Yung said that the version was compromised by some attackers before its release, who managed to attach some malware to the setup.
“A suspicious activity was identified on September 12th, 2017, where we saw an unknown IP address receiving data from software found in version 5.33.6162 of CCleaner, and CCleaner Cloud version 1.07.3191, on 32-bit Windows systems,” he added.
A two-stage backdoor was inserted in the CCleaner.exe binary which was capable of remote code execution after receiving commands from a remote IP.
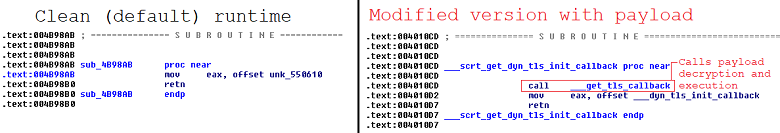
The malicious software could collect data from infected machines like the name of the computer, list of installed software and Windows Updates, list of running processes, mac addresses of the first three adapters, and information whether the machine was 32-bit or 64-bit, etc.
Based on their analysis, Piriform claims that the changes to the software were made before its released to the public. But, it’s still not known how the code ended up in the binary or who are forces acting behind the attack.
Here’s what to do?
The security breach has been taken care of by Piriform and an update is available as CCleaner 5.34 (direct download). Users are advised to update to the latest available version immediately. For Cloud users, automatic updates have been pushed.
According to Piriform, around 2.27 million users might have installed the infected version of the CCleaner software, a spokesperson told TechCrunch.
If you have something to add, drop your thoughts and feedback.