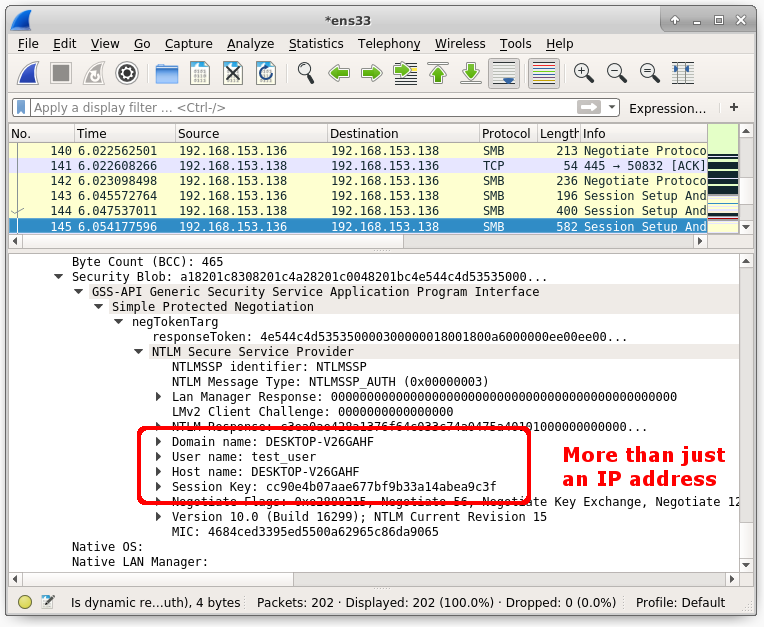
It was also discovered that OLE-SMB scenario leaks more than the user’s IP address. When the RTF email is previewed, the computer automatically negotiates an SMB session from a possibly malicious remote SMB server. Dormann discovered that the OLE-SMB scenario also leaks much more than a user’s IP address.
As soon as the email is previewed, the PC automatically negotiates an SMB session with a potentially malicious remote SMB server, which in turn leaks the client’s IP address, domain name, username, hostname, and the SMB session key in the form of an NTLM over SMB password hash. It must be noted that SMB servers can utilize Microsoft’s NT LAN Manager (NTLM) authentication protocol to create a connection between an SMB server and a Windows client.
The proximity of threat depends upon the strength of the target’s password; Dormann tested two password crackers on a mid-range GPU and managed to crack simple and weak passwords like ‘test’ within mere seconds. Eight-character passwords comprising of lower-case randomly produced letters are easier to crack as Dormann managed to crack them in 16 minutes only.
On the other hand, an eight-character password containing mixed-case letters along with symbols and digits would take a year at least with this setup. Dormann also noted that the patch released by Microsoft cannot prevent remote SMB attacks.
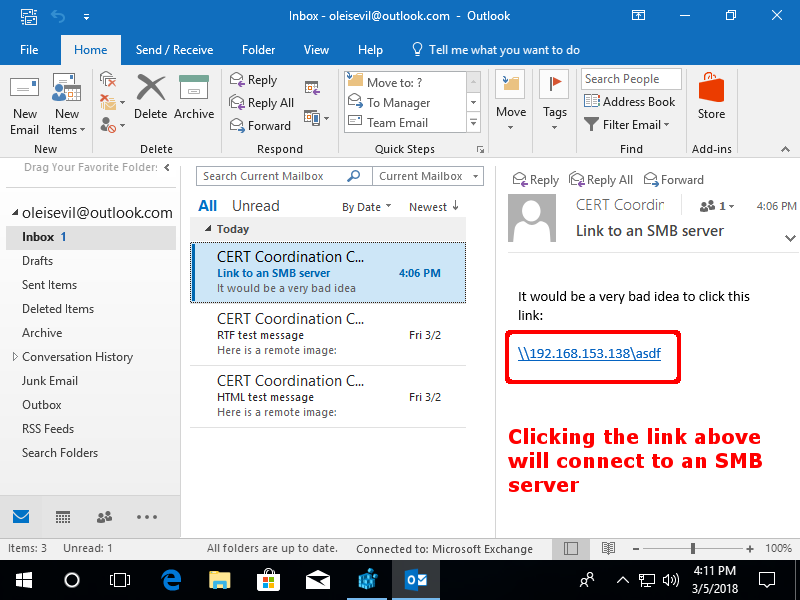
The attacker can send a Universal Naming Convention or UNC link instead of loading a remote image. The UNC link begins with ‘\’ and directs the user to a malicious SMB server. This automatically initiates an SMB session and leaks the same data. However, the victim would require clicking the link and mere previewing the email won’t work in this case.
“It is important to realize that even with this patch, a user is still a single click away from falling victim to the types of attacks described above. For example, if an email message has a UNC-style link that begins with “\”, clicking the link initiates an SMB connection to the specified server,” explained Dormann.
As per Dormann, it is important to install the patch released by Microsoft but also advises administrators to take other precautionary measures such as blocking the TCP and UDP ports for outgoing and incoming SMB sessions and blocking NTLM single sign-on to external sources so that users are compelled to use lengthier passphrases instead of simple passwords.
In its Patch Tuesday, Microsoft has released patches for 63 vulnerabilities including 22 serious flaws.