The US Department of Justice (DOJ) announced that charges will be filed against Julio Lugo and Rosenide Venant, accused of operating a complex fraudulent scheme through false statements to a financial institution; Lugo also faces charges for illegal use of economic stimulus programs for coronavirus. In case of being found guilty the defendants face sentences of up to 30 and 45 years in prison.
Authorities argue that in late March 2020, defendants began conspiring to commit fraud against the U.S. Small Business Administration (SBA), seeking improper economic stimulus.
Lugo and Venant would have used their home IP address to file about 70 false and fraudulent loan applications for funds from the Paycheck Protection Program (PPP) and the Economic Injury Disaster Loan Program (EIDL).
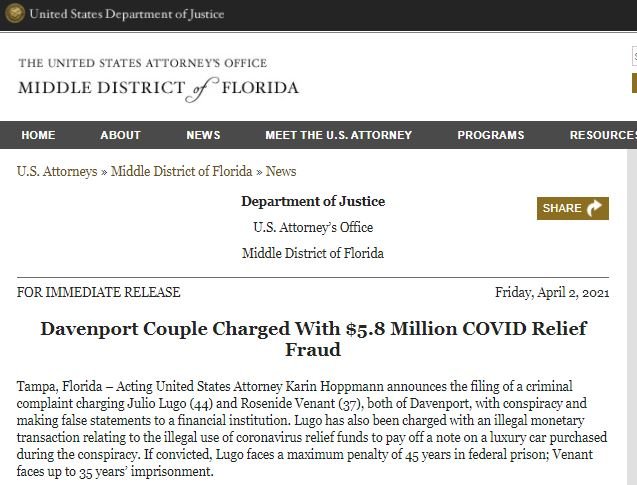
In total, the scammers requested $5.8 million USD, including registering some phantom companies to apply for government subsidies.
An important part of this fraudulent scheme was a phantom company that Lugo would have used in 2015 for tax fraud. Once some loans were obtained, the conspirators misused PPP and EIDL funds, either by paying for luxury vehicles, spending tens of thousands of dollars on casinos and expensive clothing.
This scheme began to be planned from the passage of the Coronavirus Aid, Relief and Economic Security Act (CARES), which came into force in March 2020 and was designed to provide emergency financial assistance to millions of Americans and mitigate the economic impact of the pandemic. The federal government authorized up to $350 USD billion in small business loans so they can meet their obligations to workers.
Soon after, Congress authorized an additional $300 USD billion to continue economic stimulus to the most affected sectors in society.
It should be mentioned that this process is at the complaint stage, which means that it is simply a formal charge that a defendant has committed one or more federal crimes, bearing in mind that each defendant is presumed innocent unless proven otherwise.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.