Researchers discovered an ongoing malware campaign that believed to be operating by a Chinese based threat group called “Mustang Panda” that targets public and private sectors around the world.
Mustang Panda threat group activities initially observed in June 2018, since then attackers improved their campaign activities with unique Tactics, Techniques, and Procedures (TTPs).
Various targets are focused on this new campaign that includes the Non-profit China Center, Vietnam political party, Southeast Asia residents and the different countries such as Germany, Mongolia, Myanmar (Burma), Pakistan, Vietnam.
Threat actors compromising the targeting with the help of weaponized PDF and word documents that drops via spear-phishing email with VBScript embedded in the “.lnk” file.
Different type of decoy documents was used in this campaign for each and every target based on the infection possibilities and compromised the victims to open it using various social engineering techniques.
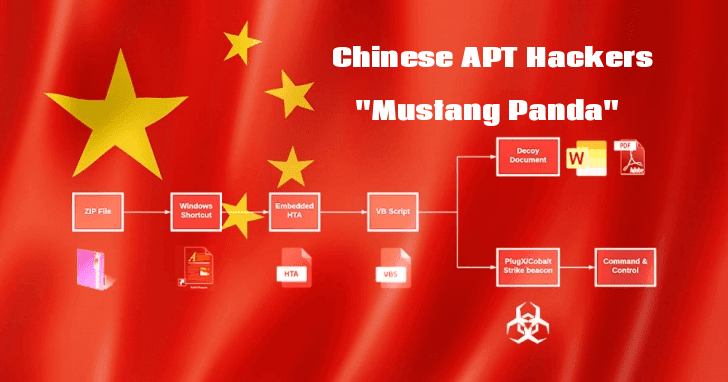
Mustang Panda APT Infection Chain
The initial stage of infection starts by delivering the zip file that contains a “.lnk” (Windows Shortcut) file and convinces the victims to open the file by utilization of a double extension trick.
A file called .lnk contains an HTA (HTML Application) with embedded VBScript that drops the main payload of the infection, which is either PlugX and Cobalt Strike payloads or malicious PDF, word documents.

Researchers from anomali found “similarities in targeting in Mongolia and an NGO. The use of United Nations’ documents regarding activities in the Middle East may also be indicative of think-tank targeting. Furthermore, the use of PlugX malware also aligns with CrowdStrike’s previous findings of activity attributed to Mustang Panda”
There is no clear indication of the distribution method used by Mustang Panda threat groups, but the researchers believe that they are using spearphishing emails to implant the malware into the targeted system.
Researchers uncovered nearly 15 malicious documents that utilized by Mustang Panda in this current ongoing campaign.
“Further analysis of the files led to the identification of other “.lnk” files that were attempting to infect individuals with a Cobalt Strike Beacon (penetration-testing tool) or PlugX (Remote Access Tool (RAT)”
This kind of malicious activity sponsored by China will likely continue as the country expands its efforts for the ongoing Belt and Road Initiative that seeks to invest in infrastructure in over 100 countries, anomali concluded.
You can also read the complete malware analysis tutorials.
Indicator of Compromise