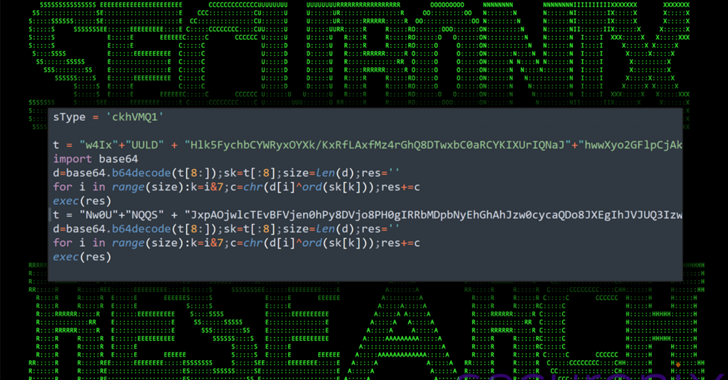
Linux is considered a more secure and privacy-focused operating system than Windows, not only because of a low market share (only 2% of all installed desktop operating system) but also due to its very architecture that is patterned after Unix. However, a device cannot approach absolute security while also connected to the Internet, that in itself is a contradiction of terms, this is regardless of the operating system used. Intezer Labs, represented by its security researchers, Ignacio Sanmillan has revealed that a malware named as HiddenWasp specifically designed to target Linux machines, infecting its victims with a rootkit-like process. Chinese hacker group used a malware named Winnti to perform the same attack against Linux previously, which made Sanmillan accuse HiddenWasp as a creation of the same group.
“We found some of the environment variables used in an open-source rootkit known as Azazel. In addition, we also see a high rate of shared strings with other known ChinaZ malware, reinforcing the possibility that actors behind HiddenWasp may have integrated and modified some MD5 implementation from [the] Elknot [malware] that could have been shared in Chinese hacking forums,” explained Sanmillan.
Intezer Labs researchers investigated the Adore-ng rootkit, it is an open source software which a certain portion of the code was used for Mirai malware previously. A small portion of the rootkit properties is similar to Azazel rootkit. HiddenWasp contains a rootkit component that closely resembles Adore-ng. “We observed that [the HiddenWasp] files were uploaded to VirusTotal using a path containing the name of a Chinese-based forensics company known as Shen Zhou Wang Yun Information Technology Co., Ltd. Furthermore, the malware implants seem to be hosted in servers from a physical server hosting company known as ThinkDream located in Hong Kong,” added Sanmillan.
As of this writing, Sanmillan’s team is still not aware of what the Chinese group is behind the development of the malware. It takes a lot of effort to infect a Linux system, as the user requires typing the root password in order to install software deep into the system. Since the user has no root access by default in a Linux system, all HiddenWasp can do is install its rootkit component as a user-level process. The team continues to investigate the malware, as the component of the second payload is not yet known, but most probably it has something to do with the RAT-module for HiddenWasp.
“Unfortunately, I don’t know what is the initial infection vector. Based on our research, it seems most likely that this malware was used in compromised systems already controlled by the attacker. From our research, it looks like an implant from a targeted attack. It’s hard to say if it’s used by [a] nation-sponsored attacker or someone else, but it is definitely not the usual DDOS/mining malware for quick profits,” concluded Sanmillan.
Intezer has published a comprehensive article in their official blog detailing the minute-to-minute operations of HiddenWasp the moment it arrives in a vulnerable Linux installation. The open source nature of Linux being matched by a somewhat “open source” malware in HiddenWasm may start a new trend of having an open source version of malware targeting Linux hosts.
Also, Read:
5 Ways to Safeguard yourself from Linux Malware
What is Linux Malware? Here’s what you need to know about it
The Best 10 Linux Distro for Penetration Testing
Trickbot, Fast Becoming the Malware Of The Year?
Nasty Side-Channel Attack Vulnerability (Again) In Windows & Linux Discovered