Every cybersecurity workflow starts from log data collection and management, that’s why SIEM Tools is highly demanded among enterprises that strive to maintain a stable security posture and comply with necessary regulations.
This overview offers a brief look at the top 5 SIEM vendors for the beginning of 2022, both on-premises and cloud-native depending on the infrastructure. Find out about their distinctive features to choose the best security solution perfectly tailored to your organization-specific needs.
Best SIEM Tools 2022
- Microsoft Sentinel
- Google Chronicle Security
- Splunk
- IBM Security QRadar
- ArcSight
Microsoft Sentinel

Microsoft Sentinel is a best SIEM Tools that enhanced version of the preexisting on-premises SIEM Microsoft Azure Sentinel which also supports cloud-based functionality. As a result, the number of available ingested events has grown to over 20 billion daily.
New features include:
- Query performance has become 12 times faster than in the previous version and up to 100 times faster in some particular cases
- Iteration speed of features set now executes at a faster rate
- The use of out-of-the-box connectors allows easier data ingestion
- Microsoft provides simplified training and onboarding of security engineers for an easy start with the platform
- The newly implemented Azure Security Center playbook automates over 800 Azure subscriptions and soon is about to include 20,000 additional subscriptions
Overall, Microsoft Sentinel is one of the powerful and best SIEM Tools that offers high performance and needed agility for all kinds of organizations, from small businesses to large-scale enterprises. Its powerful capabilities for creating analytics rules, hunting, and incident response with playbook support ensure a high level of automation, often demanded by complex networks.
Google Chronicle Security

This security analytics platform is built on Google’s infrastructure which gives this platform an edge over its competitors. Chronicle Security offers a cloud-based elastic container for storing enterprises’ security telemetry. The data integrity is provided by built-in threat signals along with automation capabilities.
Some of the other services include:
- The integration of the largest malware database in the world by VirusTotal Enterprise
- The improved speed of threat discovery and investigation (within seconds)
- Reduced rate of false positives and elimination of the triaging for speeding up threat hunting and detection
- Retroactive correlation of log data with backing from threat intelligence sources such as Avast and AVG
- Ingestion of large data sets, as well as indexing, correlating, and analyzing in a matter of seconds
Backed by Google’s core infrastructure, Chronicle Security provides a number of services that work together at maximum speed. Security event and information management, as well as extensive threat detection and analysis, are available driven by the ability of processing petabytes of data on a whim. Chronicle is also compatible with popular cybersecurity solutions like SOC Prime’s Detection as Code platform for collaborative cyber defense, threat hunting, and discovery that helps security teams address the challenges of building custom use cases while making threat detection easier, faster, and more efficiently.
Splunk

