Habu is an open source penetration testing toolkit that can perform various penetration testing tasks related to networks. These include ARP poisoning, ARP sniffing, SNMP cracking, fake FTP server creation, DHCP starvation, DHCP discover, Certificates (SSL/TLS) cloning, Denial of service attacks, TCP port scanning, TCP Flag analysis, social engineering, virtual hosts identification, and web technologies identification.
Habu Installation

Habu is python tool that requires python3 and the following packages to be installed.
cryptography
beautifulsoup4
dnspython
click
lxml
prompt_toolkit
regex
requests
pygments
requests-cache
websockets
scapy-python3
matplotlib
Matplotlib is an optional library that can be used to draw graphs of findings and analysis.
Habu can be installed using the following command.
pip3 install habu
The above command installs Habu toolkit and the packages. The alternate way of installing Habu is through cloning the toolkit from github repository and installing the dependencies using pip.
Network Penetration Testing with Habu
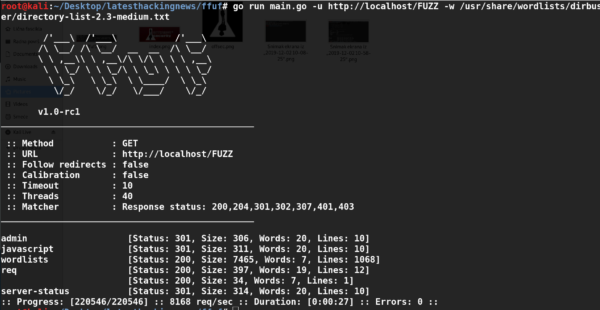
Habu can be run directly from the terminal with the desired test command. As mentioned above, Habu can be used for a number of network penetration testing tasks. For instance, we can run Habu for network sniffing using the following ARP command.
habu.arp.sniff

Similarly Habu can be used as an MITM framework using the following command to poison the network traffic using the ARP poisoning feature of the toolkit.
habu.arp.poison <victim’s ip address >
The above command allows the toolkit to manipulate the Address Resolution Protocol (ARP) table of the victim’s machine to redirect the traffic to the attacker’s machine. Packet forwarding must be enabled on the attacker’s machine in order to work as a router to send and receive the traffic. The above command can also be run with different optional flags like preferred interface (-i), verbose mode (-v) etc.
habu.arp.poison <optional flags> <victim’s ip address>
Habu can be used to get control of a web browser using the following command.
habu.jshell
![]()
The toolkit listens for a HTTP connection on a default port (3333). If the connection is established, one can send a JavaScript code to open the Websocktet on the target host. Once the Websocket is opened, the browser comes under the control of the attacker who can run any desired command.

There are various other Habu commands that can be run in a similar fashion to test the network security.
What Bunny rating does it get?