Cr3dOv3r is an open source tool that helps in finding credentials reuse attack for any specific email address. The tool makes use of the ‘haveibeenpwned’ API to find the possible leaks for the provided email address. The tools also searches for the plaintext password against the provided email address. Cr3dOv3r also tests the provided credentials’ security through login attempts into popular websites like Google, Yahoo, and Facebook etc.
How do I install this leet speak tool Cr3dOv3r?

Cr3dOv3r is compatible with Windows, Linux, and MacOS. The tool requires Python 2.x or above to operate. Cr3dOv3r can be installed by cloning the package from github repository using the following command.
git clone https://github.com/D4Vinci/Cr3dOv3r.git
Cr3dOv3r required packages can be installed using the following command. If you are running a Python version other than 2.7, replace the version according to your installed Python package in the following command.
Python2.7 -m pip install -r win_requirements.txt

Enough of this baloney, lets Get Started with Cr3dOv3r!
Cr3dOv3r can be set into action using the following command:
cd Cr3dOv3rpython2.7 Cr3d0v3r.py -h
The above command starts the tool and displays the available options that can be set as arguments in the commands.
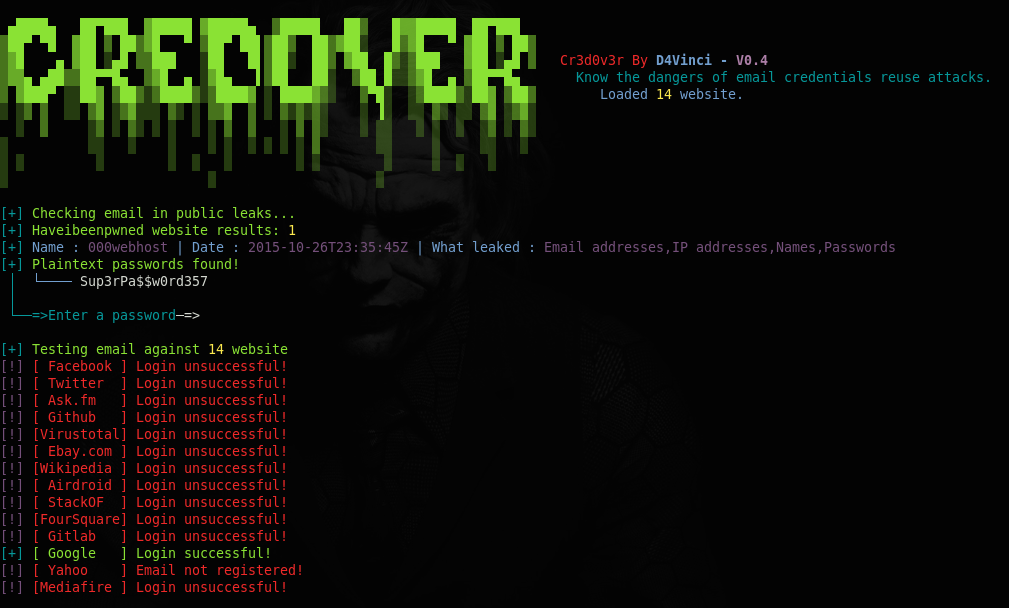
Let’s find out if our targeted email address is misused or the associated password has appeared in any leaks. The task can be performed using the following command.
Python2.7 Cr3d0v3r.py –q <targetted email address>
The -q argument represents quiet mode (no banner) in the scanning process. The tool looks for the use of the provided email address on different websites and displays the results as shown in the following screenshot.

If there is no leak found publically, the tool asks for credentials (passwords) to perform a login attempt (registration check) for different well-known websites, this could be particularly useful for Red team engagements where credentials have been found elsewhere. If credentials are used somewhere else, they are displayed in the results as shown in the following screenshot.

We have a networking hacking course that is of a similar level to OSCP, get an exclusive 95% discount HERE