Short Bytes: A team of researchers at VUSec Lab has successfully demonstrated Drammer attack which is an implementation of the Rowhammer attack for ARM-based devices. The attack has the potential to root millions of Android devices from renowned brands like Samsung, LG, Motorola, OnePlus, Xiaomi, etc.
Short Bytes: A team of researchers at VUSec Lab has successfully demonstrated Drammer attack which is an implementation of the Rowhammer attack for ARM-based devices. The attack has the potential to root millions of Android devices from renowned brands like Samsung, LG, Motorola, OnePlus, Xiaomi, etc.
The same attack has been crafted for Android devices, most of which run on ARM-based hardware. The work has been done by the researcher from VUSec Lab at the Vrije Universiteit Amsterdam. “Drammer is the first Android root exploit that relies on no software vulnerability,” wrote the researcher in a blog post.
So, what is DRAMMER?
Drammer, stands for Dynamic Rowhammer, has the similar functionality as its PC counterpart. It is an instance of the Flip Feng Shui exploitation technique. Once in action, it tries to irritate or hammer a DRAM memory cell row. As you know the memory is not a physical thing but electric charge. The irritated row can leak its electric charge to an adjacent row causing its value to change i.e. from 0 to 1 or 1 to 0. The process is known as bit flipping.
This change alters the data stored in the memory cell. If the process is done carefully, root privileges can be acquired on the target Android device. A detailed description about Drammer has been published in the paper, “Drammer: Deterministic Rowhammer Attacks on Mobile Platforms“, authored by Victor van der Veen et al.
Recommended: What Is Rooting? Is Rooting My Android Smartphone Illegal?2016/10/18
The attacker can get an application installed on the target device which doesn’t even ask for any user permissions. During the demos, the researchers clubbed Drammer with Stagefright (used for remote code execution).
“By tricking the victim into opening a malicious URL, an attacker gains remote shell access to the vulnerable device. Since the exploited mediaserver is not running with root privileges, however, he still cannot access /sdcard, for example. The attacker then launches the Drammer exploit which does give him full control over the device.”
Here is the demo video:
Is my phone affected?
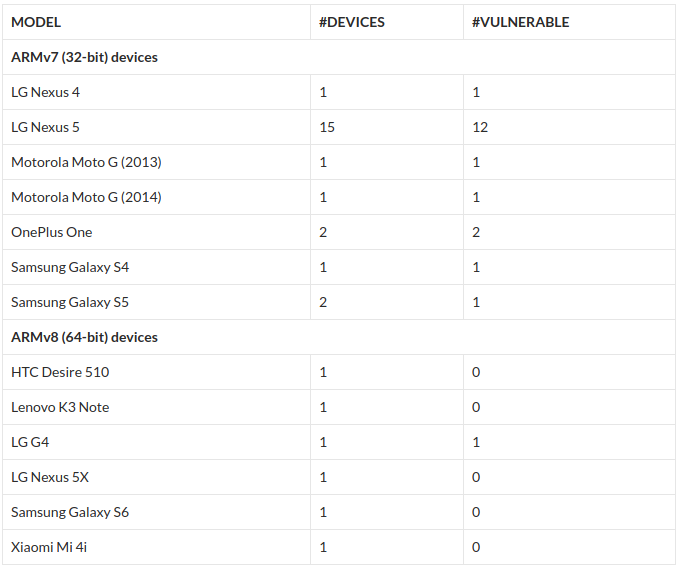
Researchers wrote that popular devices from big brands like Samsung, LG, Nexus, Motorola and Xiaomi are vulnerable to the drammer attack. In order to test the attack on various devices, they have created an android app which they call Drammer Test App in collaboration with Univerisity of California, Santa Barbara. Out of the 27 devices, the researchers were able to flip bits on 18 of them.
On the device, the app detects whether any bit flips were made, and sends anonymized data to the researchers if the test is successful. However, the researchers acknowledge the fact that their app falls short on some technical aspects and it is being improved. “Your phone might still be vulnerable, even if the app detected zero flips!”.
It is not available on Google Play Store. The researchers have given the download link in the blog post itself.
Drammer is here, what’s next?
A ray of hope given by the researchers is that Drammer attack is less effective for LPDDR4 memory. “This is because the LPDDR4 standard includes optional hardware support for the so-called target row refresh mitigation.”
On July 25, the researcher notified Google’s Android Security Team about the hardware-level vulnerability (CVE-2016-6728) for which they received a bug bounty cash reward. Google marked the vulnerability as critical. In was on October 3, when Google informed the hardware partner about the issue. A patch is scheduled to arrive in the November Android Security Bulletin.
“Note that, although Google’s patch round from November complicates our attack, it does not eradicate it. We hope to see a more sophisticated fix soon.”
The demo video of LG Nexus 5 running Android 6.0.1 with latest security patches:
If you have something to add, tell us in the comments below.
Also Read: Dyn DDoS Attack: Here’s How Hackers Took Down Half Of The Internet