ICMP, which stands for Internet Control Message Protocol, can broadly be thought of as a receptionist protocol which is responsible for requested pieces of information as well as unrequested information which might be helpful to other protocols and devices operationally.
What is ICMP?
ICMP (Internet Control Message Protocol) is an auxiliary protocol which provides diagnostic information when requested. ICMP can be divided into two broad categories:
- Error reporting and,
- Query
ICMP Error-reporting Messages:
Error reporting messages are generated when, during the processing of any internet packet, a host encounters a problem.
Scenario:
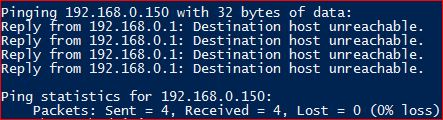
Let’s say you want to send a packet outside of your local area network, but your default gateway is down. In that case, you might have already seen “Reply from x.x.x.x: Destination host unreachable.”
Error Reporting messages
- Destination unreachable
- Source Quench
- Time Exceeded
- Parameter problem
- Redirection
Destination unreachable
The message of “Destination unreachable” is passed to the sender when the receiver could not be contacted, or the packet was discarded because the ultimate destination could not be contacted.
Source Quench:
It is a message from one host to another asking the other host to slow down the speed at which the packets are being sent. Source Quench is one of the ways to control the packet flow on the internet.
Time Exceeded:
Also known as TTL Time Exceeded, this is an interesting message generated using ICMP.
On the basic level, all the packets transmitted through the internet world will have a TTL value. TTL basically stands for “Time To Live”. Iy is a like parameter which decides how long a packet should live before it would be discarded.
But why a packet has to be discarded at all?
A packet has to be discarded because there will be too many packets roaming over the internet world. Sometimes, it might also happen due to bad routing implementation on the network. Due to bad routing implementation, the packets might go into the looping and cause network congestion.
On the other hand, the TTL value keeps on decrementing from one hop to another. Due to looping issue when the TTL value reaches zero, this ICMP message is generated.
Parameter Problem:
Sometimes, problems might not specifically be covered by any ICMP messages. In that case, Parameter Problem is shown.
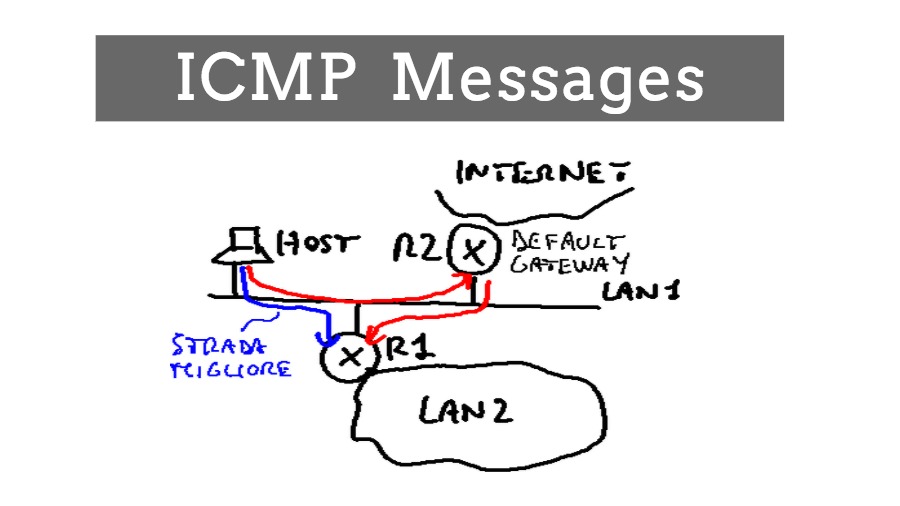
ICMP Redirects:
ICMP redirect messages direct a host to deliver the next packet for the same destination IP address to a different router.
Scenario:
Let’s say I am trying to send a packet to a host on another network. I am also connected to two routers at the same time. However, by default, my machine sends a packet to the default gateway.
Once the default gateway receives the packet, it has to forward the packet to the second router. This is an extra piece of work that the default router has to do. In this scenario, the default router sends me an ICMP redirect message asking me to redirect all the upcoming packets to a different router.
Query Messages:
Query messages, on the other hand, are generated when requested.
Scenario:
You can ping your NIC and you get the reply from the host as seen below.
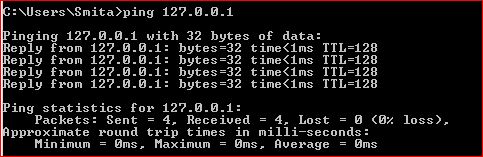
In this case, Ping sends the echo requests and get the echo reply in return.
ICMP Query Messages:
- Echo request or reply
- Timestamp request or reply
- Address mask request or reply
- Router solicitation or advertisement
Echo Request or Reply:
One of the most important things that ICMP query messages are used for is troubleshooting. It can help in identifying problems and diagnosing them.
Echo request or reply scenario
Echo request or reply is the first step towards checking if the destination device is alive or not. To check it, the source device sends an ICMP Echo message to the destination. Upon receiving the Echo request, the destination device replies with “Echo Reply”. Once the source node receives the Echo Reply from the destination, it understands that the remote device is alive.
Timestamp request or reply:
As we know that the whole of the internet world is operating in different geographical zones with different time zones as well, some of the applications need synchronization of the time stamp before they start, such as live video. In that case, ICMP timestamp request and reply messages are used to sync up the timings.
Address Mask Request or Reply:
Address Mask request or reply is used for finding out the subnet address of the destination network where the packet has to be sent.
Router Solicitation or Advertisement:
There are many routing protocols where the routers have to rely on each other’s routing table to find out the shortest path.
So, if there is an update in the routing table of a router, those updates are communicated or advertised via the ICMP messages only. Not only the routing table update but messages are also communicated via ICMP messages between two routers.
Why ICMP?
Before we try to understand why ICMP, let’s have a look at the IP (Internet Protocol). We already know that the internet protocol is the main protocol in the IP suites. However, this protocol still lacks certain functionalities which are required in the internet communication. Being an unreliable protocol, IP is not concerned with the error checking and error control.
Thus, not only ICMP but other protocols were created to compensate for the missing functionalities in the IP, such as ECN protocol.
These error reporting protocols work on top of the IP layer but just below the Transport layer. So, they are kind of sandwiched between these two protocols.
The reason why these are placed on top of the IP layer is that they can report any error. The best scenario to get an error caught will be after the data has been transmitted.
If you are more interested in the networking, read our complete coverage on computer networks.