The Group Policy Editor is one of the many important features of the Windows 10 Pro version that Home users never get to see. Although Windows 10 Home consists of the Registry Editor as a replacement, it is nowhere near the Group Policy Editor.
Most Windows Settings tweaks can be accomplished by forcing values on the Windows Registry. However, at times there are certain procedures which can only be efficiently achieved via a Group policy management console in Windows 10. Not to mention, Registry Editor can be pretty dangerous and could generate an irrevocable result.
Let’s see what exactly is Group Policy Editor and how we can access a local group policy editor in the Windows 10 Home version.
What is Group Policy Editor (gpedit.msc) in Windows 10?
Group Policy is a way for administrators to apply a bunch of Windows Settings changes from a single computer. Group Policy on a Windows computer includes different options for registry-based policy settings, security settings, software installations, scripts, computer startup and shutdowns, user logon and logoff, and folder redirection.
With the help of Group Policy, a single admin can reduce the cost of ownership by controlling the number of PC’s. A set of Group Policy configurations is called a Group Policy Object (GPO). For example, one can use a particular configuration to block access to a task manager or restricting access to certain folders.
A version of Group Policy Editor is the Local Group Policy Editor, which is used to enforce GPO’s in standalone computers. On Windows 10, the Local Group Policy Editor can be used to edit policies for groups as well.
Differences Between Local Group Policy Editor and Registry Editor
If you look at the functionality of both editors, Local Group Policy has the upper hand. This is because a Local Group Policy Editor in Windows 10 populates the Registry Editor with registry values.
If you edit a Group Policy, changes are automatically applied to Registry. However, if you edit Registry values while the Group Policy is forced, the value will be overwritten to its original state until the Group Policy Editor specifically makes the changes.
Group policy on Windows 10 periodically refreshes the Registry at certain intervals to keep the Registry values in check at all times. Generally, the update interval ranges from 30 minutes to 90 minutes. However, it can also be changed to certain limits.
Since Group Policy Editor is absent from Windows 10 Home, its functionality is only limited to Windows Pro and Enterprise users.
How to open Local Group Policy Editor in Windows 10?
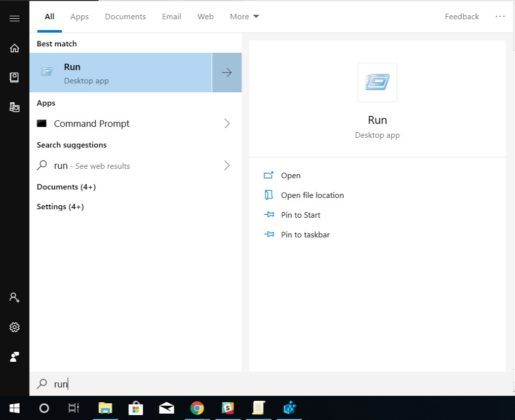
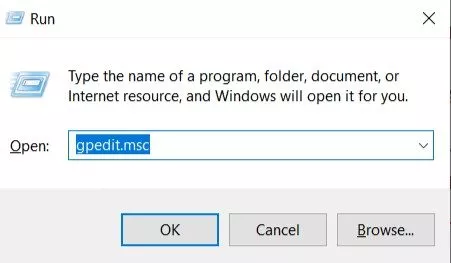
For Windows 10 Pro and Enterprise users, opening up Group Policy Editor is a piece of cake. Open Run Command via Windows Search > Type “gpedit.msc” > Click on Ok.
The problem lies with Windows 10 Home users who don’t are not provided with the Group Policy Editor. Here I have listed a two-step method to get gpedit working on your Windows 10 device.
How to Get Local Group Policy Editor on Windows 10 Home?
1. Download and install gpedit on Windows 10 Home
Kudos to iTechtics that have come up with a direct gpedit enabler for Windows 10 Home users. Under this method, you only have to run the file as administrator and install it.
![]() Gpedit.msc for Windows 10 Home Edition
Gpedit.msc for Windows 10 Home Edition
As you might have guessed, this ridiculously easy method of running and installing “gpedit.msc” on Windows 10 Home comes with a catch. It only works on some Windows PC’s.
Sometimes, Windows 10 asks you to install older Microsoft NET Framework versions (v2.0 and v3.0) for completing the setup.
2. Copy Group Policy Files to another system folder
If the first method doesn’t work out, download the Gpedit Installer program from Majorgeeks. Now, try running the Local Group Policy Editor via the Run Command.
If it says there is no such file as “gpedit.msc”. Then —
- Head over to this following address or you can directly paste it into Windows search as well.
