LastPass, which is owned by GoTo (formerly LogMeIn), said that the hackers got into its network in August and utilized information stolen from the first attack to return and steal client data. The information stolen during the first theft included company names, end-user names, billing addresses, email addresses, telephone numbers, and the IP addresses from which users were using the LastPass service.
According to a notice that was released on Thursday by the chief executive officer of LastPass, Karim Toubba, the unknown attacker was also able to copy a backup of client vault data from an encrypted storage container. This information was disclosed in a notice.
The exposed container had both unencrypted data, such as website URLs, and completely encrypted sensitive fields, such as usernames and passwords for websites, secure notes, and data that had been filled out on forms. The exposed container was accessed by a third party.
From the latest update about the data leak at LastPass:
To this day, we have come to the conclusion that once the cloud storage access key and the dual storage container decryption keys were obtained, the threat actor copied information from the backup that contained fundamental customer account information and associated metadata. This information included company names, end-user names, billing addresses, email addresses, telephone numbers, and the IP addresses from which customers were accessing the LastPass service.
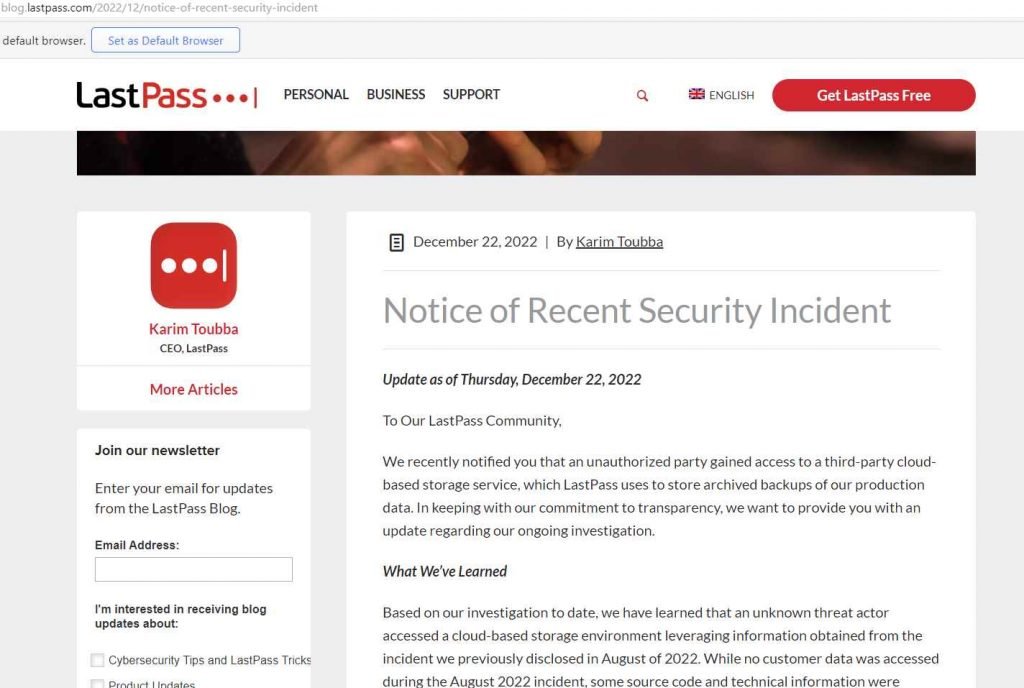
The threat actor was also able to copy a backup of customer vault data from the encrypted storage container. The customer vault data is stored in a proprietary binary format that contains both unencrypted data, such as website URLs, and fully-encrypted sensitive fields, such as website usernames and passwords, secure notes, and form-filled data. The threat actor was able to copy the backup of the customer vault data from the encrypted storage container.
The chief executive officer of LastPass is adamant that the encrypted fields will continue to be protected by 256-bit AES encryption and that they will only be able to be decrypted with a one-of-a-kind encryption key that is derived from each user’s master password by using the so-called zero knowledge architecture of the company.
However, he cautioned that the threat actor may try to decrypt the copies of stolen vault data by using brute force to guess a user’s master password and decrypt the copies of the data that were stolen.
Toubba issued a warning that the threat actor might also target consumers with phishing attempts, credential stuffing, or other forms of brute force assaults against online accounts that are connected with your LastPass vault.
The organization strongly recommends to its customers that they should not reuse master passwords on other websites.
Additionally, LastPass alerted a tiny portion (less than 3 percent) of its business clients to propose that those customers take particular measures depending on the individual account setups of those business customers.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.