According to a research, millions of Android devices from 11 OEMs are vulnerable to attacks from simple AT commands.
These AT commands or Attention commands are a short collection of strings which were designed to transmit via phone line and modems, back in the 1980s. Earlier, these commands were used for a modem dial-up, hang up, and change specific connection settings.
Surprisingly, most of the present Android devices still support these AT commands. Even though the telecommunication regulatory bodies have laid down a list of AT commands, OEM’s have added few of their own which could prove dangerous, if ever hacked.
A group of researchers from the University of Florida, Stony Brook University, and Samsung Research America analyzed, each OEM to know the AT commands supported by their Android devices.
Researchers took over 2000 Android firmware into account, and discovered that over 3500 different types of AT commands are supported on some of the OEM’s devices. Few of the vulnerable OEM’s are – ASUS, Google, HTC, Huawei, Lenovo, LG, LineageOS, Motorola, Samsung, Sony, and ZTE.
The AT commands were able to bypass Android security mechanisms, exfiltrate sensitive device information, perform screen unlocks, and inject touch events and much more.
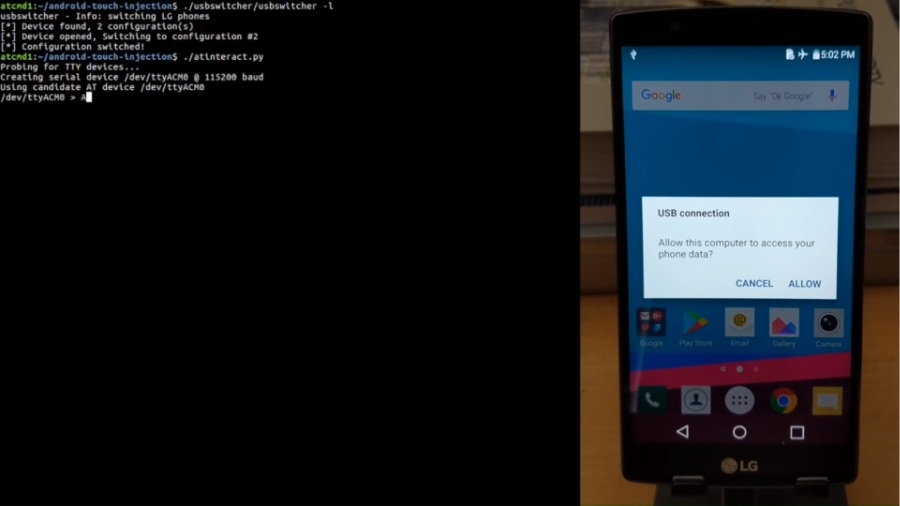
The team used the phone’s USB interface, i.e., the attacker can use USB docks, chargers or charging stations to use phone’s secret AT commands. In other words, the offender needs to possess USB devices or the smartphone itself.
The researchers have already notified the respective vendors and even posted a list of phone models and firmware versions that are exposed to AT commands threat.
An explanatory video is also posed by the team, showcasing LG G4 getting hacked using AT commands injection —