OpenVAS is a full-featured vulnerability scanner. Its capabilities include unauthenticated testing, authenticated testing, various high level and low level Internet and industrial protocols, performance tuning for large-scale scans and a powerful internal programming language to implement any type of vulnerability test.
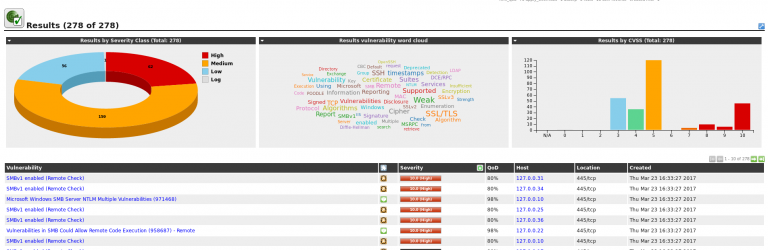
The scanner will provide a dashboard with information about vulnerabilities detected in the infrastructure, list of scanned assets and the vulnerabilities that were recently published by different vendors.
Configuration tab will allow to configure different options related to scan schedule and required reporting beside the scan profile with service scan requirement.
This utility is an important part to run the vulnerability management program and have a periodic status on each vulnerability discovered and to confirm the one that were properly patched.
Why would I use the OpenVAS scanner?
The primary reason to use this scan type is to perform comprehensive security testing of an IP address. It will initially perform a port scan of an IP address to find open services. Once listening services are discovered they are then tested for known vulnerabilities and mis-configuration using a large database (more than 53000 NVT checks). The results are then compiled into a report with detailed information regarding each vulnerability and notable issues discovered.
Once you receive the results of the tests, you will need to check each finding for relevance and possibly false positives. Any confirmed vulnerabilities should be re-mediated to ensure your systems are not at risk.
Vulnerability scans performed from externally hosted servers give you the same perspective as an attacker. This has the advantage of understanding exactly what is exposed on external facing services.
How does the hosted OpenVAS process work?
1. Enter the target to scan
Depending on your goals and the target being tested; enter an IP address, a range of IP addresses (PRO membership required) or hostname. Different targets can be entered as a list to run as separate jobs or as a single job for a consolidated report.
2. Select scan type
Multiple options are available depending on the type of system to be tested.
Full Scan for a full test of network, server and web application vulnerabilities.
Web Server Scan a more focused test for web server and web application vulnerabilities.
WordPress Scan testing for known WordPress vulnerabilities and web server issues.
Joomla Scan testing for known Joomla vulnerabilities and web server issues.
3. Launch the Vulnerability Scan!
Testing will begin and the target system(s) will be probed in order to discover vulnerabilities that could place the system at risk of compromise. Results will be available from 15 minutes to a number of hours depending on the target selection.
You can read more and download the latest version over here: http://www.openvas.org