TangleBot Android malware is delivered through smishing and is currently targeting users in Canada and the US disguised as information about COVID-19 vaccination.
It is a fact that SMS messages have become a preferred attack vector to spread malicious software and infect mobile devices. Recently, Hackread reported the notorious FluBot SMS Android malware that targeted mobile devices across Europe and the UK.
Now, there is another Android malware on the block called TangleBot, which employs more or less similar tactics to gain control of the device- the problem is that it is far more invasive than FluBot.
TangleBot Causing Trouble for Android Users
According to Cloudmark and Proofpoint cybersecurity researchers, both of which reported the new SMS-based (SMishing) malware campaign involving TangleBot, when TangleBot is installed on a device, it gains access to several different permissions to eavesdrop on user communications.
The malware also steals sensitive data stored on the device and monitors just about every user activity such as camera usage, audio conversations, and location, etc. Furthermore, the malware takes full control of the targeted device, including accessing banking data and can penetrate the deepest corners of Android OS.
Who are the Targets?
At the moment, TangleBot is targeting users in the USA and Canada. The malware gets installed when an unsuspecting user clicks on a malicious link received in an SMS message.
As soon as the link is clicked, malware operators get complete control of the device, from websites visited stealing login credentials and passwords since it uses a keylogger and spies on the user.
Hence, the malware is equipped with a full range of surveillance and data-stealing features.
The Lure
According to Proofpoint researchers, the initial lure comes as an SMS message, and this message is masqueraded as information about COVID-19 vaccination regulations/appointment-related information.
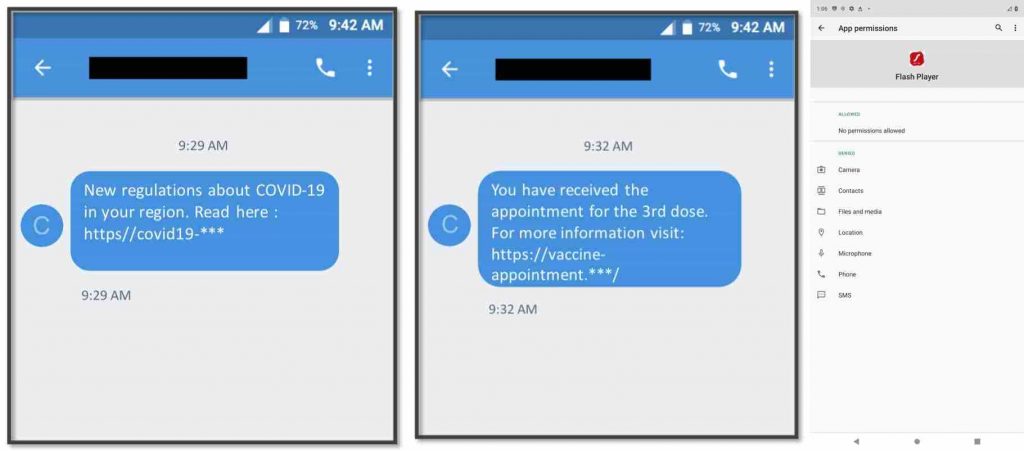
SMS with COVID and vaccine lures (Left, center) – Permissions requested by TangleBot (Right) Image: Cloudmark
More recently, researchers have noted a change in attackers’ strategy as there’s a new message that informs about fake local power outages that are due to occur.
Nevertheless, the aim behind both messages remains the same- to encourage potential victims to follow a link that supposedly offers detailed information. Once they are at the page, the user is asked to update to Adobe Flash Player to view the page’s content.
It is worth noting that Adobe stopped supporting Flash, back in Dec 2020, and it no longer supports Flash on mobile devices. Afterward, the victim goes through nine dialogue boxes to give acceptance to different permissions. If they agree to provide all the permissions, malware operators will initiate the malware configuration process.
How to Stay Safe?
In its blog post, researchers at Cloudmark explained that users should avoid checking out suspicious-looking SMS messages, never provide their mobile phone number to a commercial entity. If they receive a warning message containing a web link, they must access the enterprise or service’s website directly and refrain from opening the link.
Lastly, users in the United States can report SMS phishing spam and forward the text messages to 7726 (SPAM). Those in Canada can Canadian Anti-Fraud Centre by telephone at 1-888-495-8501.