“C:WindowsSysWOW64”
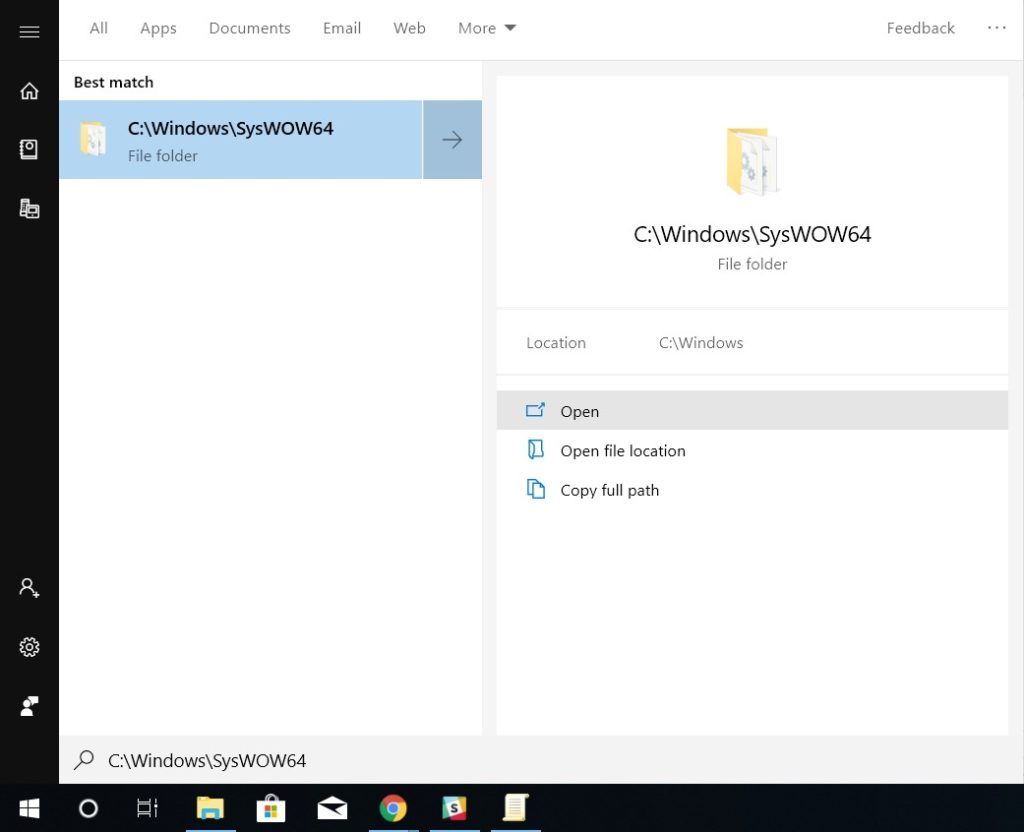
- Copy “Group Policy” folder, “GroupPolicyUsers” folder and “gpedit.msc” file
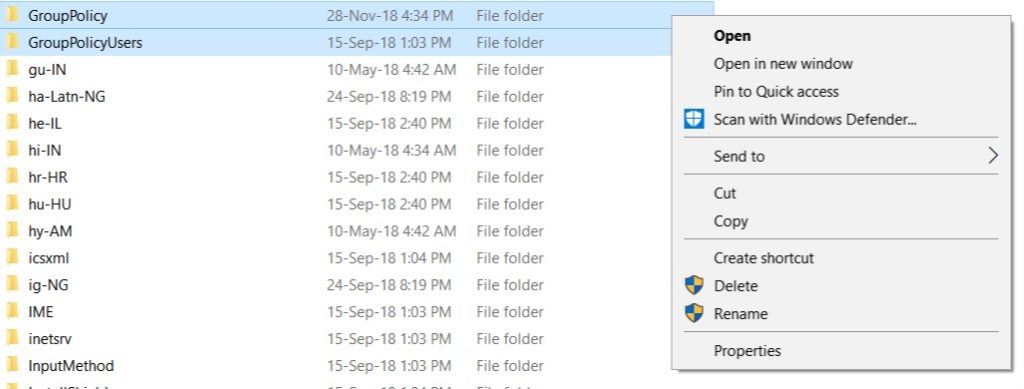
- Now, head to C:WindowsSystem32 and paste all the copied items in the System 32 folder.
