A major vulnerability with a ranking of 10.0 was discovered in specific universal copy service software that is used in some Illumina genome sequencing instruments. This vulnerability might make it possible for a variety of malicious operations to be carried out, including the remote uploading and execution of code at the operating system level.

The Cybersecurity and Infrastructure Security Agency (CISA) and the Food and Drug Administration (FDA) are advising network defenders in the healthcare sector to evaluate their warnings, as well as the Illumina security advice, in order to guarantee that the concerned devices have the highest level of protection possible against malicious actions.
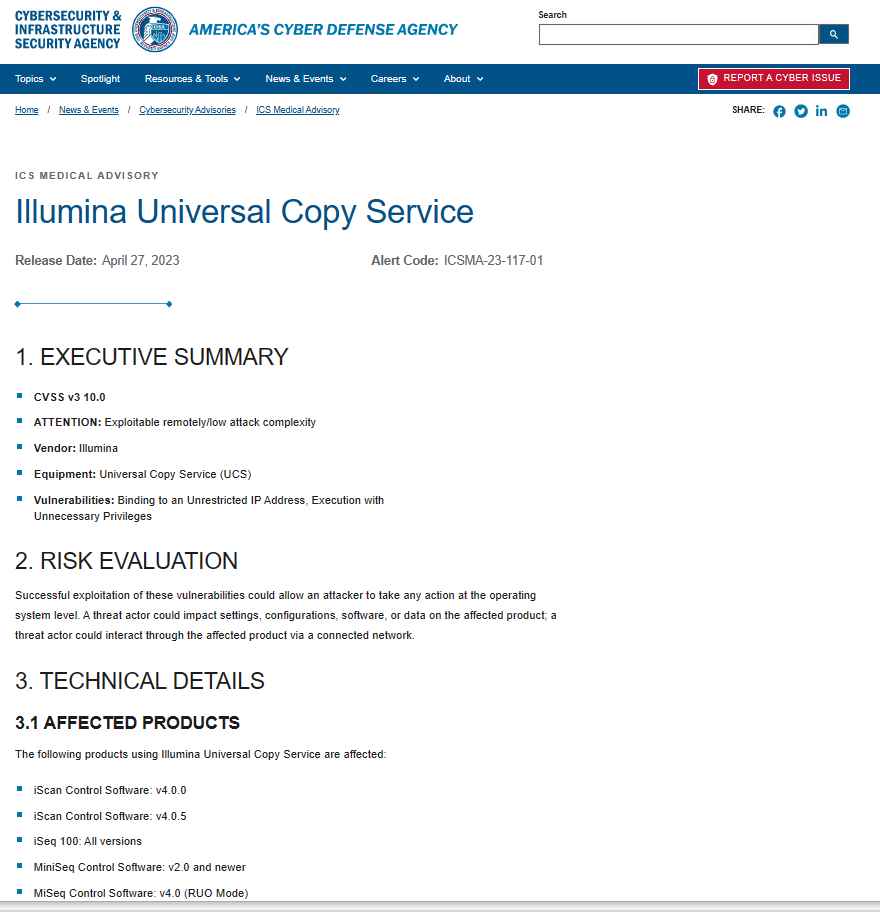
A vulnerability with a ranking of 7.4 was reported in addition to the a flaw with a score of 10.0. Both of these flaws are present in multiple iterations of the iScan Control Software, as well as the products iSeq 100, MiniSeq, MiSeqDX, NextSeq, and NovaSeq. In addition to doing other types of next-generation sequencing, these technologies also conduct bioinformatics.
The Food and Drug Administration (FDA) considers these to be medical devices that may either be used for research or in clinical diagnostic settings to sequence the DNA of persons in order to identify genetic disorders. The warnings indicate that the potentially catastrophic vulnerability is located in the universal copy service function v2.x. This function transfers the sequencing output files from the device’s run folder to the output folder. On the other hand, it is tied to an IP address that does not have any restrictions placed on it, which means that an unauthenticated attack might utilize the UCS to listen on any and all IP addresses, even those that permit remote connections.
