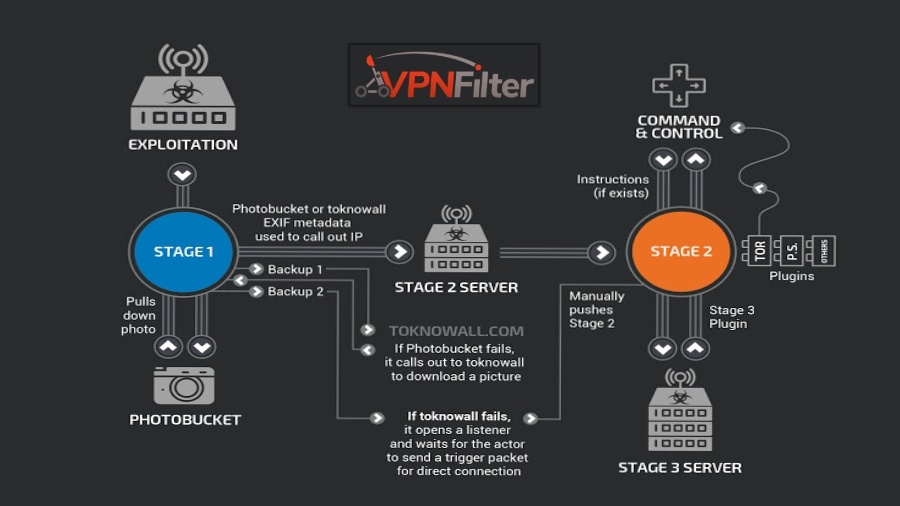
This week only, Cisco reported about the malware called VPNFilter which is assumed to have targeted around 500,000 routers to create a massive botnet. It’s believed that the malware, having a resemblance to BlackEnergy malware, could have its roots originating in Russia.
The manufacturers of affected routers and other network-connected devices include brands like Linksys, MikroTik, Netgear, and TP-Link.
American security agency FBI took down a crucial server used to perform the attack. On Friday, they issued a public service announcement for the owners of small office and home office routers (aka SOHO) in the US.
However, the advice will be helpful for anyone with a router because the malware has its reach in around 54 countries. It’s yet to be known how the malware spread.
How does this help?
Rebooting the router will temporarily disrupt the malware, FBI explains. So, when it tries to reconnect, FBI could identify the infected devices and possibly connect the dots to attackers.
FBI has also advised SOHO router owners to disable remote management settings and secure their device with strong passwords and encryption. It’s a common habit for many users to leave the default username and password as it is.
If merely rebooting sounds less secure to your ears, the option to hard reset the device is always at your disposal. The process is different for different devices, so, you can refer the documentation.