GrayKey’s code snippets recently appeared online and an unknown party was responsible for the publishing. The iPhone unlocking specialist GrayShift is now being extorted for paying 2 bitcoin, the price of one GrayKey box, but it is believed that the extortionists might have run out of codes.
GrayKey is a device developed by GrayShift and it has been creating headlines ever since it was publicly disclosed. The tool is claimed to be able to unlock almost any iPhone running any iOS version including the iPhone X using the brute-force attack technique. Oddly enough, the device is the apple of the eyes of law enforcement officials as they have become the top buyers of this costly tool priced between $15,000 and $30,000.
However, much to their dismay, the company itself became a victim of data breach since an unknown party obtained GrayKey code snippets and started publishing them online one-by-one. Now the hackers are demanding 2 Bitcoin as ransom.
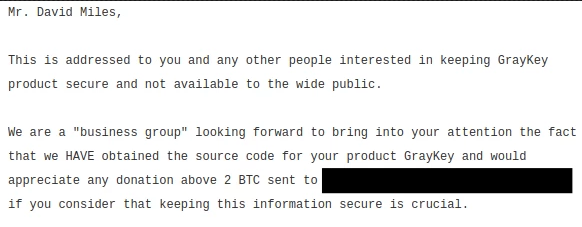
According to Motherboard, the message posted by the hackers and addressed to the co-founder of GrayShift read: “Mr. David Miles, This is addressed to you and any other people interested in keeping GrayKey product secure and not available to the wide public.”
However, this message was deleted from the website hosting it. After a day, another message was posted, which is still available online. It reads:
“We are a ‘business group’ looking forward to bring into your attention the fact that we HAVE obtained the source code for your product GrayKey and would appreciate any donation above 2 BTC [~$19,000 on Tuesday].”
GrayShift has confirmed that the data has been stolen and the code was lifted from a customer’s website where the UI of GrayShift’s units got exposed to the internet for a short duration earlier in April.
“During this time, someone accessed the HTML/Javascript that makes up our UI. No sensitive IP or data was exposed, as the GrayKey was being validation tested at the time. We have since implemented changes to help our customers prevent unauthorized access,” the company’s official statement revealed.
The company believes that hackers might not have collected any meaningful data and therefore, the ransom hasn’t been paid yet. Moreover, the posted code is also not that interesting and seems like it is the code for operating the display on the device that shows messages to a user.
Until now the extortionists haven’t been paid the ransom since the Bitcoin addresses they provided GrayShift for payment of ransom don’t have any funds as yet.
This is not the first time when an iPhone cracking device manufacturer has suffered such breach. Previously, Israeli smartphone craking firm Cellebrite was hacked and 900 GB of its data was stolen. The data was not only leaked online it also confirmed the in-house hacking capabilities of Cellebrite.
Image credit: Depositphotos