A devastating cyberattack was recently detected against SITA, a company that provides IT services for more than 90% of the world’s airlines. The incident led to a massive data breach that impacted more than 4 million users, and was attributed to a group of threat actors of Chinese origin tracked as APT41.
The incident, reported in early March, impacted major carriers such as Singapore Airlines and Malaysia Airlines, although at the time it was reported that the names of all affected carriers had not yet been revealed, at least so far. This week, Air India confirmed that its systems were compromised due to a cyberattack.
Nikita Rostovcev, security analyst at Group-IB, reported this severe incidente and shared details about hackers’ malicious activity.
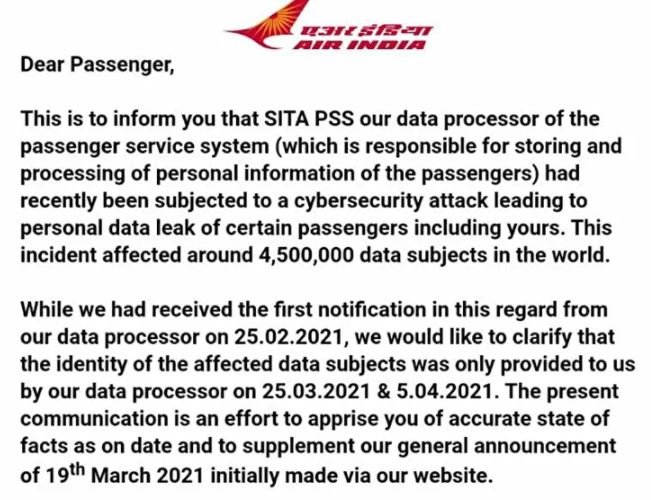
Air India initially confirmed the incident in late May, although there was no clear information about the aftermath of the attack until Group-IB identified this incident as part of the engagement at SITA. According to Rostovcev, it took cybercriminals only 24 hours to spread the malicious payload of Cobalt Strike across the affected network after the initial compromise.
Shortly after the airline confirmed the intrusion, a post appeared on the dark web announcing the sale of a database allegedly associated with Air India. The vendors were demanding $ 3,000 USD in exchange for releasing access to this compromised information.
Although the first analyzes suggested that the leak was not legitimate, a subsequent investigation confirmed that the database was real and the information had been extracted by a hacking group sponsored by an unnamed state actor. The investigation also showed that the hackers sent Air India information to a C&C server and then began to move laterally through the compromised network. Group-IB identified at least 20 devices connected to the Air India network infected during this attack.
Regarding the attacking group, APT41 specializes in the deployment of cyber espionage campaigns and electronic fraud. A recent report from the U.S. Department of Justice (DOJ) notes that, during the last 12 months, this group provided other groups with the source code, certificate signatures and information necessary for the deployment of multiple attacks.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.