In the meanwhile, the “unnecessary privileges” vulnerability, which has a severity rating of 7.4 out of 10, may be detected in instruments that use either the v1.x or the v2.x platform. The vulnerability might make it possible for an unauthenticated threat actor to remotely upload and execute code at the level of the operating system. This would provide the threat actor the ability to alter settings, configurations, and applications, as well as get access to sensitive data. The Food and Drug Administration (FDA) issues a warning that an attacker would not need to get credentials to remotely deploy harmful operations, such as the potential change of data that is held on the instrument or on the networks of customers.
An attack might also have an effect on the results of the genetic data that is stored on the instruments, which would cause “the instruments to provide no results, incorrect results, altered results, or a potential data breach.”
According to the warning, “At this time, the FDA and Illumina have not received any reports indicating that this vulnerability has been exploited.”
Illumina informed CISA about the vulnerability and developed advise for system users based on particular setups in order to lessen the effect of these severe issues. The business has already produced a software patch to guard against exploit, and the FDA is now asking “providers and laboratory personnel to be aware of the required actions to mitigate these cybersecurity risks.”
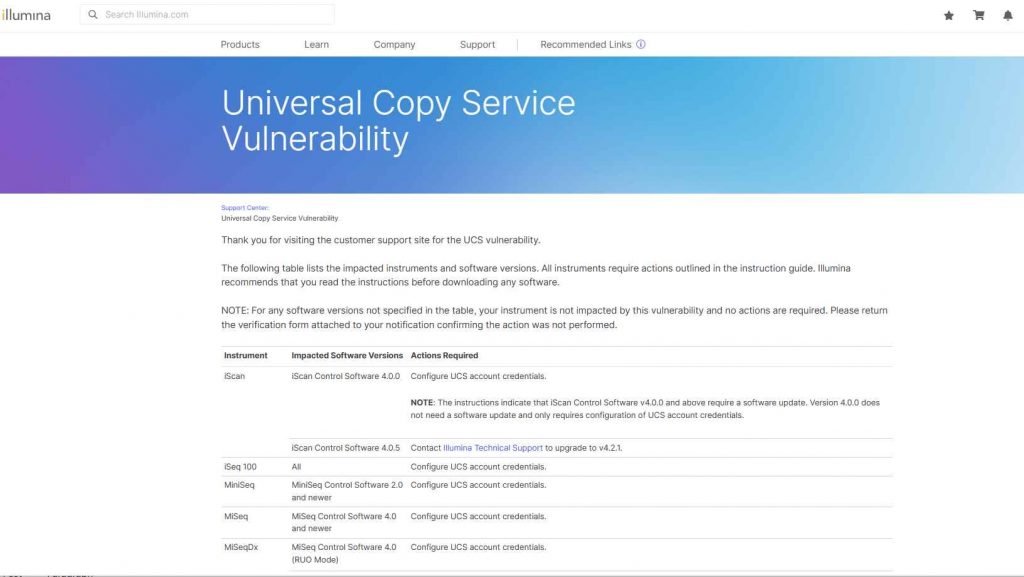
It is advised that the credentials for the UCS account be configured on a large number of the devices that have been affected, while the software on other systems will need to be updated. Additionally, the business produced instructional videos for its customers, all of which are password-protected to prevent unauthorized access from the outside world.
In the beginning of this month, Illumina sent notifications about the vulnerabilities directly to users and urged them to keep an eye out for any signs that an exploit was being used on the affected devices.
To our great fortune, there have not been any public exploits revealed yet that target this vulnerability at this time. CISA advises that network defenders adopt defensive steps to limit the danger of exploit. These measures include reducing the exposure for all control systems and devices and blocking access from the internet. However, given the current state of the threat environment, this is subject to change quite fast.
When access to a distant location is essential, the use of Virtual Private Networks (VPNs) or similar secure approach is recommended. However, virtual private networks (VPNs) come with their own set of vulnerabilities; therefore, defenders should make sure that the tools they use are always updated to the most recent version.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.