Red Hawk is an open source tool that is used for information gathering and certain vulnerability scanning. Red Hawk detects Content Management Systems (CMS) in use of a target web application, IP address, web server record, Cloudflare information, and robots.txt data. Red Hawk can detect WordPress, Drupal, Joomla, and Magento CMS. Other scanning features of Red Hawk include WHOIS data collection, Geo-IP lookup, Banner grabbing, DNS lookup, port scanning, sub-domain information, reverse IP, and MX records lookup. As a vulnerability scanner, Red Hawk looks for error based SQL injections, WordPress sensitive files, and WordPress version related vulnerabilities.
Red Hawk Installation
Red Hawk tool can be cloned from Gihtub using the following command.
git clone https://github.com/Tuhinshubhra/RED_HAWK

Using Red Hawk
After installing Red Hawk, move to the RED_HAWK directory and run rhawk.php file to launch the tool.
cd RED_HAWK php rhawk.php

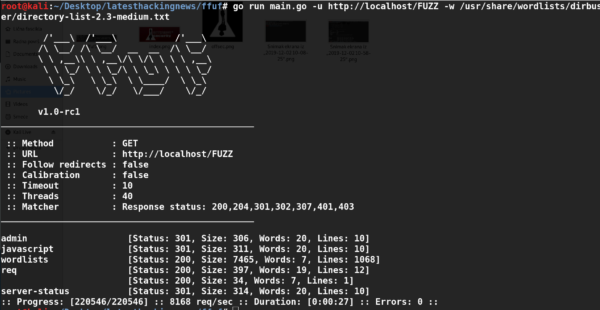
The command launches the tool and asks for the target web application. Upon providing the target web address, Red Hawk gives the information gathering and vulnerability scanning options as shown in the following screenshot.

Choose the desired scanning (or vulnerability assessment) option by typing the utility sequence number in the action field. The tool responds by fetching results according to the selected Red Hawk utility. For instance, we can use basic web scanning by selecting its sequence number in the following format.
[#] Choose Any Scan or Action From the Above List: 0
In response to above action, Red Hawk fetches basic web information like site title, assigned IP address, web server technology and version, cloudflare, and Robots.txt file.

Banner grabbing task can be performed in the following format.

Similarly, we can use Red Hawk to find open ports and running services on the target web applications.

What Bunny rating does it get?