Over 500,000 Android users targeted by phishing apps harvesting their Facebook credentials. ESET detects these trojans as Android/Spy.Feabme.A.
Over 500,000 Android users targeted by phishing apps harvesting their Facebook credentials. ESET detects these trojans as Android/Spy.Feabme.A
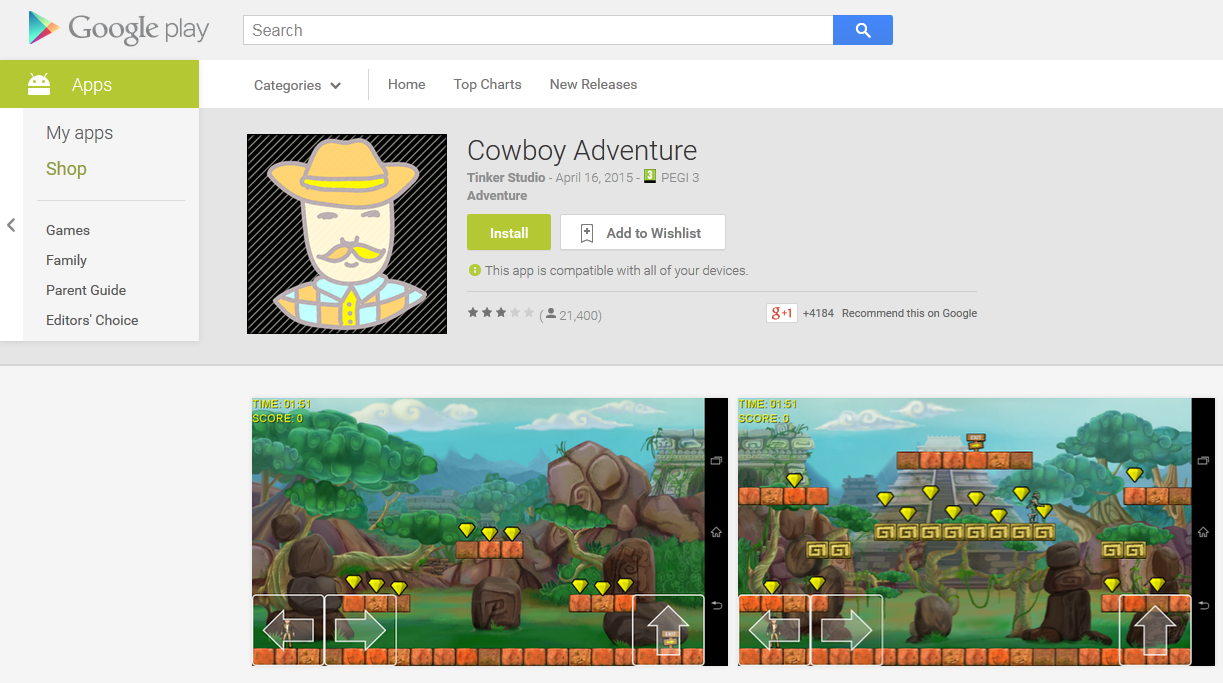
With 500,000 – 1,000,000 installs, Cowboy Adventure was a relatively popular game on the Google Play store. That popularity in itself is unremarkable: however, the developers of the app also used it as a tool to harvest Facebook credentials, and that did raise a few eyebrows. It was one of two games spotted by ESET malware researchers that contained this malicious functionality, the other one being Jump Chess.
Unlike some other Android malware, these apps did contain legitimate functionality (they actually were real games) in addition to the fraud. The problem lies in the fact that when the app is launched, a fake Facebook login window is displayed to the user. If victims fell for the scam, their Facebook credentials would be sent to the attackers’ server.

