In the computer security world, once a vulnerability is found it doesn’t take much longer for the security researchers to find similar flaws and propose new attack mechanisms. The researchers at College of William and Mary, University of California Riverside, Carnegie Mellon University in Qatar, and Binghamton University, have found a new Spectre-like attack.
Before I go ahead and tell you something about this attack named “BranchScope,” let me talk about “speculative execution” — a feature of modern CPUs that’s responsible for such attacks.
With speculative execution, your computer’s CPU can process calculation ahead of the current state of the program and make attempts to guess what could happen next. When a program finally moves ahead, the CPU discards the wrong guesses and performs the correct action.
In the perfect scenario, the CPU should clear the cache entirely and get rid of any stored data used for guessing as it could even contain some secret information. But, that’s not the case here. Just like Spectre 2, BranchScope attack also exploits this possibility of any residue data.
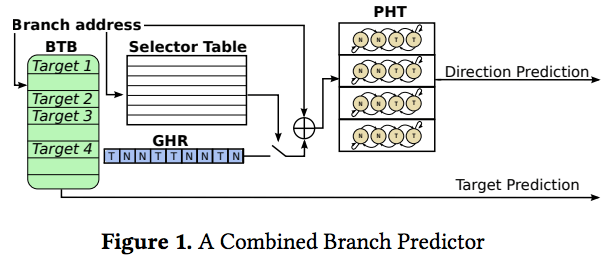
Now, talking specifically about BranchScope attack, it deals with a CPU’s Branch prediction units (BPUs). A BPU tracks if a particular instruction branch is followed or not. Now, when multiple processes are executed on the same physical core, they end up sharing same branch predictor.
This, theoretically, opens up the possibility of an attacker getting access to shared BPU and creating a side-channel, thereby leaking sensitive data. For example, if an instruction involves a secret key, it can be leaked directly.
There are chances that the Spectre and Meltdown microcode updates released by Intel might have only fixed branch target buffer (BTB), which is just one component of BPU. So, there are chances that BranchScope attack is still possible.
It’s worth noting that BranchScope isn’t the first side-channel attack after Meltdown and Spectre. We’ve already told you about SgxSpectre attack that targeted Intel SGX (Software Guard Extension).
“The attacker may also change the predictor state, changing its behavior in the victim,” reads the paper detailing the attack. It also claims that BranchScope could be extended to attack SGX enclaves with even lower system rates.
You can read about the attack in detail in this research paper.