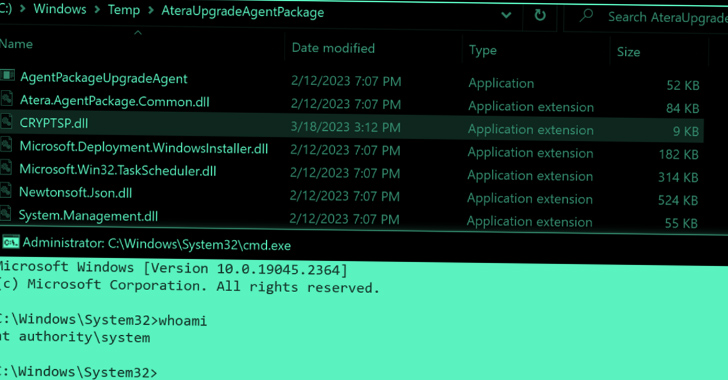
A zero-day vulnerability for Tor browser was revealed yesterday on Twitter by Zerodium — a company that buys and sells exploits in software.
Zerodium published the details of the vulnerability which was present in the Firefox extension NoScript (built-in to the Tor browser), which prevents web pages from executing JavaScript, Flash, or Silverlight.
Advisory: Tor Browser 7.x has a serious vuln/bugdoor leading to full bypass of Tor / NoScript ‘Safest’ security level (supposed to block all JS).
PoC: Set the Content-Type of your html/js page to “text/html;/json” and enjoy full JS pwnage. Newly released Tor 8.x is Not affected.— Zerodium (@Zerodium) September 10, 2018
Even though NoScript is supposed to block all JavaScript at its “safest” security level, but there is a backdoor that can be exploited by attackers to suppress NoScript and run malicious codes anyway.
However, this bug can be exploited in Tor Browser 7.x only and the recently released Tor Browser 8.x is unaffected by this bug.
The reason behind it is the change of Tor’s codebase from the older Firefox core to the new Firefox Quantum platform. The new add-on API’s in it protects version 8 from this vulnerability.
Besides the NoScript add-on was rewritten last year to make it compatible to the new Firefox Quantum platform. This is why the zero-day exploit in question does not work on the new Tor Browser 8.x series.
Following the revelation by Zerodim, a latest NoScript “Classic” version 5.1.8.7 has been released by the company to stop the zero-day’s exploitation vector.
I said FIXED, guys ?
Get 5.1.8.7 here:https://t.co/0h5BHFexTw— Giorgio Maone (@ma1) September 10, 2018
Meanwhile, Tor Project has issued an official statement to ZDNet:
Nevertheless, it is advisable for Tor users to either install the NoScript update or switch to Tor Browser 8.x for better security.