Although they are not uncommon, network security specialists mention that the security risks present in Linux systems are not known broadly enough. Either because of its little offensive nature or because the security mechanisms of these systems overlook them, these security threats do not receive as much diffusion as those that impact Windows systems.
However, it has become something common to
detect malware with highly developed evasion capabilities using existing open
source present in some implementations beyond Windows systems. The Intezer
network security firm has recently reported the finding of a new malware
variant known as HiddenWasp.
According to the company’s specialists,
HiddenWasp is a cybersecurity threat that must be addressed, since after some
analysis, it has been concluded that it has a detection rate of 0% in the most
widely used malware detection systems in the world.
According to network security experts, the
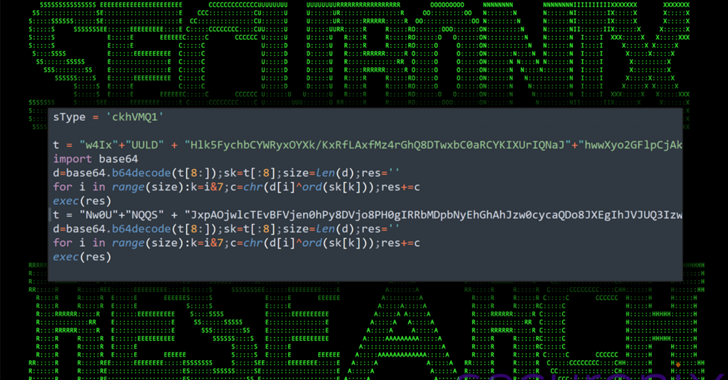
Linux HiddenWasp malware infection requires the execution of an initial script.
In the research, experts discovered that the script depends on the use of a
user called ‘sftp’ with a fairly secure password; in addition, the script
cleans the system to get rid of previous versions of the malware in case an
infection had occurred earlier.
Subsequently, a file is downloaded to the compromised
machine from the server containing all components, including the Trojan and
rootkit. The script also adds a Trojan binary to the/etc/rc.local location to
work even after reboot on the system.
The specialists from the International
Institute of Cyber Security (IICS) have found several similarities between the
rootkit of HiddenWasp and the malware Azazel, in addition to sharing some
string fragments with the malware ChinaZ and the Mirai
botnet. “Thanks to HiddenWasp, hackers can run commands on the Linux
terminal, run files, download additional scripts, and more”, the experts added.
Although the research achieved some findings,
experts still do not know the attack vector used by hackers to infect the Linux
systems, although a possible way is that the attackers have deployed the
malware from some systems that are already under their control. “HiddenWasp
could be a second stage of another attack”, the experts concluded.