A cyber-espionage group linked to the Russian military has developed Android malware which it used to infect the smartphones of Ukrainian soldiers and track Ukrainian field artillery units, according to a report released today by Crowdstrike.
The report from the same security firm that discovered the “alleged” Russian hack of the Democratic National Committee (DNC) servers in April 2016.
According to CrowdStrike, the group behind the Android malware that targeted Ukrainian military forces is named Fancy Bear, one of the two groups involved in the DNC hack, albeit the other group, named Cozy Bear, was far more active.
Group has ties to Russia’s military
Based on multiple reports from several security firms across the globe, the Fancy Bear group appears to have ties to the Russian military intelligence service GRU.
The Fancy Bear group is also identified under several other names in different cyber-espionage reports. Across time, the group has been referenced to as Strontium, APT28, Sednit, Pawn Storm, but most of the time has been named Sofacy.
Sofacy is also the name of its primary espionage tool, a remote access toolkit (RAT), also known as X-Agent.
The Sofacy (X-Agent) malware is unique because it was developed by the Fancy Bear group, and only deployed in its cyber-espionage operations, and nowhere else.
Crowdstrike finds Android version of the group’s native malware
Until know, security firms that have analyzed the group’s activity have found Windows, Mac OS X, and iOS variants of this RAT.
According to Crowdstrike, things changed over the summer when Crowdstrike analysts discovered an Android app that contained a new breed of malware which employed the classic X-Agent communications protocol, seen only in the original Sofacy (X-Agent) malware.
After taking a deeper look at the Android app, researchers discovered that this was a clone after an application created by an officer of the Ukrainian military, the 55th Artillery Brigade, named Yaroslav Sherstuk.
Speaking to Sherstuk, Crowdstrike learned that he created the app in order to automate some mathematical computations needed to calibrate D-30 Howitzer cannons used by the Ukrainian artillery.
The officer said he created the app in 2014 and distributed to other officers of the Ukrainian military, but without hosting it on the Google Play Store. He estimated the app’s initial userbase at around 9,000 installations.
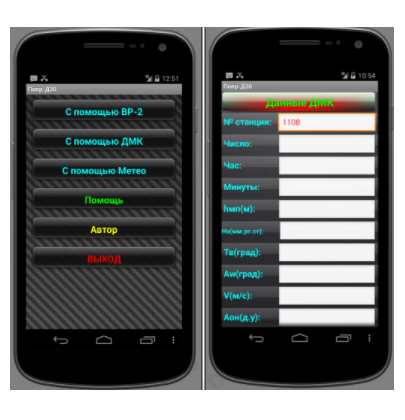
As the conflict in eastern Ukraine evolved towards a military engagement, somewhere along the way, Fancy Bears operators took a copy of this app, injected it with their malware, and spread it online by posting links to the infected version on various Ukrainian military forums.
It appears that before Crowdstrike found the app, several Ukrainian military forces might have installed the application, with dire consequences.
Ukrainian army lost 80% of its D-30 Howitzer guns
According to independent reports, Ukrainian forces lost 50% of all their artillery weapons in the last two years, since the war started in 2014. Most conspicuous is that Ukraine lost 80% of its arsenal of D-30 Howitzer guns.
The Sofacy malware’s Android variant has the ability to spy on its victims by transmitting geo-location data back to the Fancy Bears servers.

While Crowdstrike hasn’t discovered smartphones belonging to Ukrainian artillery personnel infected with the Sofacy malware, drawing the line between the existence of this malware and the rebels’ efficiency at destroying D-30 guns is a conclusion at which many third-party observers would reach.
Furthermore, this is one of the few cases when cyber-espionage groups were found to operate on a live battlefield, instead of lurking in the shadows and collecting data from foreign businesses and politicians.
Source:https://www.bleepingcomputer.com