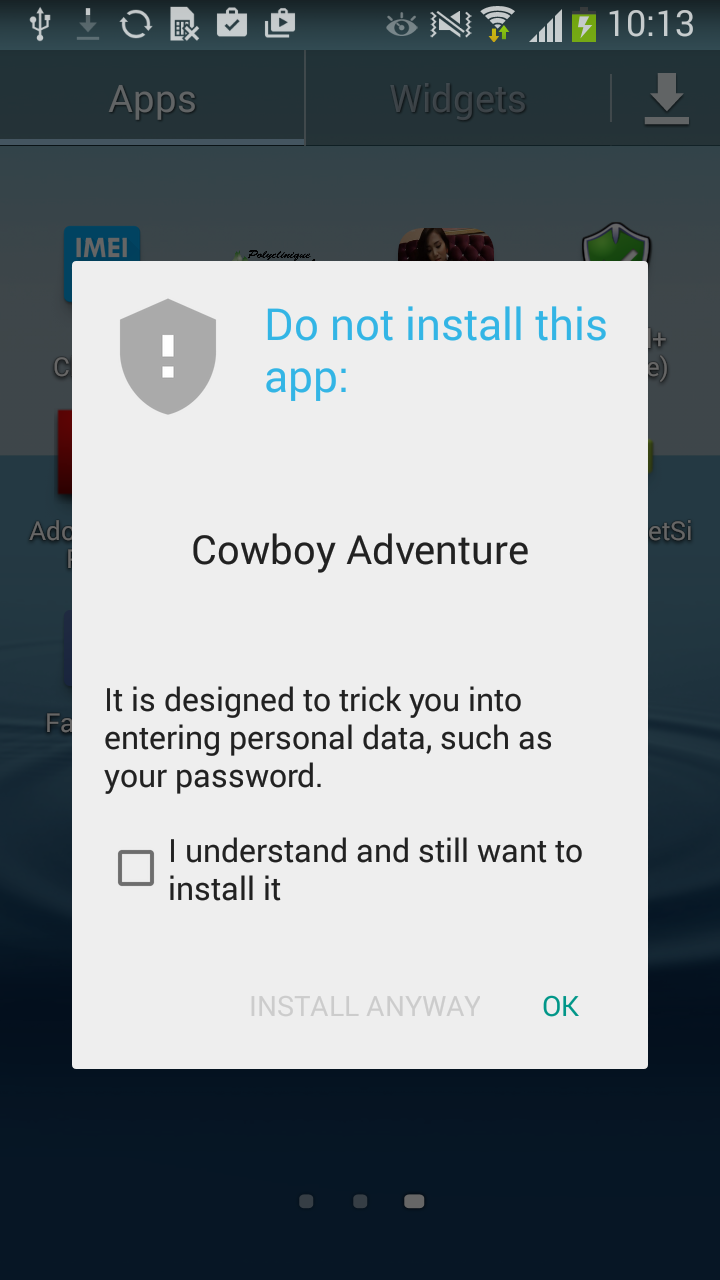
That was the bad news. The latest version of Cowboy Adventure at the time Google took it down from their official market last week was 1.3. This trojanized game had been available for download from Google Play since at least April 16, 2015, when the app was updated. We are not sure how many users had their Facebook credentials compromised.
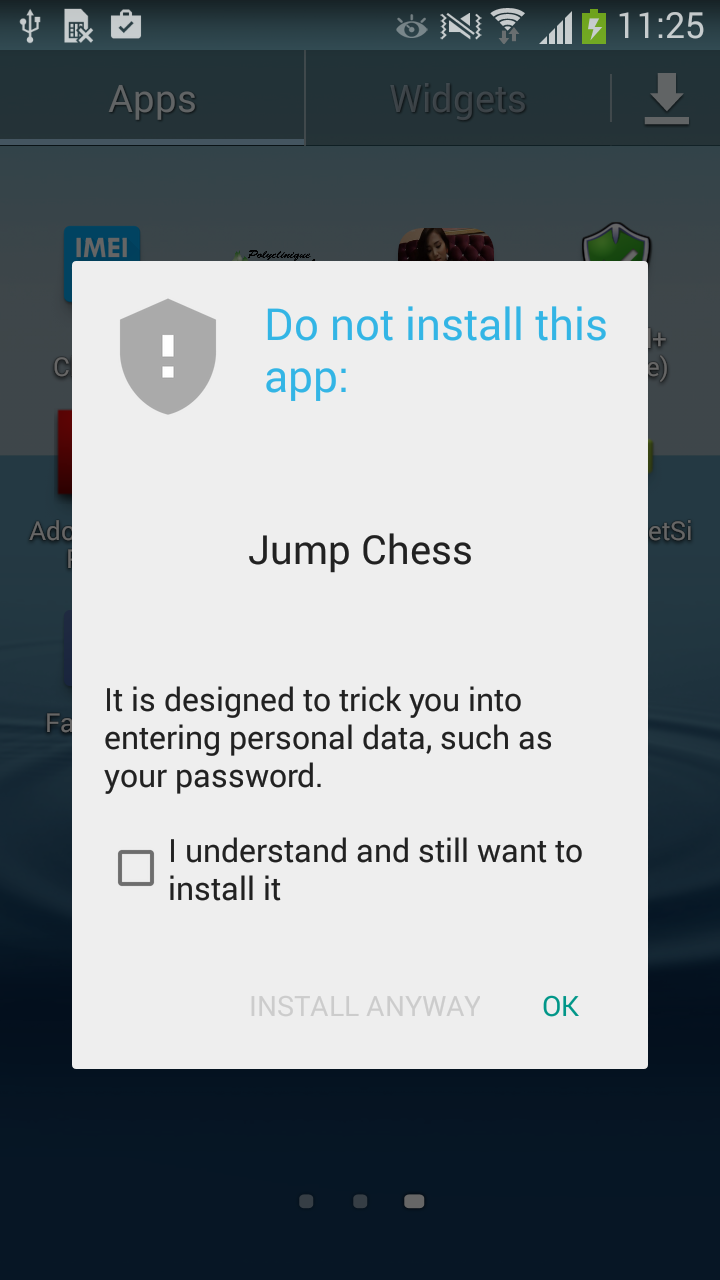
Jump Chess – from the same developer – had been available for download since April 14, 2015, but fortunately it was less successful than Cowboy Adventure, with only 1,000 – 5,000 installs.
