IVRE (Instrument de veille sur les réseaux extérieurs) or DRUNK (Dynamic Recon of UNKnown networks) is a network recon framework, including tools for passive recon (flow analytics relying on Bro, Argus, Nfdump, fingerprint analytics based on Bro and p0f and active recon (IVRE uses Nmap to run scans, can use ZMap as a pre-scanner; IVRE can also import XML output from Nmap and Masscan).
Currently the framework support the following features:
- Scan & sniff – Nmap and Masscan included to run scan during penetration testing against subnet , whole country or a specific range of IP addresses. It can use Zmap for a fast pre-scan, and collect info from network traffic (passively) using Bro, Argus, Nfdump & p0f.
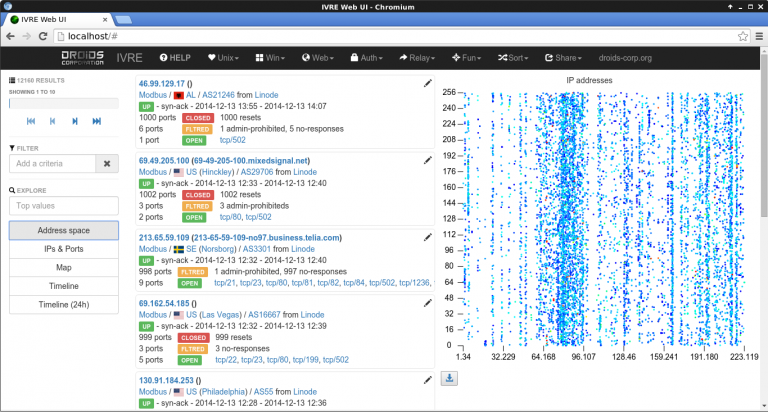
- Browser – Use the CLI tools, the Python API or the Web interface to browse the results. Filter, look for specific services or vulnerable versions, within a specific country or network, quickly access to previous results for a specific host, etc.
- Analyze – Make the best of your scan results to identify similar hosts and corner-cases. Look for most (and least) common ports, services or products, and get a quick overview of the address space with the “heatmap”
- Flow analysis – IVRE comes with a handy interface to browse network flows.
- Count open ports and top ports open on a remote service detected
Get started in no time.
Thanks to Docker and Vagrant, running IVRE is (almost) as easy as typing vagrant up.
$ mkdir -m 1777 var_{lib,log}_mongodb ivre-share
$ wget -q https://ivre.rocks/Vagrantfile
$ vagrant up --no-parallel
Bringing machine 'ivredb' up with 'docker' provider...
Bringing machine 'ivreweb' up with 'docker' provider...
Bringing machine 'ivreclient' up with 'docker' provider...
[...]
$ docker attach ivreclient
root@e809cb41cb9a:/#
Also read: Reconnoitre – Multithreaded Recon and Enumeration Tool
If you are an Arch Linux user, there is an AUR package, that should be easy to install: something like yay -S ivre ivre-web should work. If you use BlackArch Linux, IVRE should be installed and work out of the box. If not, just run: pacman -S ivre ivre-web.
IVRE is also packaged in Pypi, and you can use Pip to install it: pip install ivre.
While both AUR and Pypi packages are built for each release, Docker images are built automatically from the Github repository and follow the development version, just like AUR ivre-git packages.
You don’t want to use Docker, Archlinux or Pip? The documentation includes a step-by-step installation procedure, that should be easy to adapt to any Linux / Unix-like system.
You can read more and download this framework over here: https://ivre.rocks/