DRAMMER, a dangerous threat to Android Devices — Google has awarded the researchers $4000 for identifying the bug but it will take a while to get rid of it.
IT security researchers from the University of Amsterdam have discovered a security flaw in the memory chip design used in Android Devices. The flaw allows the attackers to target a specific memory chip and thus gaining control of the entire system. Drammer has the potential to put millions of users at risk, especially when combined with existing attack vectors like Stagefright.
Also Read: New Android Malware Asks for Selfies; Steals Credit Card Details
Not a new method
The attack goes by the name of Rowhammer which is not new. Previously, security researchers found a similar flaw in systems running on Linux. The flaw could also be exploited to launch a Rowhammer attack. This time, however, it is the Android devices that are in danger.
How does it work?
Essentially, the Rowhammer, as the name suggests, targets a row of transistors in a memory chip. These are the DDR DRAM chips found in mobile android devices. The attack is usually executed through a harmful app unbeknownst to the user.
Primarily, the attacker implants the code in such an app. When the code is executed, the app keeps on accessing a specific row of transistors. It is a repetitive process which causes that row of transistors to cause an electric disturbance with the rows nearby. This leads to a leak in electricity which eventually results in a bit flip.
A bit flip, in turn, is simply the interchange of bits of data in random positions. Due to such randomization of bits, the attacker is able to change values for data stored on the chip and gain access to the victim’s device.
Also Read: 2016 Best Hacking Apps for Android Phones
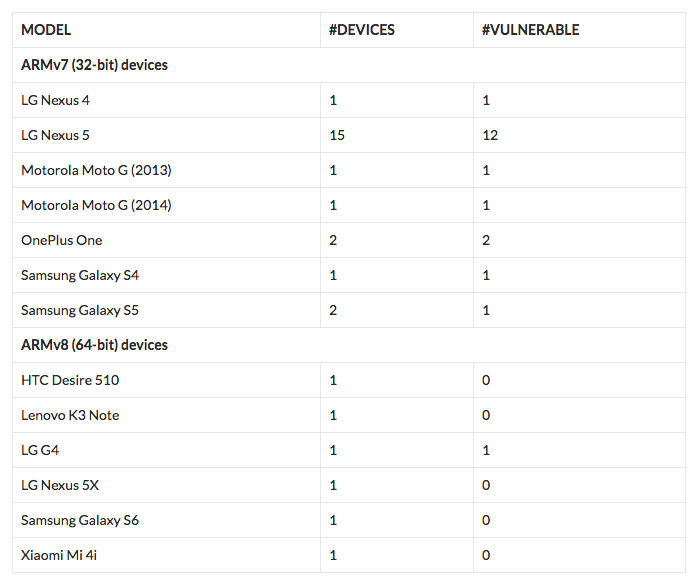
List of Android devices tested by researchers
Proof-of-concept
In order to test the attack, the researchers themselves devised an attack aimed at mobile devices such as Samsung, LG, etc. The project was named “DRAMMER”. The mechanism allowed the researchers to gain root access to the victim’s device.
Also Read: Beware; Adwind RAT infecting Windows, OS X, Linux and Android Devices
Reporting to Google
The vulnerability has already been reported to Google for which Google awarded the researchers a sum of $4000. It states that it is crucial to fix the issue and we can expect an update coming soon in November.
However, the real issue is the inherent design of the chips and software. The Rowhammer attack exploits an innate weakness in the design. This means it may be a while before Google can come with another design concept that eradicates the inherent weakness.
Read Next: After Linux, TCP Exploit Expandable to 80% of Android Devices
H/T Security Affairs
Research Paper: VUSec
Image Source: Flickr/Uncalno Tekno










