 Short Bytes: Researchers at CyberArk Labs have described a method that shows how an attacker can exploit Windows Safe Mode to steal login credentials. This is possible because Safe Mode only boots with minimal drivers and tools–without third-party security measures. To mitigate the risks, the researchers have advised the sysadmins to take necessary security steps.
Short Bytes: Researchers at CyberArk Labs have described a method that shows how an attacker can exploit Windows Safe Mode to steal login credentials. This is possible because Safe Mode only boots with minimal drivers and tools–without third-party security measures. To mitigate the risks, the researchers have advised the sysadmins to take necessary security steps.
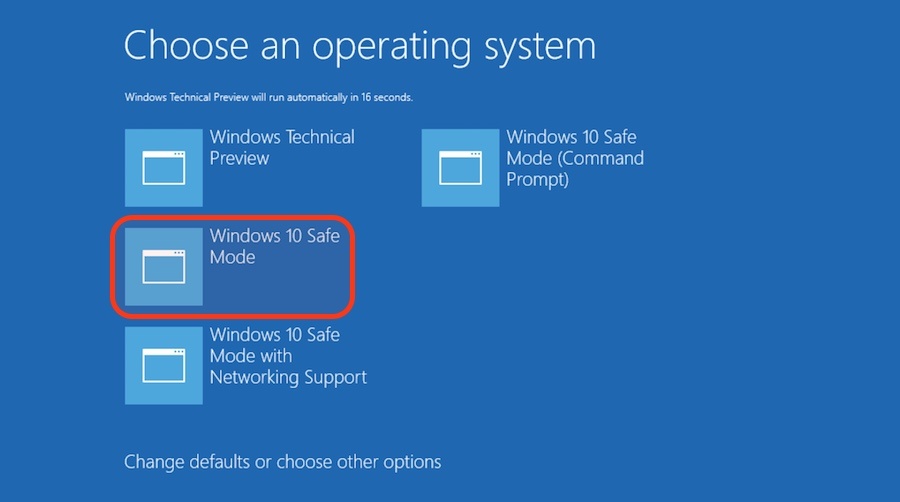
However, in few cases, Safe Mode can turn out to be dangerous. In Safe Mode, an attacker can freely run tools to steal login credentials due to the absence of security measures. The same risk has been outlined by the researchers at CyberArk Labs who have shown how to exploit a Windows PC’s Safe Mode to execute pass-the-hack attacks.
Describing the risk involved, the security researchers explain that once the attackers have remote, local administrative privileges, they need to evade various third-party security measures and Microsoft’s new Virtual Secure Mode. However, these measures only work in Normal Mode.
To complete the hack, an attacker needs to complete these three steps:
Boot a machine in Safe Mode: To force a machine to boot into Safe Mode during the next reboot, attackers can use BCDEdit and change the configuration. This will, by default, boot the machine in Minimal Safe Mode that only runs the minimal Windows drivers and services.
Configure the attack tools to load in Safe Mode: As Widows Safe Mode only loads the necessary drivers and tools, the attacker must enable the attack tools to load in this state. This can by done by creating a malicious service that can be included in the initial payload. The other option explores the possibility of registering a malicious COM object that explorer.exe will load. Using these tools, the attacker can steal the login credentials from LSASS.exe and use them for privilege escalation and further hacking.
Here’s how an attacker can accomplish this attack process:
Rebooting the machine: The next step involves restarting the system to execute the next phase of the attack. To avoid any suspicion, the attack can either wait for the next restart or show a fake Windows update window.
CyberArk Labs reported the risk to Microsoft Security Response Center. However, Microsoft didn’t consider the submission a valid vulnerability as “it needs an attacker to have already compromised the system.”
Given the risks involved, the researchers advise the sysadmins to enforce the principle of least privileges, rotate the account credentials, monitor the use of Safe Mode, and employ the security tools in Safe Mode.
For detailed information on the attack, read CyberArk’s security blog.
Did you find this article helpful? Don’t forget to drop your feedback in the comments section below.
Also Read: Hackers Shows How To Hack Windows And OS X Passwords In 13 Seconds