Short Bytes: More than a dozen Telegram accounts were compromised leading to the identification of 15 million users’ cell number. Two researchers were able to point out this mass hacking campaign being carried out and have hinted the involvement of Rocket Kitten group behind this.
Short Bytes: More than a dozen Telegram accounts were compromised leading to the identification of 15 million users’ cell number. Two researchers were able to point out this mass hacking campaign being carried out and have hinted the involvement of Rocket Kitten group behind this.
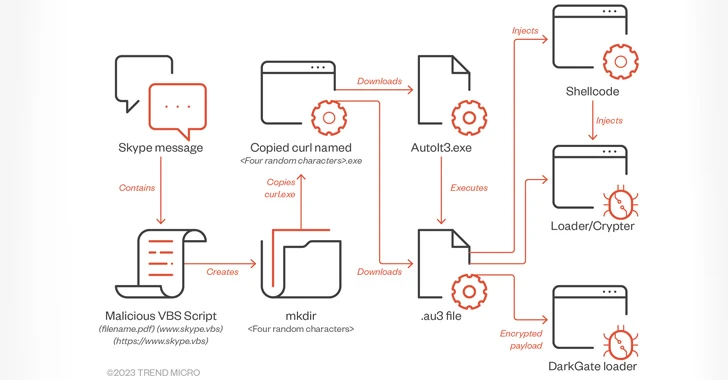
Two researchers, an independent cyber security expert Collin Anderson and Claudio Guarnieri, were able to detect the security breach which utilized the two-factor SMS verification used by the Telegram app for adding a new device to a user’s account. The hacker, who has access to the SMS data of a device, could add his own device to the account and gain access to the data. Like this, more than two dozen user accounts were hacked.
The berlin-based Telegram stores the data in the cloud. It offers end-to-end encryption the users just like Facebook’s Secret Conversations in Messenger and WhatsApp platform.
Is the politics involved in Telegram hack?
The SMS verification process is a common multi-factor authentication implemented across various apps and services just like Telegram has done.
But, how these messages reach the phone? Through the cell phone company’s servers.
“We have over a dozen cases in which Telegram accounts have been compromised, through ways that sound like basically coordination with the cellphone company,” said Anderson.
The researchers didn’t rule out the possibility of the government-backed cellphone company acting as the greedy cat in the picture. The cat might be responsible for finding the details of the mice.
“The individuals that are targeted [in these Telegram hacks] are individuals who are human rights activists, they’re opposition figures, they’re individuals tied with people who are currently in jail or under house arrest or these sorts of things,” Anderson said.
“The fact that they’re going after these individuals shows that this is part of a larger understanding of the opposition environment inside of the country.”
A Telegram Spokesperson Markus Ra said that “if you have a strong Telegram password and your recovery email is secure, there’s nothing an attacker can do”.
Maybe the users can add an extra layer of security but in reality, 15 million cell numbers have been exposed.
The tale of the Kitten!
Rocket Kitten is a hacktivist group which is presumed to be behind this mass exposure campaign. The researchers have pointed to the Persian-language references in the code to relate the involvement of the Rocket Kitten group. The hacker group has been linked to the Revolutionary Guards in the past and the researchers have analyzed the similarity in the operations.
Telegram’s API is publically available and researchers said that same was used to identify the people against their cell numbers, whether they exist on Telegram or not. The mass identification carried out by brute forcing the numbers to the API to get the user ID. Telegram has disabled the ability to perform mass checks in the API.
Reuters writes,
Cyber experts say Iranian hackers have become increasingly sophisticated, able to adapt to evolving social media habits. Rocket Kitten’s targets included members of the Saudi royal family, Israeli nuclear scientists, NATO officials and Iranian dissidents, U.S.-Israeli security firm Check Point said last November.
— With inputs from Wired and Reuters
If you have something to add, tell us in the comments below.
Also Read: These Are The Programs Used By ISIS To Remain Anonymous On The Web