Splunk is an American tech company that produces one of the SIEM Tools for searching, monitoring, and analyzing machine-generated data via a Web-style interface. Organizations can choose the most applicable setup depending on their infrastructure with the same capabilities available in the cloud or on-premises. Splunk Enterprise covers the needs of on-premises SOCs while Splunk Cloud is suitable for cloud and hybrid architectures. This software is infinitely scalable and effectively deals with big data. Splunk can be installed quickly and is compatible with multiple platforms.
This SIEM is capable of monitoring and searching through vast amounts of data from the organization’s log sources. Next, the information gets indexed and correlated within containers that make it available for search. It is also possible to automatically generate alerts and reports with a detailed visualization.
Splunk provides improved security operations like customizable dashboards, an asset investigator, statistical analysis, as well as incident review, classification, and investigation.
Key characteristics:
- Works both with cloud and on-premises log sources
- Allows quick threat detection
- Enables automated actions, workflows, and event sequencing
- Includes the functionality of an asset investigator, statistical analysis, and incident review
Splunk is packed with a lot of useful functions. It’s one of the popular SIEM Tools used across a wide variety of industries by startups and large-scale businesses alike. Plus, it delivers customizable dashboards so any SOC team can create one that suits their needs and particular system architecture. For added efficiency and speed, engineers may use the SOC Prime CCM App, both for Splunk Cloud and on-premises to continuously stream new detection rules directly into their environment and update the existing ones.
IBM Security QRadar
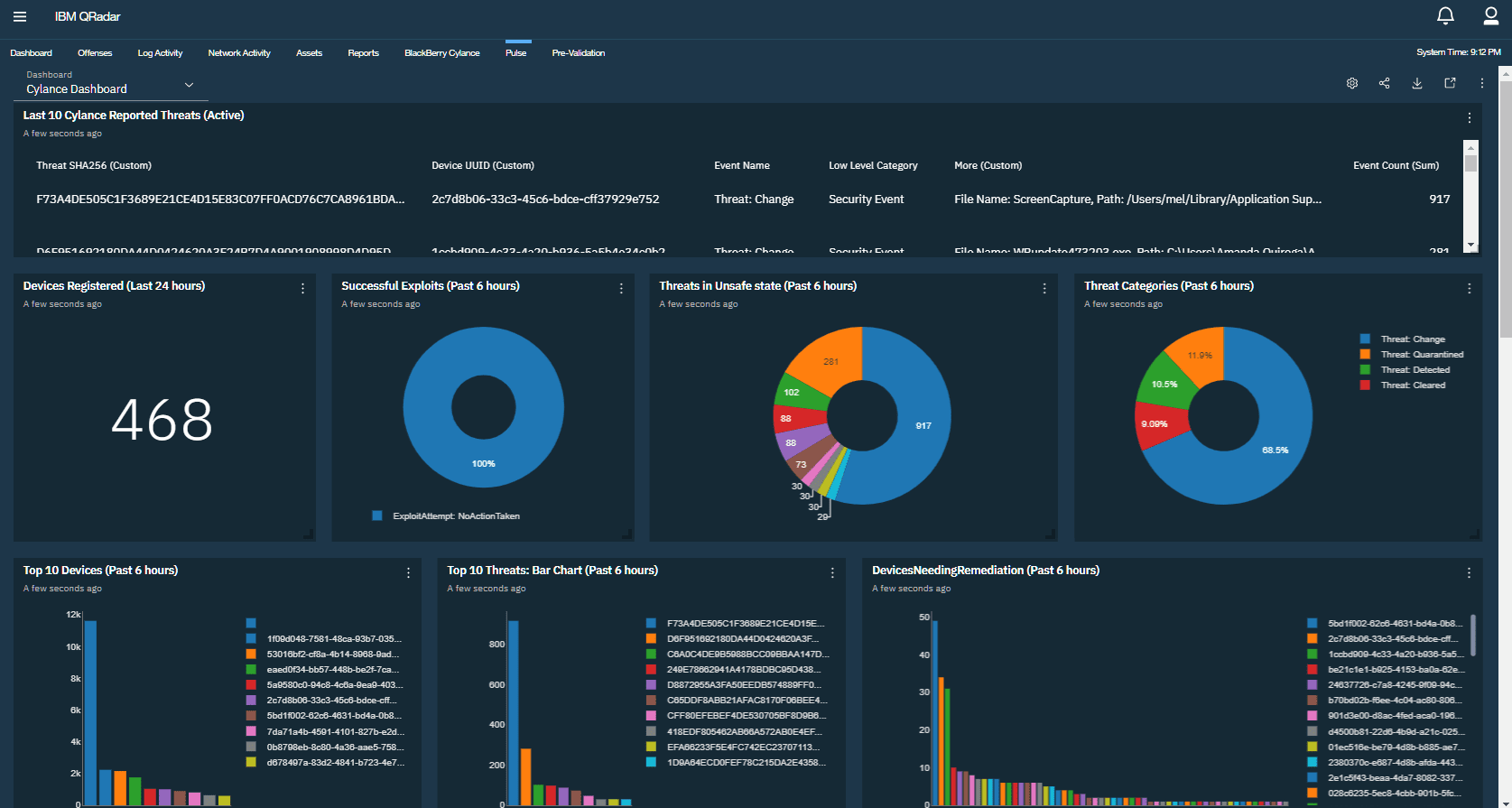
QRadar SIEM is available both on-premises and in cloud environments. SOC teams can connect a whole network of configured devices, apps, workstations, and servers to collect log data. It also helps to ensure accurate threat detection and run prioritization.
The software ingests and correlates data from endpoints, cloud, networks, and users against the latest threat intel feeds. Advanced security analytics helps to track down threats at every stage of the kill chain.
Prominent features:
- Supports multiple logging protocols
- Provides AI-powered investigations
- Runs intelligent root cause analysis
- Includes zero-trust model
- Generates reports with visualizations
QRadar delivers a number of useful features that can be further enhanced by integrating other IBM security products. It helps to reduce the manual workload by automation and prioritization.
ArcSight

ArcSight Enterprise Security Manager (ESM) is one of the SIEM Tools that scalable solution for collecting, correlating, and reporting on security event information. It collects data from more than 500 types of log sources. Its scalable data collection framework unlocks visibility across the entire organization’s network. The aggregation, normalization, and data enrichment enable the performance of advanced security analytics throughout the appliance, software, and cloud environments.
Besides the standard ingestion and interpretation of log data, ArcSight offers threat intelligence, security alerts, compliance reporting, and real-time correlation through intuitive user interface dashboards. The product is compatible with other security tools from ArcSight such as User Behavior Analytics.
Recent enhancements to ESM include:
- Distributed correlation via distributed cluster technology
- Baselining and outlier mechanism notification
- Integration with machine learning algorithms
- Compliance with GDPR
- Default content and customizable rule sets
- Community marketplace support
- Asset, network, user, and vulnerability modeling with geo-location
ArcSight is a highly scalable SIEM solution that is popular among large enterprises and suitable for a wide range of cybersecurity environments. Generally, it provides high-speed performance combined with effective threat blocking.