From November 9, Wikileaks has started a new series named Vault 8. As a part of this series, the first leak contains the source code and analysis for Hive software project. Later, the other leaks of this series are expected to contain the source code for other tools as well.
In its press release, Wikileaks has hoped that the new publication will help investigative journalists, forensic experts, and people to understand CIA and its components.
As per the documents, Hive acted as a major tool for CIA’s malware operators as it helped them communicate with the sophisticated malware implants in the wild in a secure manner.
Even if the target detected the malware implant, it was difficult to attribute the same to CIA due to the use of covert communications to send information to CIA servers and get new instructions.
Hive could act as multitasking tool by taking care of multiple implants on target computers. The front ends of the operation were cover domain whose servers acted as a relay for a hidden CIA server named Blot, which passed traffic over VPN.
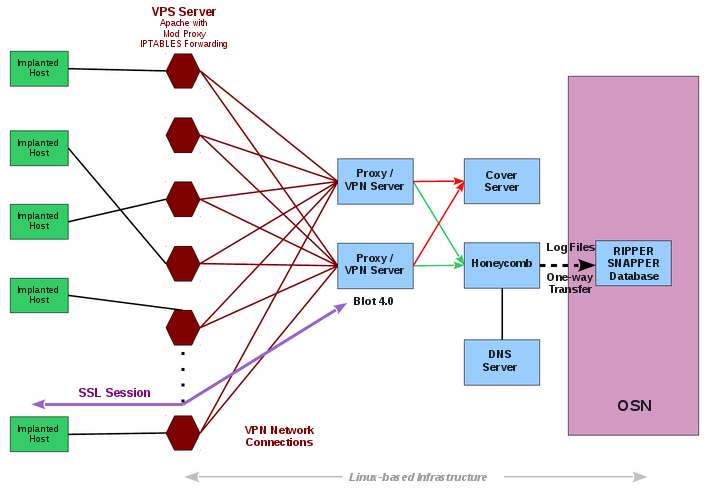
In case a visitor stumbled on the website, everything seemed normal. However, Hive used an uncommon HTTPS server option Optional Client Authentication which doesn’t need any authentication from user’s side.
“Traffic from implants is sent to an implant operator management gateway called Honeycomb while all other traffic go to a cover server that delivers the insuspicious content for all other users,” Vault 8 leak mentions.
In an interesting development, it was also found that CIA also wrote code to impersonate Kaspersky Labs antivirus company and build fake certificate.
You can read about Hive malware control program here and find leaked documents as well.










