Dirhunt is a python tool that can quickly search directories on target domains to find interesting directories and file locations. The URL’s can further be analyzed through offensive security tools. Dirhunt has multiple scanning features. Web developers may create an empty index files to hide certain files/data. Dirhunt can detect those blank index files. It can also distinguish between real and fake 404 error codes on the target domain.
Other features include extracting interesting URLs from the ‘index of’ pages, finding all the redirectors on a target domain, and processing multiple target domains simultaneously. Dirhunt supports proxies to stay anonymous and flags to filter the scan results. All the supported flags can be found using the –help command while running the tool.
Dirhunt Installation
Dirhunt can be installed by running the setup.py file from Dirhunt directory. First clone Dirhunt from Github using the following path.
git clone git://github.com/Nekmo/dirhun

After cloning Dirhunt, move to the Dirhunt directory and run the installation file using the following commands.
cd dirhunt python setup.py install

Dirhunt can also be installed using the Pip command.
sudo pip3 install dirhunt
Running Dirhunt
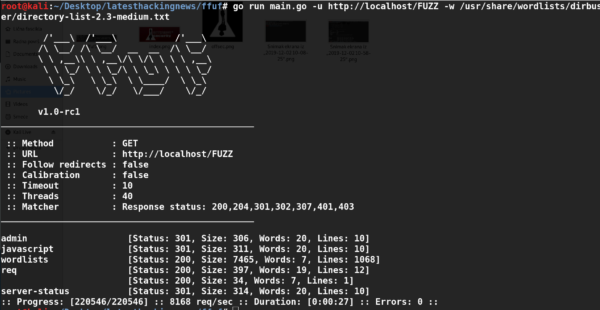
The following command runs Dirhunt on the target domain and finds the directories and urls that can be helpful in further analyzing the security of the domain.
dirhunt <target url>
For instance, by running Dirhunt on the following test domain, we see many interesting urls that can further be used in security analysis of the target host.
dirhunt http://testphp.vulnweb.com/
The results show that Dirhunt has found some interesting php files that can further be analyzed for penetration tests.

For instance, by further analyzing the /categories.php path, we find urls that are vulnerable to cyber-attacks. For example, /categories.php shows a url (http://testphp.vulnweb.com/listproducts.php?cat=4) that seems vulnerable to SQL injections. We can test the security of this url by running SQL injection tool (sqlmap) as shown below.
python sqlmap.py –u http://testphp.vulnweb.com/listproducts.php?cat=4
While performing the sql injection tests on the url, it has been found that the domain is vulnerable to SQL injection and XSS attacks.

What Bunny rating does it get?