Hacking Facebook credentials such as login IDs and passwords have always remained the apple of the eye for cybercriminals and malicious threat actors. In a newly identified scam, a malicious app is being used to obtain user credentials directly from the targeted devices. This is accomplished via new Android malware dubbed as Android.Fakeapp.
This time around, the scammers have employed a rather aggressive approach to stealing Facebook login credentials by directly stealing data from the devices, which are mostly detected in Asia-Pacific region. The malware is being sourced from third-party markets and English speaking users are the primary targets in this campaign.
According to Symantec’s findings, when malware is installed, the user cannot suspect anything out of the ordinary because the app hides from the home screen and the service run in the background. A number of steps are undertaken by this service to steal credentials from a Facebook user’s account, which include checking for a prospective Facebook account that is to be targeted by obtaining the IMEI (International Mobile Equipment Identity) number to the C&C server.
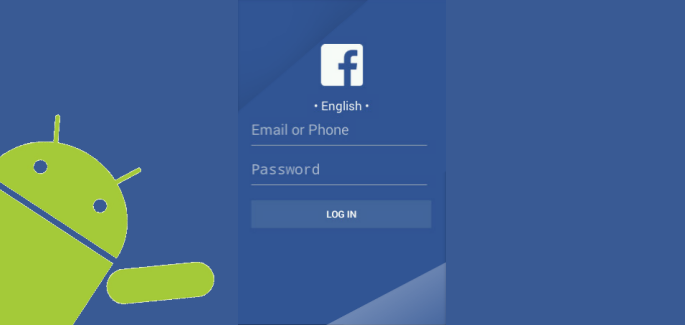
In case there isn’t any account to target then it launched a fake Facebook login user interface after verifying the installed app to obtain user credentials. This user interface is displayed occasionally until login credentials are acquired. The compromised Facebook account is accessed through a JavaScript from a hidden WebView and it is hidden by setting the display to be on transparent.
Furthermore, the malware ensures that CAPTCHA isn’t available and if it is then it sends the information to the C&C server after which caches and cookies are removed and malware again attempts to perform its given task. After it manages to log-in to the targeted Facebook page it manages to leverage a varied array of activities; it can remove the user’s private data as well as data of the contacts and transmit it to the C&C server.
In this regard, the malware adopts a step-by-step approach in which general data is fetched immediately, which includes the user’s login ID, password and device IMEI number. Then it switches attention to the profile details including contacts, education, work, basic information about family and relationships and locations. Lastly, it targets other activities such as friends, groups, pages, posts, likes, check-ins and events related information.
These tasks are achieved through sophisticated techniques as the malware can search and harvest information using dynamic web techniques and content is stolen through Ajax calls. In order to stay protected, Facebook users need to update the software and avoid downloading from unfamiliar sites while only preferring to download apps from trusted sources. Moreover, be cautious about the permissions requested by the apps. It is also important to install a decent enough mobile security application like Norton and keep data securely backed up at all times.