Remember the movie “Mission Impossible” where the protagonist, Tom Cruise bypassed a security system using body heat signatures left on the keyboard? Well, that is actually happening in 2018.
A new attack discovered by a group of researchers let hackers steal your passwords by recording thermal residue left on the keyboard after you walk away from it.
The researchers based out of the University of California, Irvine (UCI) concluded that entire password could be recovered within a time span of 30 seconds of the first key being entered using a thermal imagining camera. And partial keywords can be retrieved in under one minute.
According to the published report “Thermanator,” the researchers attached a FLIR thermal imagining camera 25 inches away from the four standard PC keyboards by Dell, HP, AZiO Prism KB507 and Logitech. The UCI team say that the Thermanator attack can be used to recover verification codes, ATM pins, and even long strings of text.
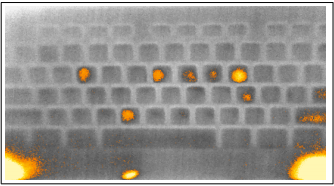
The “hunt and peck” typists (pressing each key individually while looking at the keyboard) are more vulnerable to password stealing since they take longer completion times, which leaves longer time for keycaps to cool off before recording begins.
On the other hand, Touch typists (typing without the use of sight, or just by feeling the keyboard) were challenging to capture heat signatures “since a typical Touch typist’s fingers are always in contact with the home-row (middle row encompassing ASFD and JKL;) of the keyboard.
The Thermanator attacks will soon become reality as the thermal imagining camera will become more and more affordable in the future. At present, FLIR cameras range from $100,000 to $400, and lower end ones can be attached to any Android smartphone.










