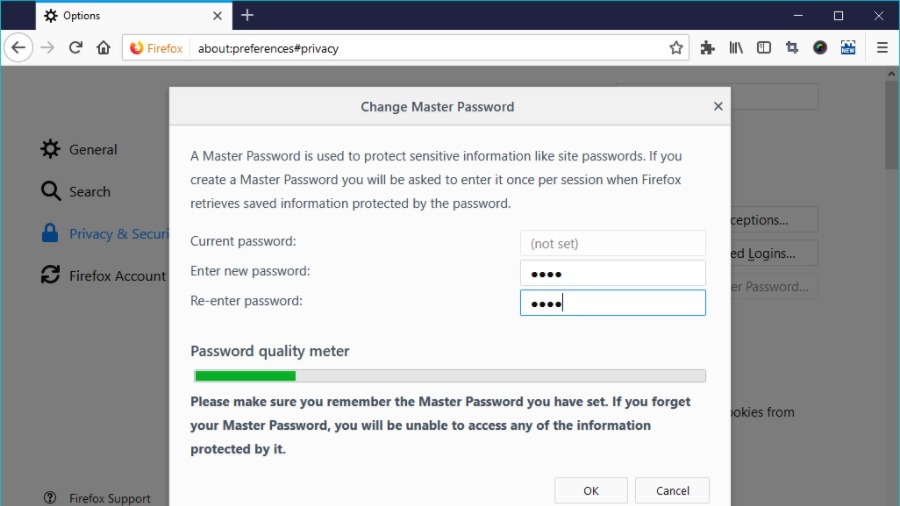
You might rest assured after setting a Master Password in the Firefox web browser, but it’s not as secure as you think. Last year, Mozilla did a major overhaul of their browser in the form of Firefox Quantum. But the non-profit forgot to fix the security holes that exist in their ‘very fast’ web browser for nine years.
The encryption scheme used for the Master Password feature is efficient enough, and it can be easily brute-forced, according to the security Wladimir Palant who is the creator of AdBlock Plus. Surprisingly, the issue wasn’t discovered recently but nine years ago when it was reported on the Mozilla bug tracker.
The Master Password feature is present in the Firefox browser and Thunderbird mail client. It is used to secure the login credentials stored by the users.
After looking at the source code, Wladimir points out that the SHA1 iteration count for the Master Password is just 1, i.e., it’s applied only once. It’s too low in comparison to the industry practice which is around 10,000.
The low iteration count makes the password manager vulnerable to attackers. With the aid of modern GPUs, a simple Master Password could be cracked in less a minute’s time with the help of brute-force attacks.
One possible way out is to keep long and strong Master Passwords. According to Mozilla, things would get in order after the launch of their new password manager component which is currently codenamed “Lockbox.”