Short Bytes: Another day, another CIA hacking tool reveal. Wikileaks has published fresh documents that deal with the CIA’s hacking and spying on Linux machines using a malware strain called OutlawCountry. This tool consists of a kernel module that creates invisible netfilter table for creating new rules with iptables command. This way the operator is able to modify and redirect the network traffic.
Following the CIA’s Brutal Kangaroo malware which hacked offline and air-gapped computers using USB drives, WikiLeaks has leaked another CIA hacking and spying tool called OutlawCountry. Interestingly, unlike the previous tools, OutlawCountry targets Linux machines.
This new malware strain’s details have been leaked in the form of a user manual, which describes that OutlawCountry tool consists of a kernel module for Linux 2.6, using which CIA can modify the network traffic and redirect it for ex- and infiltration purposes.
The OutlawCountry’s prerequisites for operation are a compatible 64-bit CentOS/RHEL 6.x operating system, shell access and root access to the target, the target must have a “nat” netfilter table.
Brief working of OutlawCountry
The working of OutlawCountry hasn’t been described in detail in the document. The operator of this Linux malware loads the module via shell access to the target. After it’s loaded, the module creates a new Netfilter table with some obscure name.
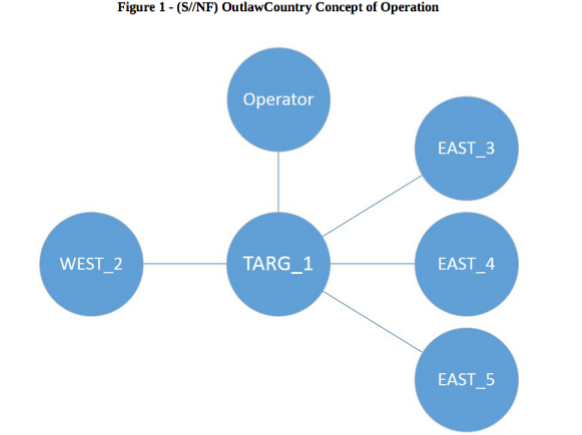
The newly created table allows certain rules to be created with the help of “iptables” command. The new rules get priority over the older rules and are only visible to a person if he/she knows the name of the table. The table gets removes when the hacker removes the kernel module. ” Also, OutlawCountry v1.0 only supports adding covert DNAT rules to the PREROUTING chain,” WikiLeaks writes.
Talking about the network traffic modification, as you can see in the picture above, the OutlawCountry module is loaded on the target (TARG_1). After this step, a CIA hacker may add more hidden iptables rules to play with the network traffic between EAST and WEST networks. For e.g., the traffic from WEST_2 to EAST_3 could be redirected to EAST_4 or EAST_5.
You can read further details about OutlawCountry in this user manual.
Don’t forget to check out our complete Vault 7 coverage.