If you are getting the error “MMC could not create the snap-in,” then —
- Go to Windows Search
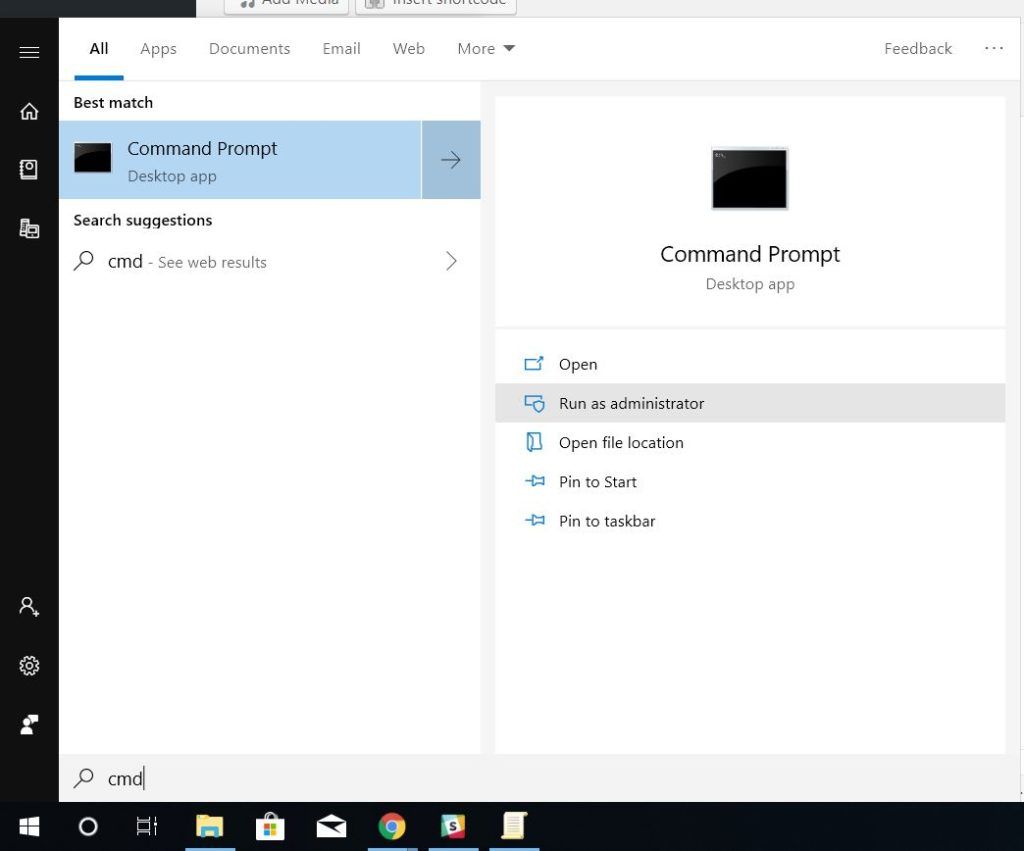
- Type CMD > Click on “Run as Administrator”
- Type “cd/” and hit Enter > “cd Windows” and hit Enter > “cd temp” and hit Enter > “cd gpedit” and hit Enter > x64.bat and hit Enter
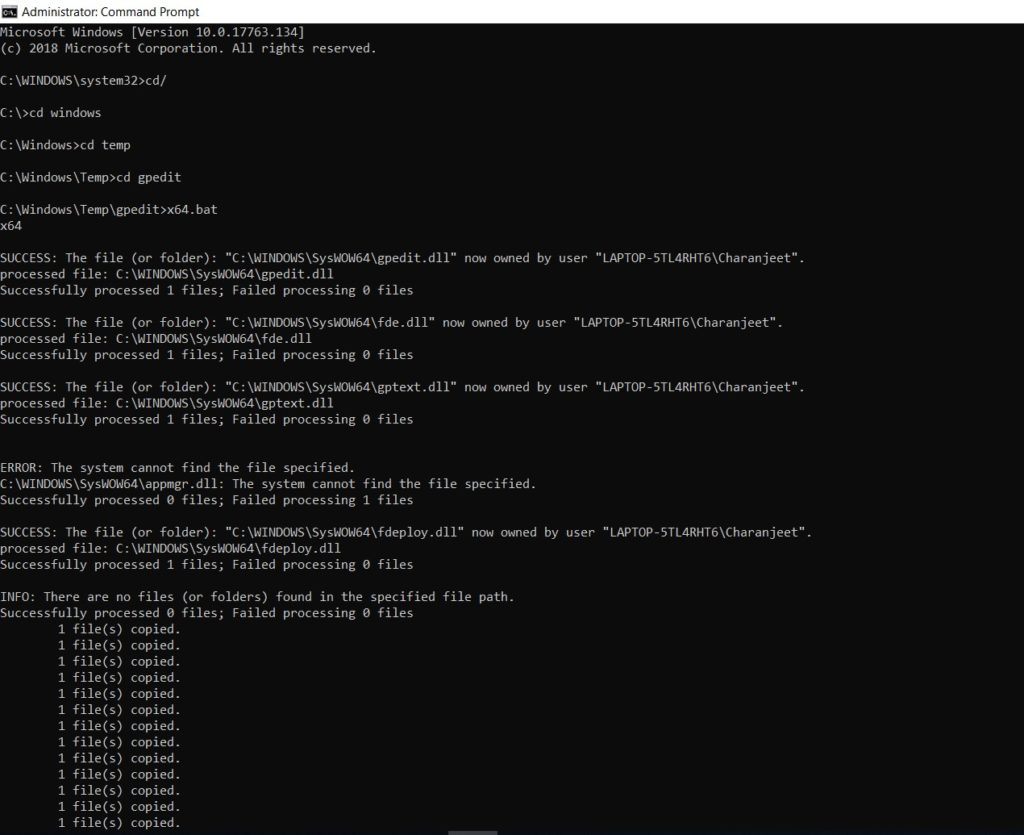
Cool Windows 10 tweaks you can do using Local Group Policy Editor (gpedit.msc)
Here are a lot of Windows settings that you can tweak with the help of the group. Policy Editor —
I’ll soon prepare more Group Policy Editor tweaks and add them soon. So, make sure to bookmark this article. Also, comment if the above methods of enabling gpedit worked for you.