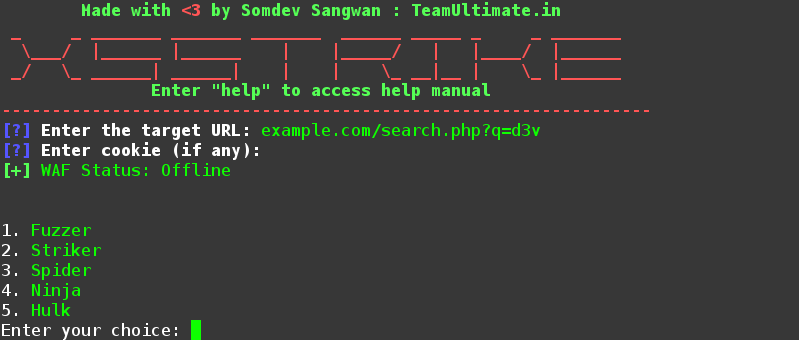
XSStrike is an open source tool that detects Cross Site Scripting vulnerabilities and exploits them. The tool is equipped with a powerful fuzzing engine that increases the accuracy of the tool. The promising features of the tool include the following.
- XSStrike is equipped with a powerfull fuzzy engine for accurate results.
- The tool possesses context breaking technology.
- GET and POST methods are supported in case no parameters are provided in target urls.
- The tool is capable of gathering the web applications firewalls information during the scan process.
- The tool uses levenshtein algorithm that increases the tool’s accuracy.
- Custom payloads are supported by the tool to avoid any specific WAF.
- Cookie support is also available.
- Bruteforcing feature for the blind XSS is also part of the tool.
- The tool possesses an efficient encoding engine.
XSStrike Installation

XSStrike is a python3 tool that can be cloned from github using the following command.
git clone https://github.com/s0md3v/XSStrike
XSStrike requires the following packages to operate.
Fuzzywuzzy
python-Levenshtein
prettytable
requests
The ‘pip install –r requirements.txt’ may not work in the case of XSStrike. Try to install the packages using the pip3. Each package can be individually installed as follows.
pip3 install fuzzywuzzy pip3 install python-levenshtein pip3 install prettytable pip3 install requests
Running XSStrike
XSStrike can be executed using the following command.
python3 xsstrike
The tool asks for a target url upon loading. The url may contain some parameter to be tested by the tool. Once the url is provided, the tool asks for an optional cookie information. After setting up the url and the cookie information, the tool also gives the option to look for the additional hidden parameters. If more hidden parameters search option is ignored, the tool starts scanning the provided url for possible XSS attacks with the provided parameter.

Similarly, if a url is provided to XSStrike without any parameters, the tool gives the option to test the target url using GET or POST arguments. By selecting GET or POST argument along with the argument data.

XSStrike also generates a series of custom payloads to be tested manually by replacing the url parameters. If any payload matches the XSS requirement, the tool takes over the target website.
What Bunny rating does it get?