Arch Linux software repository named Arch User Repository (AUR) has been infected by malware. As many as three Arch Linux packages available on the repository have been reported to contain malware.
The repository has user-submitted packages, and that is how the malware was released in the repository. A user named “xeactor” took over an ‘orphaned’ package going by the name of “acroread” which functions as a PDF viewer and added a malicious code.
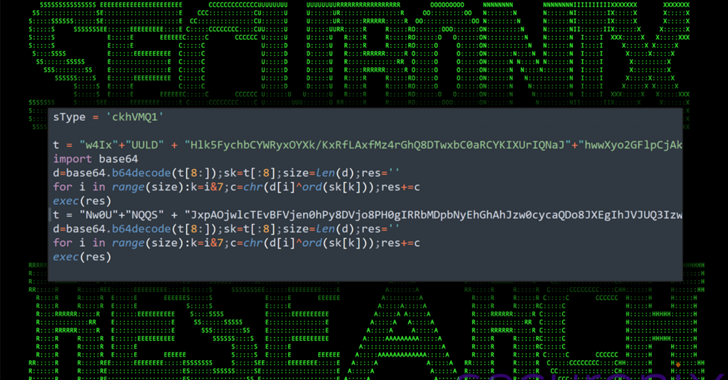
As per Git commit, “Xeactor” added a code that would download a script which in turn would install software that meddles with “systemd” and reconfigure it. This script would run every 360 seconds.
The malware intended to collect the data of the infected system including date, time, machine’s ID, package manager details, CPU information and outputs of “uname-a” and “systemctl list-units” commands. The collected data would be posted in a new Pastebin file.
Two other packages were also infected in a similar manner. Even though it does not pose any serious threat to the infected computers, it is anticipated that “xeactor” could launch another malware as any self-update mechanism was not included.
After discovering the malware, the changes done in the packages were rolled back, and the AUR team has suspended “xeactor.”
However, this malware attack raises serious concerns over the credibility of user-submitted package repositories. Earlier this year, the Ubuntu Store Team also found a cryptocurrency miner hidden in an Ubuntu package.