Cybercriminals will stop at nothing to take every chance to attack Internet users.
Even the catastrophic spread of SARS-COV-II (virus), causing COVID-19 (disease), enables them to spread malware or launch cyber attacks.
Reason Cybersecurity recently released a threat analysis report detailing a new attack that exploits the increased desire of Internet users to receive information about a new coronavirus that is damaging the world.
The malicious attack is specifically aimed at those who are looking for cartographic presentations about the distribution of COVID-19(via coronavirus map application) on the Internet, as well as tips for downloading and launching a malicious application that on its front panel shows a downloaded map from the Internet as a source of legitimacy, but in the background, it compromises the computer.
A new threat with an old malicious component- Coronavirus map
The latest threat, designed to steal information from unintended victims, was first discovered by MalwareHunterTeam last week and is now being analyzed by cybersecurity researcher Reason Labs Shay Alfasi.
Also Read: Kr00k Attack: New Wifi Encryption Vulnerability Affects Over Billion Devices
This is malware identified as AZORult, theft-malware detected in 2016. AZORult malware collects information stored in web browsers, in particular cookies, browsing history, user IDs, passwords and even cryptocurrency keys.
Using these data from browsers, cybercriminals can steal credit card numbers, login credentials, and other confidential information.
It is reported that AZORult was discussed at Russian underground forums as a tool for collecting sensitive data from computers. It comes with an option that can generate a hidden administrator account on infected computers to allow connections through the Remote Desktop Protocol (RDP).
Sample Analysis
Alfasi provides technical details of malware research that is embedded in a file, usually called Corona-virus-Map.com.exe. This is a small Win32 EXE file with a payload size of approximately 3.26 MB.
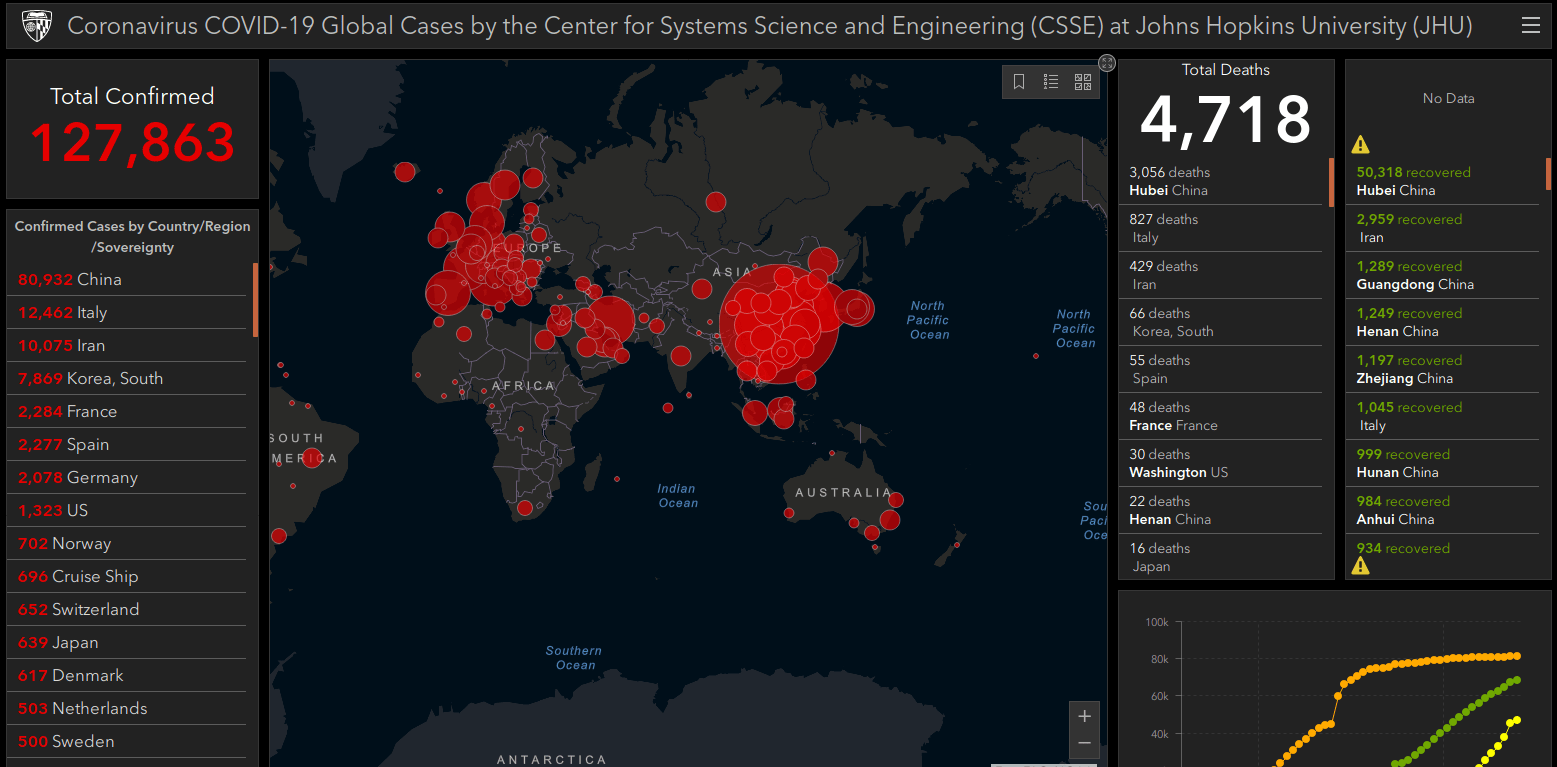
Double-clicking on the file opens a window with various information about the distribution of COVID-19. A central element is an “infection map,” similar to that maintained by Johns Hopkins University, a legitimate online source for viewing and tracking recorded cases of coronavirus in real-time.