The good news is that Google has taken down both of the apps from their app store and also warns against their installation on Android devices:
Google’s security mechanisms have been improving, which has lowered the risk of getting infected by malware for Android users.
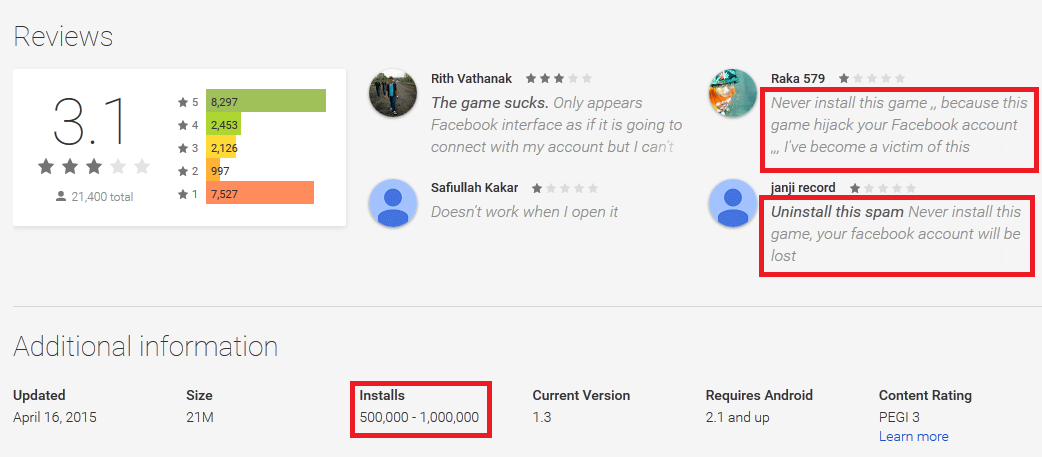
Another piece of good news is that even though the number of potential victims may have been up to one million, there were many of them who were not tricked by the scam. They expressed their negative opinions in the user comments for the app:
Our analysis of these malicious games has shown that the applications were written in C# using the Mono Framework. The phishing code is located inside TinkerAccountLibrary.dll. The app communicates with its C&C server through HTTPS and the address to which to send the harvested credentials (also known as the ‘drop zone’) is loaded from the server dynamically.
This example of Android malware reminds us of a few basic principles that help us to stay safe when using Google’s mobile platform:
- Always favor downloading apps from the official Google Play store rather than from alternative app stores or other unknown sources. Even though Google Play is not 100% malware free, they do have strong security mechanisms to keep trojans out.
- Download apps only from trustworthy app developers and always check the ratings and user comments. The scam behavior of Cowboy Adventure was quickly noticed by users. Also take a minute to review the permissions that an app is asking for during installation.
- Don’t underestimate the necessity for an anti-malware scanner on your Android phone. ESET Mobile Security detects the malicious games as Android/Spy.Feabme.A.
Malware Analysis by: Lukáš Štefanko
Update: After proofing, as this article was on its way to press, we discovered that Trustlook also published their analysis of this trojan yesterday. Check out their blog post for interesting additional technical details.