In its latest alert, the Federal Bureau of Investigation (FBI) mentions that the financially motivated cybercriminal group known as FIN7 has been attacking the U.S. defense industry, sending malicious USB devices with the LilyGO logo to some employees; these devices are loaded with a powerful ransomware variant.
The cybercriminals reportedly used the U.S. Postal Service (USPS) and the United Parcel Service (UPS) network to ship BadUSB or Bad Beetle USB devices, used to obtain an entry point to potentially affected organizations.
The agency details how the attackers of the attack posed as members of Amazon and the U.S. Department of Health and Human Services (HHS), tricking affected users into opening the packages and connecting these devices to their work computers.
To get users to connect the USB device, hackers pretend they contain government files on COVID-19 measures, or fake gift cards for online services.
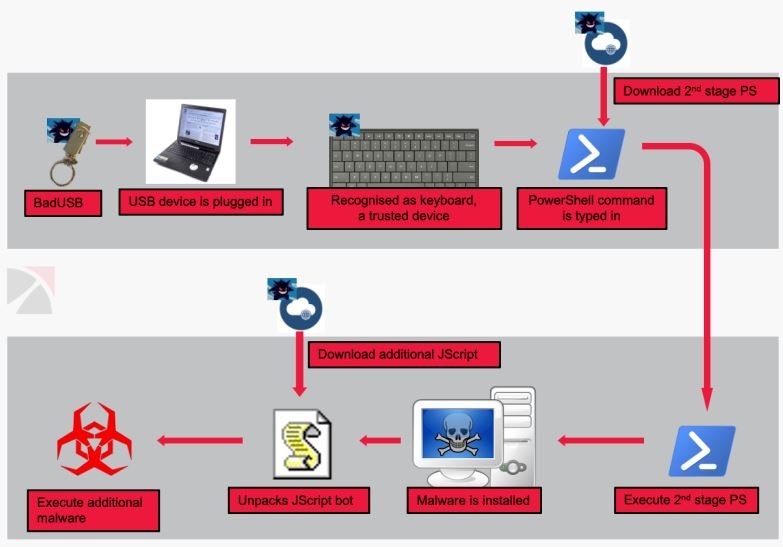
When victims connect these devices to their computers, the affected computer is registered as a Human Interface Device (HID) keyboard, which will allow the device to work even with the unused malicious USB devices. Once this configuration is done, hackers inject keystrokes to install malware payloads.
As mentioned above, the main goal of this campaign is to inject various ransomware variants into the affected systems. To do this, hackers use tools such as Metsploit, Cobalt Strike, the Griffon backdoor and some PoweShell scripts, in addition to ransomware variants such as BlackMatter and REvil. At the moment the real scope of the attack is unknown, although it is not ruled out that there are hundreds of organizations affected.
This report comes after the FBI detailed an operation in which FIN7 posed as Best Buy to send similar packages with malicious flash drives through USPS to hotels, restaurants and retailers. Reports of such attackers began to emerge in February 2020, stretching for nearly two years.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