The number of confirmed cases in different countries is presented on the left, and statistics on mortality and recovery are presented on the right. The window looks interactive, with tabs for various other related information and links to sources.
It provides a convincing graphical interface that few suspects of harm. The information presented is not random data, but the actual COVID-19 information collected on the John Hopkins website.
Please note that the original coronavirus map, posted on the Internet by Johns Hopkins University or ArcGIS, is in no way infected or misappropriated and can be visited in complete safety.
The malware uses certain packaging levels, as well as a multiprocessor technique, to make detection and analysis difficult for researchers. In addition, he uses a task scheduler to support his work.
Signs of infection
When you start Corona-virus-Map.com.exe, duplicates of the file Corona-virus-Map.com.exe and several Corona.exe, Bin.exe, Build.exe and Windows.Globalization.Font groups are created. Exe files.
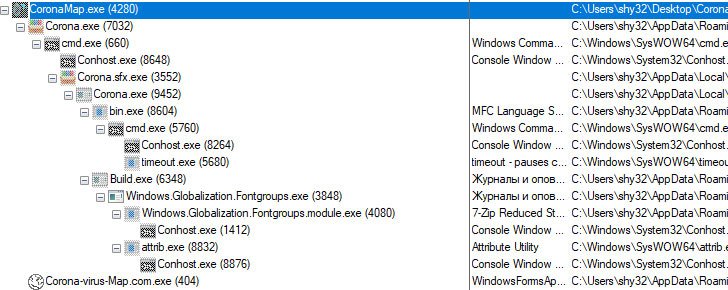
In addition, the malware changes several registers in ZoneMap and LanguageList. Several mutexes are also created.
Running the malware activates the following processes: Bin.exe, Windows.Globalization.Fontgroups.exe, and Corona-virus-Map.com.exe. They are trying to connect to multiple URLs.
These processes and URLs are just an example of what the attack entails. There are many other generated files and running processes. They create various online activities when malware attempts to collect different types of information.
How an attack steals information
Alfasi talked in detail about how he analyzed malware on his Reason Security blog. An important detail is his analysis of the Bin.exe process with Ollydbg. As a result, the process wrote several dynamically linked libraries (DLLs). The dll “nss3.dll” attracted his attention because it was what he knew from different actors.
Coronavirus Map
Alfasi observed the static loading of APIs related to nss3.dll. These APIs seem to make it easier to decrypt stored passwords, as well as generate output.
This is a general approach used by data thieves. Relatively simple, it only captures connection data from an infected web browser and moves it to the C: Windows Temp folder. This is one of the features of the AZORult attack, in which malware extracts data, generates a unique identifier for the infected computer, applies XOR encryption, and then initiates the C2 connection.
The malware makes certain calls to steal login information from popular online accounts such as Telegram and Steam.
Also Read: Top 10 FREE Music Download Websites in 2020
We emphasize that launching malware is the only step necessary to continue the process of information theft. Victims do not need to interact with the window or enter confidential information.
Cleaning and maintenance
It may seem adware, but Alfasi offers Reason antivirus software as a solution to recover infected devices and prevent further attacks. In the end, he is associated with Reason Security. The reason is to be the first to find and analyze this new threat so that they can effectively manage it.
Other security companies have probably been aware of the threat since Reason released it on March 9th. Their antivirus or malware defenses will be updated after publication.
In this way, they can also detect and prevent a new threat.
The key to removing and stopping the opportunistic Coronavirus Card malware is having the right malware protection system. It will be difficult to detect manually, not to mention removing the infection without the right software tool.
It may not be enough to be careful when downloading and running files from the Internet, as many of them, are usually too slow to access information about the new coronavirus these days.
Dispersion at the COVID-19 pandemic level deserves the greatest caution not only offline (to avoid becoming infected with this disease), but also on the Internet. Cyber-attackers exploit the popularity of coronavirus resources on the network, and many of them can be attacked.