BadKarma is a GUI based network reconnaissance tool that can gather useful network information at any stage of the penetration testing process. The tool is loaded with some top level reconnaissance and active scanning modules, such as nmap, masscan, shodan, searchsploit, metasploit, dnsrecon, dnsenum, and Whois information resource. The user can select any of these modules during the penetration testing process to collect valuable information about the target hosts.
BadKarma Installation

Before installing BadKarma, install the dependencies as follows:
apt install python3-pip python3-gi phantomjs mitmproxy ffmpeg gir1.2-gtk-vnc-2.0 gir1.2-gtksource-3.0 gir1.2-vte-2.91 gir1.2-osmgpsmap-1.0 gir1.2-webkit2-4.0

It is highly recommended to run the update command before installing the dependencies.
sudo apt-get update
Once all the dependencies are fulfilled, clone the toolkit git repository and install the requirements using the following commands.
git clone https://github.com/r3vn/badKarma.git cd badKarma pip3 install -r requirements.txt

Running BadKarma
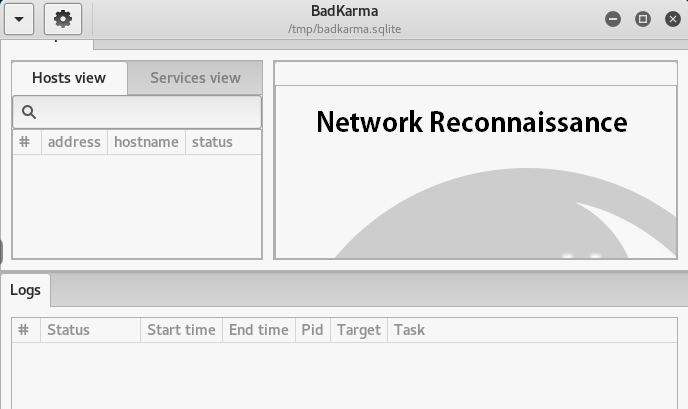
The following commands open the BadKarma GUI window as shown in the following screenshot.
chmod +x badkarma.py ./badkarma.py

We can see the BadKarma dashboard is loaded with different tabs, such as Hosts view, Services view, and Logs. The hosts view tab shows the target hosts information like host IP, hostname, and its status. The services tab shows the running services on the target. One of the selected modules performs the scanning to identify the running services on the target hosts. The logs tab stores the session information about the target hosts. There is a dropdown arrow option in the top left corner of the toolkit. By clicking the dropdwon menu, we see the option of adding the target for reconnaissance. The overall dropdown options can be seen in the following screenshot.

If we click on the add target(s) option from the dropdown menu, a window pops up, requiring the IP address of the target host and the scanning tool to initiate the scanning process. If no other tool is selected, BadKarma uses nmap as the default scanning tool.

Once the target IP is provided, the selected tool starts gathering information about the target host. The target IP address, hostname, and status information is displayed in the Hosts view tab of the tool.

The services tab contains the information about the detected ports, ports state, their types, and the running services. We can run different scanning options by clicking any port, as shown in the following screenshot.

Besides network machines, we can also scan web applications, gaining useful information as shown below.

What Bunny rating does it get?
BadKarma is efficient in scanning target network hosts to capture valuable information like banner grabbing, DNS information, ports status, and running services on the target hosts. The toolkit can also scan the web applications for desired information. However, the toolkit does not provide any concrete information for smart devices that are part of the network. As a result we will be awarding this tool a rating of 3.5 out of 5 bunnies.