ObliqueRAT is a remote access Trojan (RAT) active at least since mid-2020, identified in multiple attacks against organizations in South Asia and constantly evolving. Cybersecurity experts mention that the operators of these attacks have found a new attack mechanism, hiding the Trojan in seemingly harmless images posted on compromised websites.
When first discovered, the cybersecurity community described ObliqueRAT as a conventional Trojan for data theft, connection to a C&C server and the ability to terminate its own processes. ObliqueRAT is also able to look for clues that would follow that the target system runs in an isolated environment, one of the main cybersecurity practices for detecting malicious developments.
The developers of this RAT have continued a complex update work since the malware was detected, adding new techniques and abusing a large set of possible attack vectors. Recently, Cisco Talos researchers published research on ObloqueRAT, mentioning that Trojan operators are deploying a new campaign through an unusual attack involving the use of images in various formats.
In previous attacks, hackers used Microsoft Office documents sent by email in phishing campaigns. Talos mentions that, in the most recent attacks, hackers use malicious documents to redirect victims to compromised websites in order to bypass email security controls.
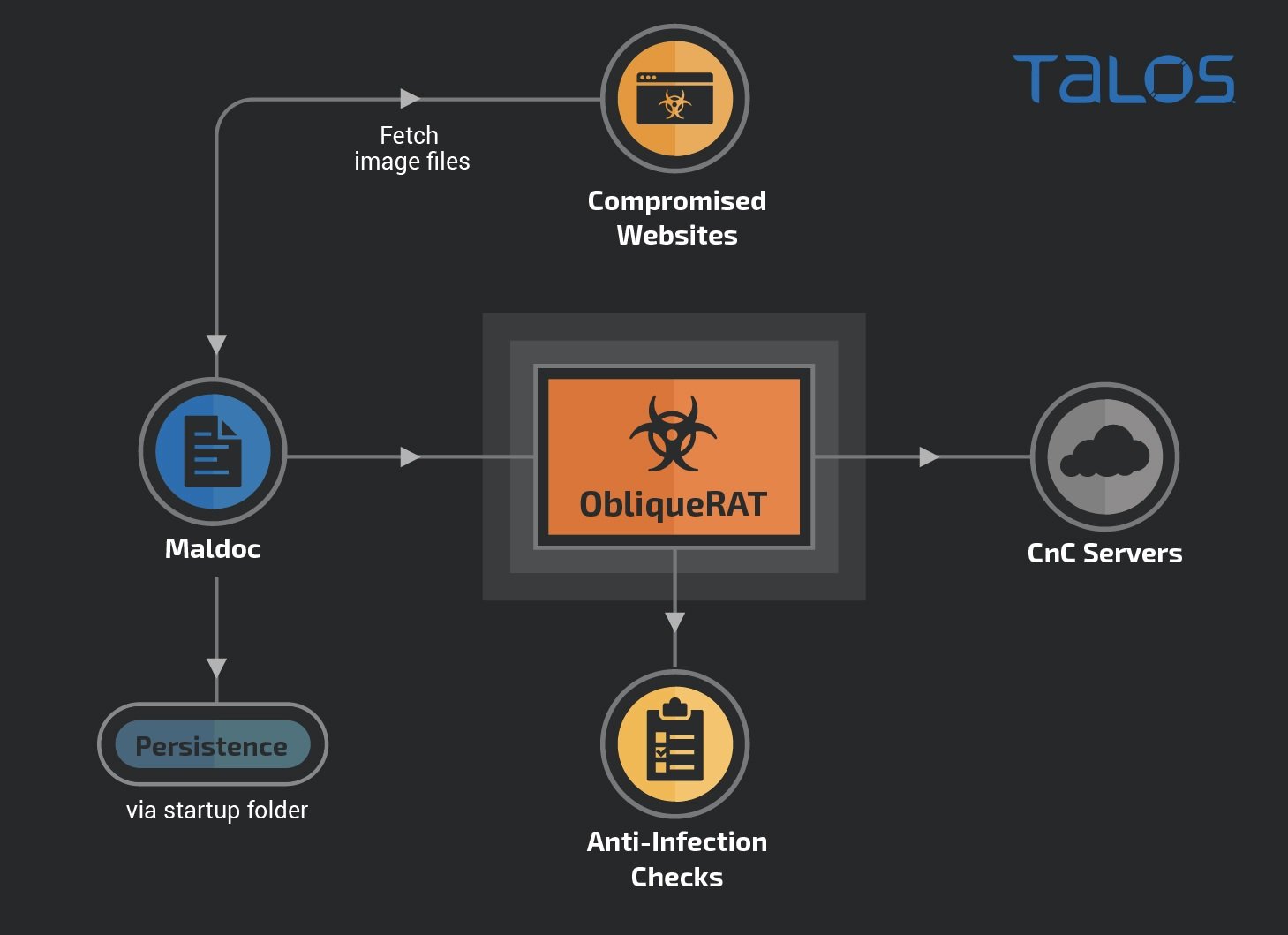
The attack involves a technique known as steganography, which involves hiding code, files, images and videos within files in other formats (in this case, .BMP files). Although these files contain legitimate data, executable bytes are also hidden in RGB data that triggers the download of a .ZIP file containing ObliqueRAT.
Experts mention that the malicious macros used by hackers extract the storage file and deploy the Trojan to the target endpoint. Since the end of 2020, specialists have detected at least four new improved versions of malware, allegedly developed between April and November last year. Improvements include endpoint checks and locked computer names, as well as the inclusion of external storage file extraction capabilities. A new command prompt, not yet unassigned, also indicates that additional updates will occur in the future.
Finally, experts mention that ObliqueRAT could be linked to the Distribution Campaigns of the CrimsonRAT Trojan, as there are potential links with Transparent Tribe, a hacking group specializing in attacking countries’ technology infrastructure in the East.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















